Mind the Gap: A Closer Look at the Vulnerabilities Disclosed in 2022

This is the third of a four-part series examining the period of time between when a vulnerability is first discovered and when it is fully disclosed on the National Vulnerability Database. In this installment, we take a closer look at the vulnerabilities disclosed in 2022 — and discuss how Tenable can help.
It is necessary to look at the results of observation objectively, because you, the experimenter, might like one result better than another —Richard P. Feynman
There were 25,080 vulnerabilities disclosed in 2022, an 18.78% increase over 2021. Of these, 108 (0.43%) received a Tenable Vulnerability Priority Rating (VPR) of Critical, compared with 3,920 (15.63%) that received a Critical CVSS v3 score and 8,659 (34.53%) that received a High CVSS v3 score.
Of the vulnerabilities disclosed in 2022, 295 (1.2%) were observed to be exploitable before they were fully disclosed on the National Vulnerability Database (NVD).
While attackers can devote their time to monitoring CVE advisories ahead of their placement on NVD, most time-strapped cybersecurity practitioners have little choice but to rely on NVD as their primary source for vulnerability awareness.
Why does this matter? Because the time between when a vulnerability is first assigned a CVE on MITRE and when it’s analyzed and scored by NVD represents a critical blind spot for organizations. Attackers monitor advisories looking for vulnerabilities. This blind spot can increase the risk of a vulnerability being exploited by an attacker before the security professionals in an organization are even aware of it.
|
How vulnerabilities are rated: A common vulnerabilities and exposures (CVE) number is assigned by a CVE Naming Authority (CNA) when a vulnerability advisory is first published. The CVE database is managed by MITRE. While a CVE number can be reserved immediately upon publication of an advisory, a CNA must provide vulnerability details to MITRE before the flaw can be evaluated and assigned a score on the National Vulnerability Database (NVD). It can take weeks (or longer) from the time the CVE details are provided to MITRE to the time NVD analyzes the CVE and provides detailed information about it, including giving it a common vulnerability scoring system (CVSS) score. The gap in time between when a CVE is made public and appears in MITRE and when that CVE is fully disclosed on NVD creates blind spots for cybersecurity organizations. This study analyzes how that gap can increase cybersecurity risk in organizations. |
For the purposes of this blog, we examined the vulnerabilities disclosed between January and December, 2022, to assess the gaps between the time a vulnerability is first published and when it’s fully disclosed on NVD. We also explore historical trends and discuss how Tenable can help security teams close the gap.
We analyzed the vulnerabilities made public in 2022 based on the following criteria (see glossary for more details on each):
- How many vulnerabilities were covered in Tenable products prior to being fully disclosed on NVD.
- How many vulnerabilities were ranked as Critical or High by the Tenable VPR prior to being fully disclosed on NVD.
We began 2022 with Log4Shell, a vulnerability from the prior year, still making headlines as one of the worst security vulnerabilities of the last decade. The rest of the year didn’t disappoint, ushering in plenty of other critical vulnerabilities, including Follina and ProxyNotShell. As the vulnerability landscape continues to evolve, cybersecurity organizations face the daunting task of gathering accurate data, analyzing it and acting upon it to reduce risk.
Tenable Research is devoted to gathering a broad knowledge base of the vulnerability landscape. The team develops a wide range of insights and reporting capabilities for Tenable products. Our goal? To help security practitioners find and fix the vulnerabilities that matter most in their organizations and to do so in a timely fashion. To that end, this blog provides:
- Statistics on timelines and measures enacted by Tenable in order to fill in critical blind spots.
- A closer look at critical vulnerabilities that Tenable covered on a multitude of aspects — from awareness to prioritization coverage — ahead of NVD.
2022 lookback: Tenable plugin coverage ahead of NVD
With 25,080 new vulnerabilities disclosed in 2022, we looked at several indicators for Tenable plugin coverage prioritization. Tenable is aware of at least 565 public exploits for those vulnerabilities, constituting 2.25% of vulnerabilities with known exploitation to date. Tenable provided plugin coverage for 41 vulnerabilities mentioned in the CISA Known Exploited Vulnerabilities catalog before they were fully disclosed on NVD. Furthermore, Tenable provided plugins ahead of NVD for at least 96 vulnerabilities that had an available and observed exploit (see Fig. 1), of which 35 had a functional exploit, 15 had a high likelihood of exploit and 46 had an available Proof-of-Concept (PoC).
Fig. 1
Exploit maturity breakdown
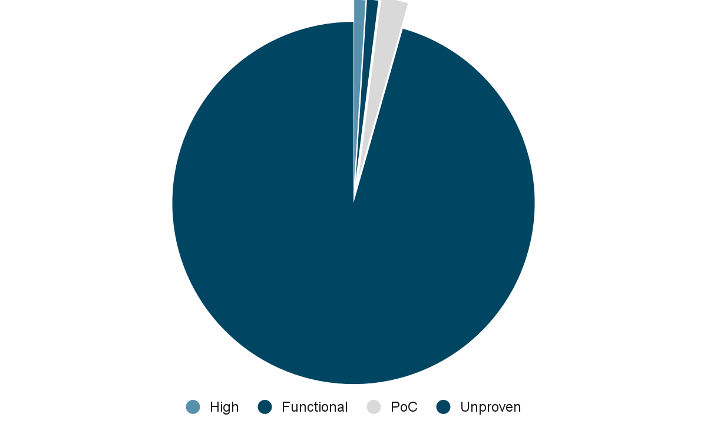
Source: Tenable Research, April 2023
Furthermore, as Fig. 2 shows, in 2022, Tenable provided plugin coverage for 30 vulnerabilities that received a VPR rating of Critical, 684 that received a VPR rating of High and 915 that received a VPR rating of Medium — all ahead of these vulnerabilities being fully disclosed on NVD. In addition, there were 556 CVEs that received a Low VPR score ahead of being fully disclosed on NVD.
Fig. 2
VPR ratings for 2022 CVEs
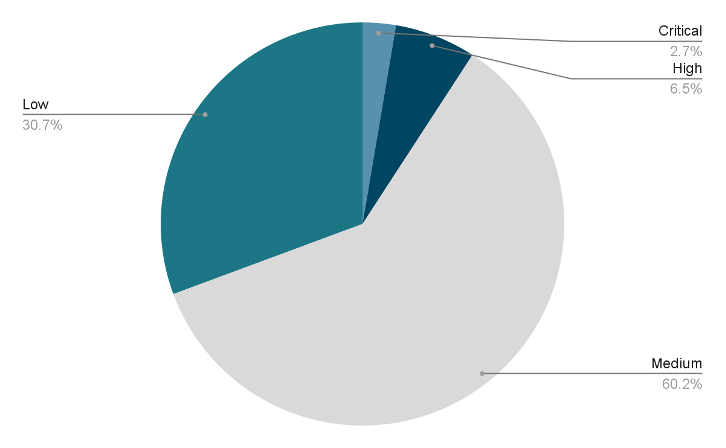
Source: Tenable Research, January 2023
Last, but not least, the Tenable Security Response Team (SRT) issued Cyber Exposure Alerts for 326 vulnerabilities.
VPR coverage ahead of NVD
In 2022, Tenable provided VPR scores for 1,801 vulnerabilities before they were fully disclosed on NVD. Thirty-one of the vulnerabilities that received a Tenable VPR score were mentioned in the CISA Known Exploited Vulnerabilities catalog. Furthermore, as Fig. 3 shows, in 2022, Tenable provided VPR scores ahead of full disclosure on NVD for at least 66 vulnerabilities that had an available and observed exploit, 26 of which had a functional exploit, 10 of which had a high likelihood of exploit and 30 of which had an available proof-of-concept (PoC). To our knowledge, 1,735 had an unproven exploit maturity.
Fig. 3
VPR coverage ahead of full disclosure on NVD
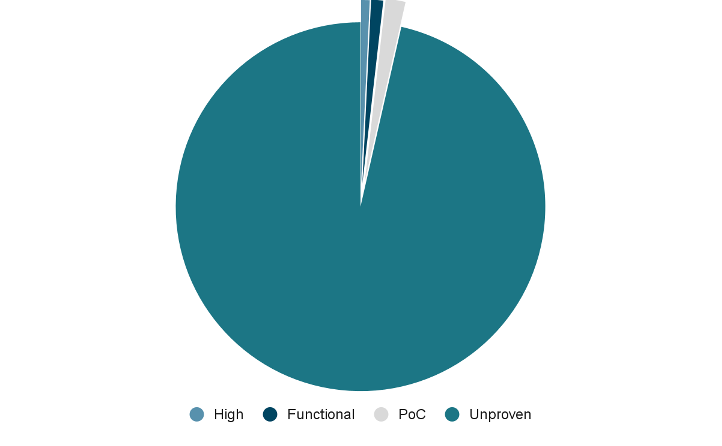
Source: Tenable Research, April 2023
Furthermore, as Fig. 4 shows, Tenable VPR rated 24 CVEs as Critical, 535 as High and 763 as Medium, all ahead of the vulnerabilities being fully disclosed on NVD. In addition, there were 479 CVEs that received a Low VPR score before being fully disclosed on NVD.
Fig. 4
Tenable VPR scores
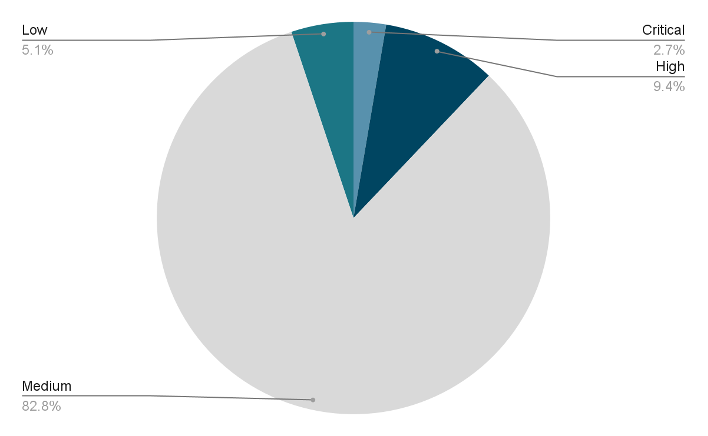
Source: Tenable Research, April 2023
Last, but not least, Tenable SRT issued Cyber Exposure Alerts for 150 of the vulnerabilities covered by VPR ahead of NVD.
Of the 25,080 vulnerabilities disclosed in 2022, 108 (0.43%) were rated with a Critical VPR score. For the vulnerabilities discovered ahead of NVD in 2022 (2,000 to date), we observed the following average timespans between when a vulnerability is first publicly referenced by a vendor and when it is scored and detailed on the National Vulnerability Database (see note):
- 45 days for vulnerabilities ranked with a Critical VPR score
- 71 days for vulnerabilities ranked with a High VPR score
- 130 days for vulnerabilities ranked with a Medium VPR score
- 148 days for vulnerabilities ranked with a Low VPR score
The maximum number of days we observed for vulnerabilities in each category are:
- 1,749 days for vulnerabilities ranked with a Critical VPR score
- 5,921 days for vulnerabilities ranked with a High VPR score
- 5,622 days for vulnerabilities ranked with a Medium VPR score
- 6,562 days for vulnerabilities ranked with a Low VPR score.
Zoom in: CVE highlights
In this section, we first analyze the gap for two noteworthy vulnerabilities from 2022. Then, we provide a quick outlook on vulnerabilities with the largest lapse between the time of discovery by Tenable Research and the time the vulnerabilities were fully disclosed on NVD.
Two noteworthy vulnerabilities in 2022
We examined the following two noteworthy named vulnerabilities that emerged in 2022: SpookySSL and Psychic Signatures.
|
SpookySSL CVE-2022-3786 and CVE-2022-3602 are two buffer overflow vulnerabilities affecting OpenSSL and fixed with the release of OpenSSL version 3.0.7. Both vulnerabilities received a High VPR rating. Tenable discovered the first piece of intelligence for both CVEs on October 27, 2022. Vulnerability details were fully disclosed on NVD five days later, on November 1, 2022. For these vulnerabilities, the earliest Nessus plugin coverage was provided on the same day as NVD. For more details and further guidance visit CVE-2022-3786 and CVE-2022-3602 OpenSSL patches two high severity vulnerabilities |
|
Psychic Signatures CVE-2022-21449, also known as Psychic Signatures, is a Java cryptographic signature vulnerability affecting Java 15, 16, 17 and 18. Tenable discovered the first piece of intel for this vulnerability on April 17, 2022. The vulnerability was fully disclosed on NVD two days later, on April 19, 2022. For this vulnerability, the earliest Nessus plugin coverage was provided on the same day as NVD. For more details and further guidance visit Oracle April 2022 Critical Patch Update Addresses 221 CVEs. |
Closing the gaps: How exposure management can help
We like to think that if Einstein were to work in cybersecurity in this era he would have said:
Learn from yesterday, assess your exposure today, hope for tomorrow.
Assessing and securing the modern attack surface depends on a multitude of conditions affecting today’s complex and dynamic environments. These factors all need to be viewed holistically in order for security practitioners to implement the preventive measures that help reduce risk.
To this end, implementing an exposure management program is fundamental. Threat actors do not think in silos. Rather, they look for the right combination of vulnerabilities, misconfigurations and identities that will give them the access they need to meet their objectives.
Yet, most security organizations rely on a hodgepodge of siloed point security tools that do not effectively allow them to obtain an overarching picture of the attack surface. An effective exposure management program requires dismantling silos by gathering together technologies such as vulnerability management, web application security, cloud security, identity security, attack path analysis and external attack surface management. It is only by considering all these factors in context that organizations can hope to understand the full breadth and depth of their exposures and take the actions needed to reduce them through remediation and incident response workflows.
About The Mind the Gap series
This four-part Mind the Gap blog series is a valuable resource for security professionals that provides an overview of the observed vulnerability landscape with a focus on vulnerabilities discovered by Tenable Research before detailed information appeared on the NVD. This series stems from the analysis of our own dataset, one of the most extensive and rich datasets in the industries. Through the years, we gathered a broad knowledge of the vulnerability landscape, enmeshed with Tenable Research-specific insights and reporting capabilities.
Other blogs in this series:
- Mind the Gap: How Waiting for NVD Puts Your Organization at Risk
- Mind the Gap: How Existing Vulnerability Frameworks Can Leave an Organization Exposed
- Mind the Gap: A Closer Look at Eight Notable CVEs from 2022
Learn More
- Vulnerability Management



