Containerization and Security

Containerization is not only an exciting foundation of DevOps; it is also an answer to several critical operational issues.
For developers, building software once, packaging it and running it anywhere regardless of library versions, dependencies, or underlying hardware and operating system has been a challenge.
For operations staff, setting up an environment that can run any new application consistently is reassuring, so that when the application goes into production, the system is reliable and can be trusted to run smoothly.
For production staff, implementing a new package easily is a huge time saver.
For all these professionals, containers are helping a dream become a reality.
What are containers?
Containers are lightweight, portable software packages with everything needed at runtime
While containers are a hot topic, they are not new. Docker is arguably the company that launched the current container market. But container technology has been with us for several years, principally in Linux as LXC. Containers are lightweight, portable software packages with everything needed at runtime: code, system tools, and libraries. While containers are similar to virtual machines (VMs), they are much smaller and more efficient. Along with the application itself, a VM includes the overhead of the entire guest operating system, binaries and libraries, and it requires a hypervisor for management on a server. A container is a much lighter weight package (think of twenty megabytes instead of twenty gigabytes); it shares the operating system kernel via API calls with other containers on a host. Containers are a means of consistently moving and deploying applications into different environments, because a container includes the entire runtime environment needed for the application – libraries, dependencies, configuration files, etc. – eliminating the differences in OS distributions and guaranteeing that the software will always run the same, regardless of the environment.
The benefits of containers
Not only are containers small and efficient, but they are also highly dynamic. They can start up or shut down quickly. They can run for just hours or for days. They can be deleted and replaced.
Containers are increasingly being used for web services, such as Google Apps. Containers make it easy to develop web apps that are composed of hundreds of microservices, replacing a monolithic backend. Microservices accelerate development by separating functionality for efficiency and maintainability.
Containerization provides isolation for microservices from other processes, a lightweight deployment mechanism, a stateless package, and the ability to build and rebuild services on the fly. Containers contribute to easier and quicker application delivery, and faster and more reliable deployment. Hundreds of containers can be run on just one server, saving valuable data center budget. Docker containers can run on virtually any computer, infrastructure, or cloud. Container management is therefore much less painful for operators.
Container security
Infosec professionals generally consider containers less secure than VMs
But because containers are not isolated from one another to the same degree that virtual machines on a shared host are, and because containers are usually not scanned for vulnerabilities before or after being deployed to production, infosec professionals generally consider containers less secure than VMs. A vulnerability in a shared OS kernel can potentially provide a way into a container. Active scans can miss most of them. Containers also typically don’t include the SSH daemon, so credentialed scans don’t work with most containers. Microservices and containers can introduce hundreds of endpoints and erode the visibility of security risks.
Tenable has been addressing container security since early 2016, with Nessus offering the ability to detect running Docker hosts and the containers running on them. Nessus can also audit Docker hosts against the CIS Docker v1.6+ benchmark to help harden container hosts. Discovering and securing Docker hosts is an important first step, but it’s not enough. Without comprehensive, continuous monitoring, you may not be able to see and assess all container configurations and instances. A new kind of security solution is needed.
Tenable now offers a better approach to container security
Because containers are rebuilt on the fly and exist for short periods of time, organizations have struggled to continuously assess Docker containers and similar environments for vulnerabilities. Tenable now offers a better approach to container security – a solution that monitors container images for vulnerabilities during the development lifecycle, before deployment, to ensure containers are vulnerability-free in production.
The recent acquisition of FlawCheck, the leader in container security, enables Tenable to deliver innovative technology to organizations that want to integrate security into their build pipeline. This helps provide a real-time view of their CI/CD (continuous integration and continuous deployment) environments for vulnerability and malware detection in Docker container images.
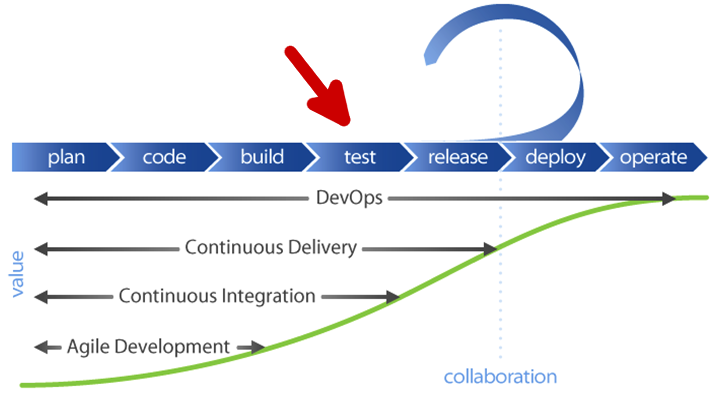
FlawCheck scans container images for vulnerabilities and provides continuous monitoring early in the DevOps lifecycle. An application need not be running to be discovered and scanned; the container image for that app is stored and scanned, providing timely security assurance before an application or service is launched.
FlawCheck revolutionizes DevOps security
For organizations with large development teams, FlawCheck revolutionizes DevOps security, moving security into the development pipeline for real-time on-the-fly security auditing. Security is baked into containers before they are ever deployed onto networks.
For more information
- Read more about FlawCheck
- Sign up for a free trial of FlawCheck
- Container security



