Auditing Patch Management Solutions with Tenable.io
We receive many questions from customers on how to configure scans to audit their patch management solutions. Whether you have a few hundred or several thousand systems, patch management solutions provide one of the easiest ways to maintain integrity and stability of systems within your network. Unfortunately, no matter what type of solution you are using, or how often you are patching your systems, patches can still fail for a variety of reasons. Issues such as managed clients failing to synchronize, systems offline during a patch cycle, group policy issues and other misconfigurations can leave your systems at risk. Using Tenable.io patch management integrations provides you with an effective way to compare vulnerability results and monitor patch management efforts across the enterprise.
Many organizations use Microsoft’s Windows Server Update Service (WSUS) and System Center Configuration Manager (SCCM) to manage and deploy patches. WSUS is Microsoft’s built-in patch management service that enables organizations to automatically patch vulnerabilities on Windows systems. Organizations often use SCCM to deploy software, monitor systems, and manage devices within the enterprise. SCCM integrates with WSUS by providing more control over scheduling and deployment of patches.
Creating Scans
To audit your patch management solution using Tenable.io, start by selecting the Advanced Scan template. Under the Credentials tab, click on Patch Management, then select the desired Patch Management solution. Enter the IP address of your server along with an administrative account that has access to the patch management server.
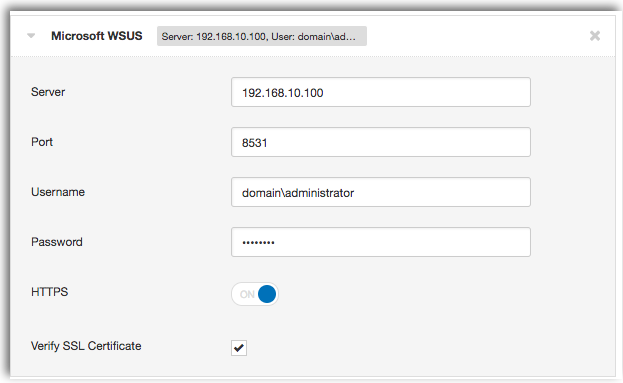
Tenable.io only requires patch management credentials to be entered into your scan, so you don’t need to add local credentials for your managed hosts. This option is useful for larger organizations where credentials for managed hosts may not be available. Vulnerability data is collected from the selected patch management solution, and will return a list of outstanding patches that you need to install.
To get a complete look at your patch management solution, we recommend adding credentials for your managed hosts. Nessus will scan each individual host and compare the information being reported by your patch management solution.
Whether you are auditing your WSUS or SCCM server, there are several plugins that need to be enabled within your scan in order to see results. In addition, you will also need to enable the Windows : Microsoft Bulletins Plugin family.
Required SCCM Plugins
- Patch Management: SCCM Server Settings (Plugin ID 57029)
- Patch Management: Missing updates from SCCM (Plugin ID 57030)
- Patch Management: SCCM Computer Info Initialization (Plugin ID 73636)
- Patch Management: SCCM Report (Plugin ID 58186)
- Windows : Microsoft Bulletins Plugin family
Required WSUS Plugins
- Patch Management: WSUS Server Settings (Plugin ID 57031)
- Patch Management: Missing updates from WSUS (Plugin ID 57032)
- Patch Management: WSUS Report (Plugin ID 58133)
- Windows : Microsoft Bulletins Plugin family
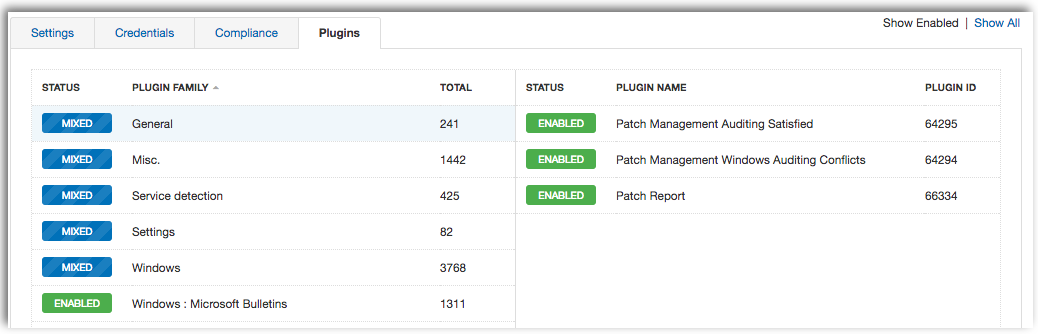
If you have added credentials for your managed hosts into your scan, using the Patch Management Windows Auditing Conflicts plugin will help you quickly detect any patch conflicts being reported. The Patch Report plugin will report on vulnerabilities from third-party software that may not be covered by your existing patch management solution. Enabling the optional plugins will provide valuable information on client versions deployed within your network.
Recommended Plugins
- Patch Management Windows Auditing Conflicts (Plugin ID 64294)
- Patch Management Auditing Satisfied (Plugin ID 64295)
- Patch Report (Plugin ID 66334)
Optional Plugins
- Microsoft SMS/SCCM Installed (Plugin ID 62028)
- Microsoft System Center Configuration Manager Client Installed Plugin ID (55532)
- Microsoft Windows SMB : WSUS Client Configured (Plugin ID 50859)
- Windows Server Update Services (WSUS) Detection (Plugin ID 20377)
Once you have selected the appropriate plugins, your output should look similar to the screenshot below.
Results
The patch management feature within Tenable.io enables you to collect information on missing patches reported by patch management solutions. Scan results will include a summary of Windows Bulletins collected from your patch management solution.
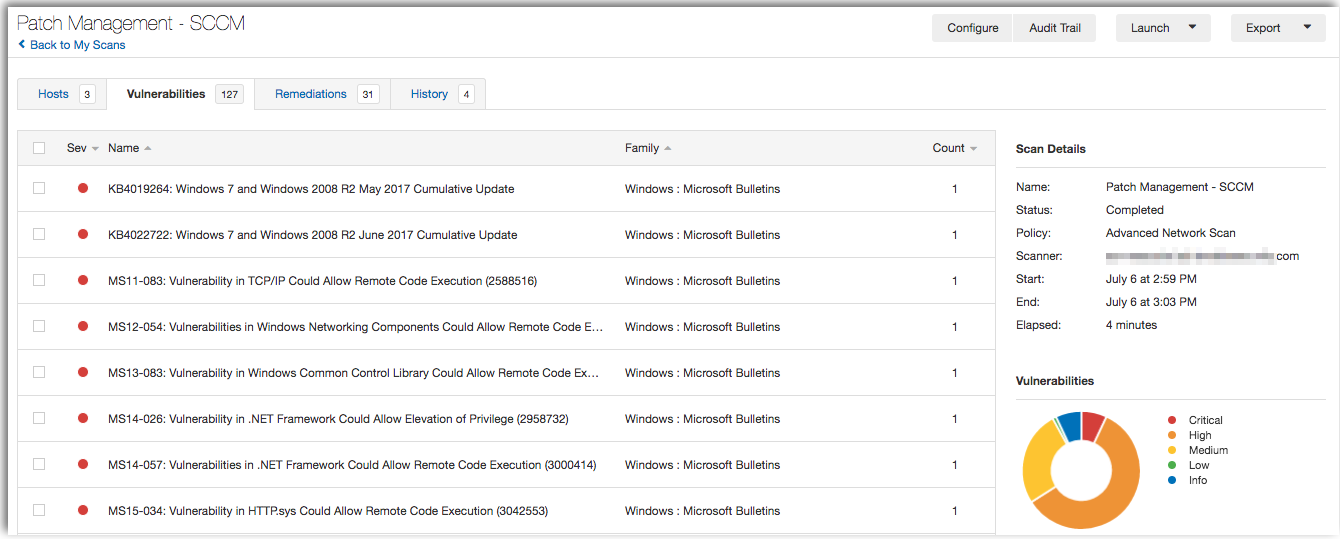
Vulnerabilities detected by your patch management solution includes a report on the affected hosts and whether the system is vulnerable. Using this information will help to ensure that your patch management software is configured properly and providing accurate information.
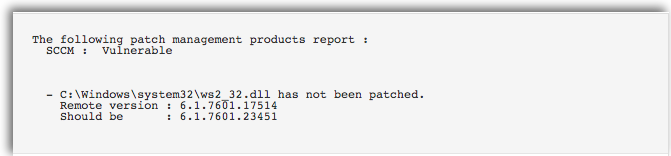
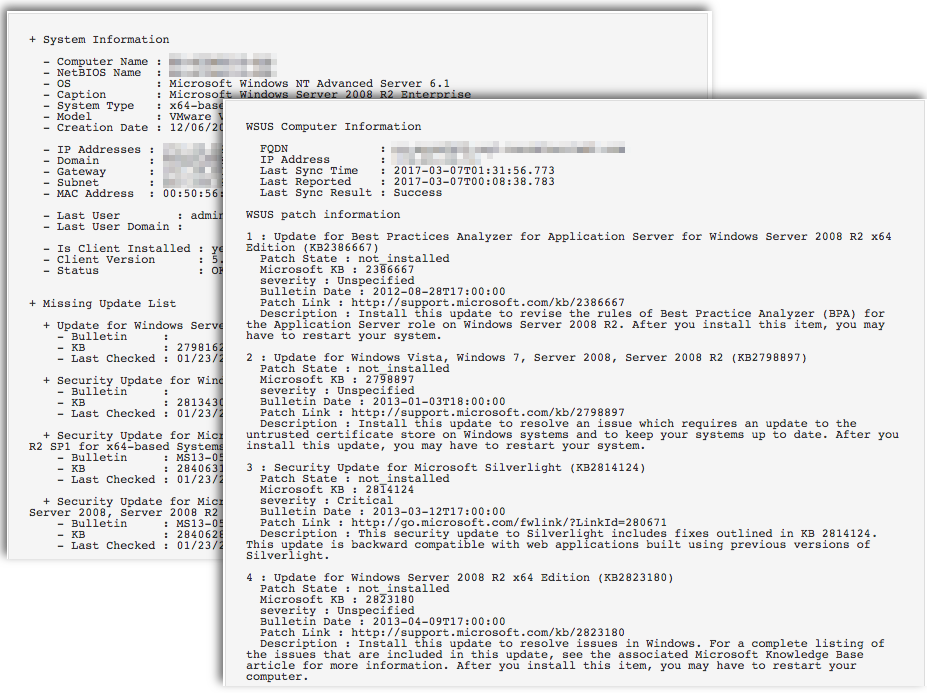
Results from the Patch Management: SCCM Report (Plugin ID 58186) and the Patch Management: WSUS Report (Plugin ID 58133) plugins will include a report on the status of managed agents, last sync timestamps, patch failures reported and any hosts that are up to date. This information will help you detect potential communication issues between the client and server, as well as any systems that may have fallen out of scope.
Conflicts
Using credentialed scans along with the Patch Management Windows Auditing Conflicts (Plugin ID 64294) plugin will report on any conflicts between Nessus and your patch management solution. If any conflicts are discovered, the plugin will use a “High” severity rating, and include a summary of the Microsoft Bulletins found.
Nessus uses the credentials provided within your scan to login to each managed host and compare the current patch level status. These results are compared to patch levels collected from SCCM by Nessus as indicated by “SCCM conflicts.”
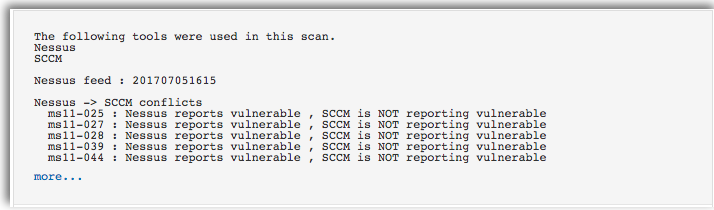
The report for each patch and the discrepancies are displayed in the plugin output. Conflicts like this may indicate that the host was not targeted for deployment of a particular patch, so the SCCM server does not detect it as missing.
The below example shows that SCCM is reporting the MS15-037 patch missing, however Nessus is reporting the system as not vulnerable. In this instance, SCCM may be reporting outdated or inaccurate data that should be addressed immediately by your security team.
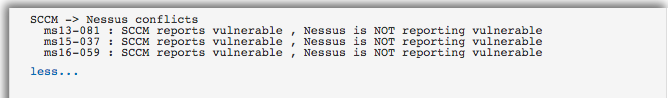
Using this data helps to underscore the importance of cross-referencing patches between what is on the system and what the patch management system thinks is on the system.
Wrap-Up
Using patch management integrations within Tenable.io helps you monitor patch cycles, improve remediation efforts, and strengthen your overall security posture. Start with your free 60-day trial of Tenable.io Vulnerability Management.
More Questions?
- Check out the Tenable.io for Microsoft SCCM How-To Guide.
- Continue the patch management conversation in the Tenable Community.
- Patch Auditing
- Tenable Vulnerability Management
- Tenable Vulnerability Management (DO NOT USE)
