by Cesar Navas
February 1, 2016
The Gramm-Leach-Biley Act (GLBA), also known as the Financial Modernization Act of 1999, is a federal law that governs the way financial institutions handle the private information of individuals. . GLBA compliance is mandatory. Safeguards must be in place to reduce risk and protect data integrity. This dashboard summarizes audit results as they relate to the controls described by the Federal Financial Institutions Examination Council’s (FFIEC) guidance on host level malicious code prevention for Section 501 (b) compliance of the Gramm-Leach-Bliley Act (GLBA).
The FFIEC guidance provided in their ‘Information Security Booklet’ for host level malicious code prevention includes controls for patch application, security-minded configurations, antivirus and the periodic auditing of host configurations. The booklet is a member of the FFIEC IT Examination Handbook series and provides coordinated guidance for GLBA Section 501(b) compliance. The booklet can be found in downloadable form at: http://ithandbook.ffiec.gov/it-booklets/information-security.aspx
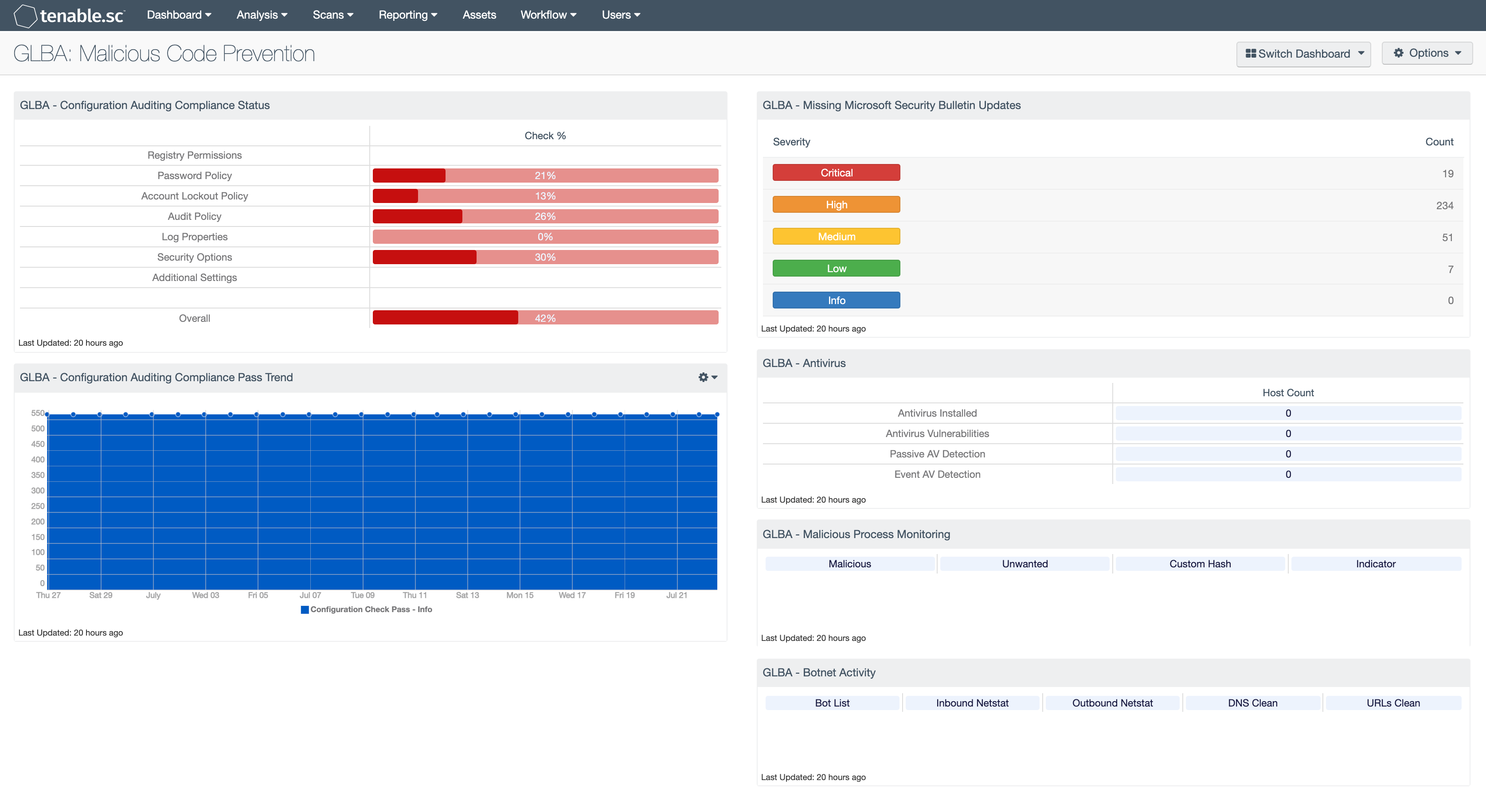
The Configuration Auditing Compliance components measure compliance using configuration check results as they relate to best practice configuration settings typically used within financial institutions for Microsoft platforms. The checks are executed by using Tenable Network Security's GLBA Windows System Audit file with Tenable Network Security's Nessus Vulnerability Scanner in conjunction with its agent-less compliance checks feature. The Pass Trend component data that is used for the area graph is produced by repetitive auditing and is automatically stored within Tenable's Tenable.sc central management console. Compliance results are grouped in the Pass Trend and Compliance Status components by policy families normally found within Windows Group Policy. These components can be removed if the audience of the dashboard prefers just an overall compliance status.
The Missing Microsoft Security Bulletin Updates dashboard component provides overall totals for missing security patches by severity. There are five severity ratings; which are Informational, Low Risk, Medium Risk, High Risk and Critical Risk. The ratings are derived from risk score ranges found within version 2 of the Common Vulnerability Scoring System (CVSS). The results are produced by Nessus agent-less credentialed scanning and/or through Nessus patch management integration.
The Antivirus dashboard component leverages the Nessus antivirus auditing plugins. For more information regarding the plugins please see the Tenable Blog post Auditing Anti-Virus Products with Nessus [https://www.tenable.com/blog/auditing-anti-virus-products-with-nessus]. As a relevant note, non-functioning host based antivirus is a potential indicator of malicious code infection.
The Malicious Process Monitoring and Botnet Activity dashboard components do not roll under the FFIEC guidance for host level controls for malicious code prevention. However, a single malicious code infection has the potential to lead to further infections. To learn more about the Malicious Process Monitoring and Botnet Activity dashboard component indicators please see comprehensive Indicators dashboard. This dashboard provides displays close to 100 different indicators of compromise and suspicious activity using Tenable.sc Continuous View.
If an analyst intends to run more Tenable configuration audits beyond the GLBA Windows System Audit for network appliances, applications and operating systems found within the organization consider using the Tenable.sc repository feature for segmenting results. The components used by the dashboard can be easily modified to filter by repository.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance and Configuration Assessment.
The dashboard requirements are:
- Tenable.sc 4.8.2
- Nessus 8.5.1
- NNM 6.0.0
- LCE 5.9.0
Tenable.sc Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new types of regulatory compliance configuration audits. Tenable.sc CV allows for the most comprehensive and integrated view of network health.
The dashboard contains the following components:
- GLBA Configuration Auditing Compliance Status - The pass trend data that is used for the area graph is produced by repetitive auditing and is automatically stored within Tenable's Tenable.sc central management console. Compliance results are grouped in the Status component by policy families, normally found within Windows Group Policy.
- GLBA Configuration Auditing Compliance Pass Trend - This component measures compliance using configuration check results as they relate to best practice configuration settings typically used within financial institutions for Microsoft platforms. The checks are executed by using Tenable Network Security's GLBA Windows System Audit file with Tenable Network Security's Nessus Vulnerability Scanner in conjunction with its agent-less compliance checks feature. The pass trend data that is used for the area graph is produced by repetitive auditing and is automatically stored within Tenable's Tenable.sc central management console.
- GLBA Missing Microsoft Security Bulletin Updates - This component provides overall totals for missing security patches by severity. There are five severity ratings which are Informational, Low Risk, Medium Risk, High Risk and Critical Risk. The ratings are derived from risk score ranges found within version 2 of the Common Vulnerability Scoring System (CVSS). The results are produced by Nessus agent-less credentialed scanning and/or through Nessus patch management integration.
- GLBA Antivirus - The Antivirus dashboard component leverages the Nessus antivirus auditing plugins to report known antivirus installations and identified vulnerabilities.
- GLBA Malicious Process Monitoring - This component does not roll under the FFIEC guidance for host level controls for malicious code prevention; however, a malicious code infection may lead to compromised systems and further infections.
- GLBA Botnet Activity - This component does not roll under the FFIEC guidance for host level controls for malicious code prevention; however, malicious activity from a botnet may lead to compromised systems and further infections.