BYOD Auditing, Tenable Style
Note: Passive Vulnerability Scanner (PVS) is now Nessus Network Monitor. To learn more about this application and its latest capabilities, visit the Nessus Network Monitor web page.
The recent release of SecurityCenter 4.7 allows organizations to combine network monitoring and MDM auditing to discover and audit all mobile devices in use, regardless if they are being managed, only used for email, or are connected directly to the network.
Tenable accomplishes this with two different technologies – Nessus and the Passive Vulnerability Scanner.
Nessus supports discovery of mobile users, devices, and vulnerabilities through integration with Active Directory, Good for Enterprise, and Apple’s Profile Manager. SecurityCenter users can now leverage this information for reporting, dashboards, and analytics to identify risky mobile users and devices.
Below is a screen shot of mobile vulnerability data shown on a SecurityCenter dashboard:
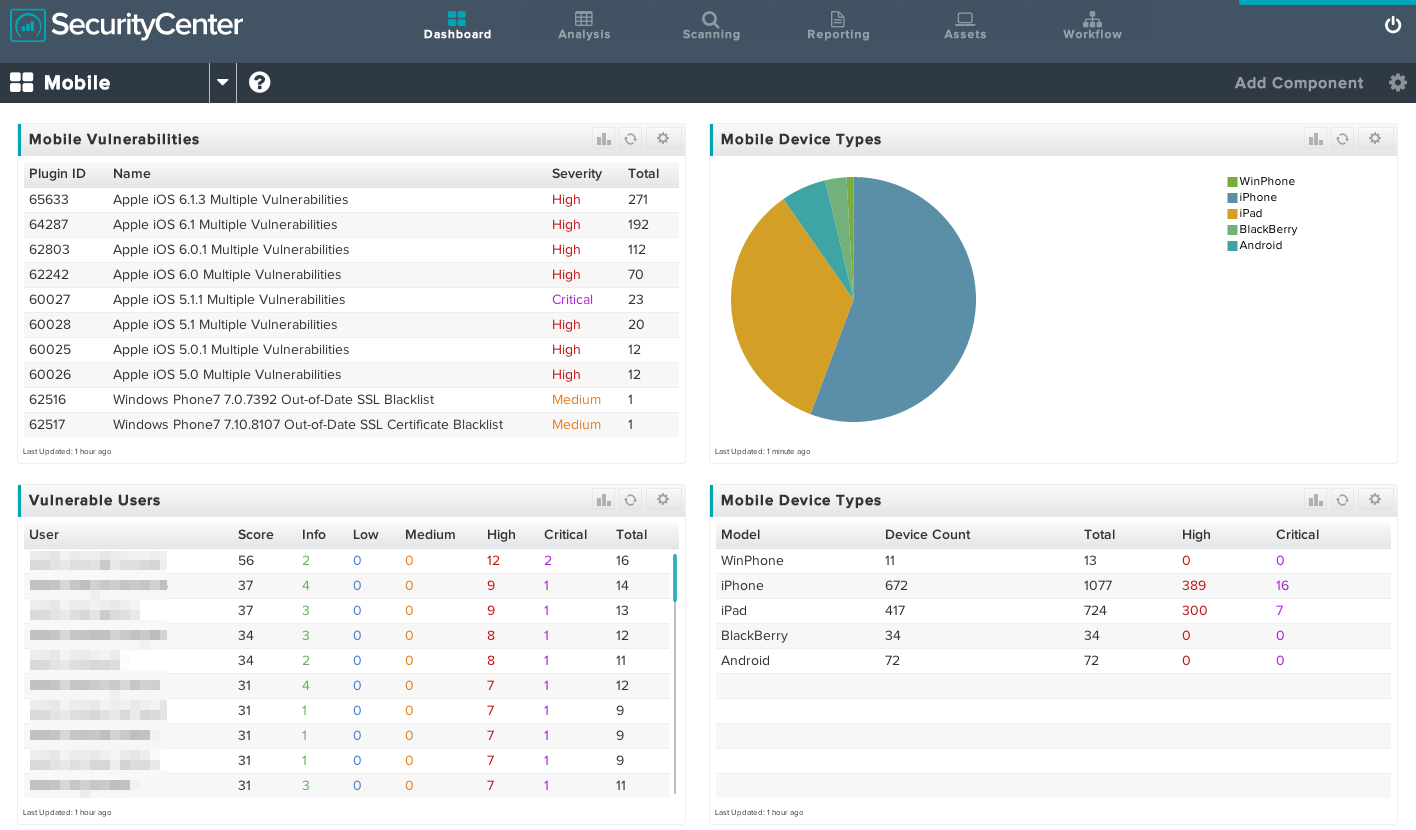
This dashboard shows a list of mobile vulnerabilities ranked by their criticality and prevalence, a pie chart of detected mobile device types, a list of mobile users (sanitized) ranked by number of vulnerabilities, and a list of mobile device types with the number of high and critical vulnerabilities associated with each. This is a tremendous amount of information pertaining to mobile devices that have accessed your network email through Active Directory authentication, or from your MDM.
SecurityCenter also supports mobile device vulnerabilities discovered by the Passive Vulnerability Scanner (PVS). These vulnerabilities are obtained from PVS deployments that are watching network traffic. PVS can identify all major mobile devices, as well as a wide variety of their vulnerabilities and popular applications like DropBox.
Below is a screen shot of passively detected mobile security issues:
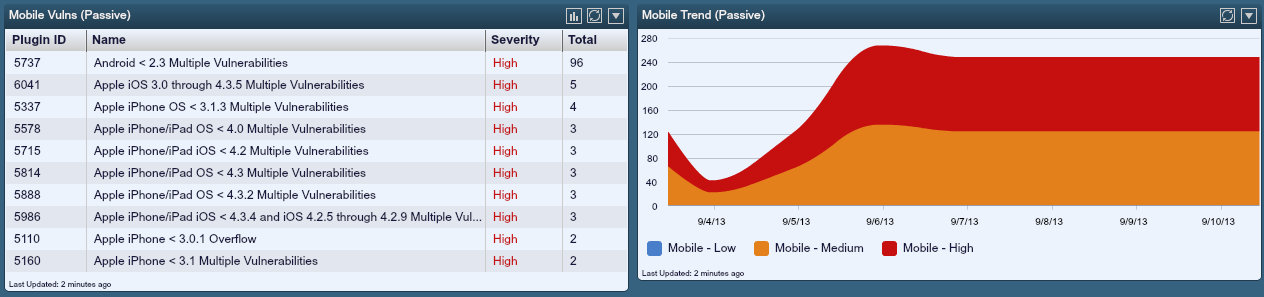
In this dashboard, the specific number of mobile device vulnerabilities currently active on the network is listed, as well as a seven-day trend of all mobile vulnerabilities observed by PVS.
Leveraging Nessus and PVS for mobile device discovery and auditing is significant for several use cases.
For organizations that allow their users to receive email on personal devices, Nessus audits of MDM and Active Directory installations easily identify security issues associated with these mobile devices. These vulnerabilities are often overlooked in the BYOD (Bring Your Own Device) discussion, because they aren’t “brought” to work or plugged into the network. They are personal devices that may or may not be managed, but they are on home and carrier 3G/4G networks. Traditional scanning, network access control, or sniffing won’t see these devices because they aren’t “on” the network.
For organizations that have mobile devices connected internally, passive discovery is an excellent continuous mechanism for discovery and internal monitoring. The larger a network is, the easier it is for an IT group to grant mobile devices access to wireless networks and areas not secured with network access control.
Leveraging active and passive network monitoring under the SecurityCenter platform ensures that you know how many mobile devices are on your network, and what risks they are bringing with them.
Each of these techniques can be combined into a single dashboard. Below is a screen shot of such a dashboard combining both passive network discovery of mobile security issues with audit results from an MDM.
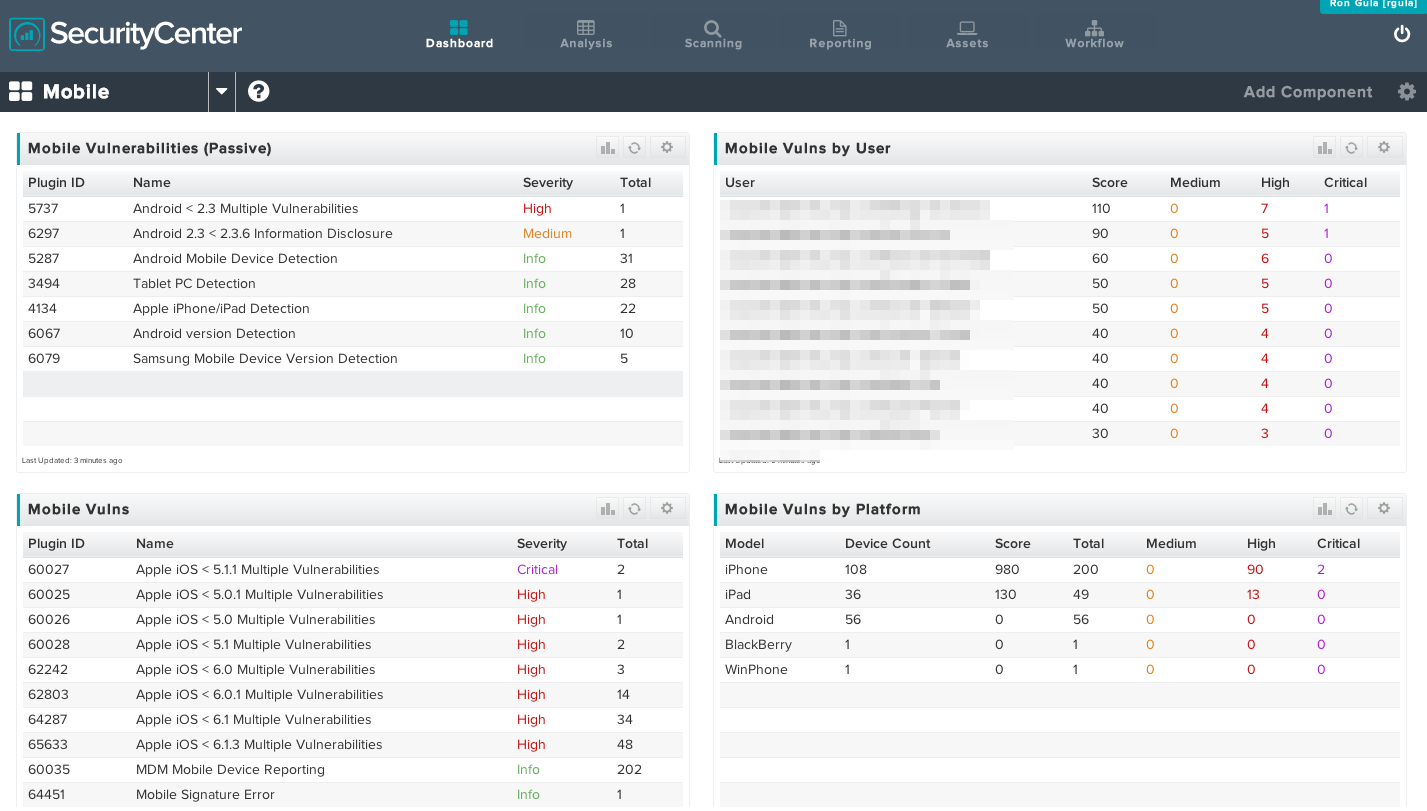
In this particular dashboard, which has had the user names sanitized, it is interesting to note that PVS has discovered about 70 mobile devices, while direct Nessus auditing has found several hundred.
To learn more about Tenable’s approach to monitoring mobile risks to your network, please visit our Mobile Device Security page.
- BYOD
- Dashboards
- Mobile Security
- Nessus
- Nessus Network Monitor
- SecurityCenter


