Microsoft’s May 2020 Patch Tuesday Addresses 111 CVEs

After back-to-back months of patching more than 100 CVEs, Microsoft released another 111 CVEs this month, none of which were publicly disclosed or exploited in the wild.
Microsoft addressed 111 CVEs in the May 2020 Patch Tuesday release, just short of the 113 CVEs seen in April. The updates this month include patches for Microsoft Windows, Microsoft Edge, ChakraCore, Internet Explorer, Microsoft Office, Microsoft Office Services and Web Apps, Windows Defender, Visual Studio, Microsoft Dynamics, .NET Framework, .NET Core and Power BI.
CVE-2020-1117 | Microsoft Color Management Remote Code Execution Vulnerability
CVE-2020-1117 is a remote code execution vulnerability in the Windows Color Management Module ICM32.dll due to how objects are handled in memory. An attacker that convinces a user to interact with a malicious link can execute commands on the vulnerable machine with the same rights as the active user.
CVE-2020-1126, CVE-2020-1028, CVE-2020-1136, and CVE-2020-1150 | Media Foundation Memory Corruption Vulnerability
CVE-2020-1126, CVE-2020-1028, CVE-2020-1136, and CVE-2020-1150 are memory corruption vulnerabilities that exist when Windows Media Foundation improperly handles objects in memory. Exploitation of these vulnerabilities could allow full system access to an attacker.
CVE-2020-1118 | Microsoft Windows Transport Layer Security Denial of Service Vulnerability
CVE-2020-1118 is a denial of service (DoS) vulnerability found in the Windows implementation of Transport Layer Security (TLS) due to improper handling of certain key exchanges. An attacker who successfully exploits this flaw can cause the target system to stop responding. Utilizing a specially crafted request against a system utilizing TLS 1.2 or lower, an attacker can trigger the DoS condition causing a system to automatically reboot.
CVE-2020-1023 and CVE-2020-1024 | Microsoft SharePoint Remote Code Execution Vulnerability
CVE-2020-1023 and CVE-2020-1024 are remote code execution vulnerabilities in Microsoft SharePoint when it fails to correctly check the source markup of an application package. An attacker who successfully exploits these vulnerabilities could run arbitrary code in the context of the SharePoint server farm account and the SharePoint Application pool. Exploitation of this flaw would require an attacker to successfully upload a specially crafted SharePoint application package to a vulnerable version of SharePoint.
CVE-2020-1069 | Microsoft SharePoint Server Remote Code Execution Vulnerability
CVE-2020-1069 is a remote code execution vulnerability that exists in Microsoft SharePoint Server when it fails to properly identify and filter unsafe ASP.Net web controls. An attacker who successfully exploits this vulnerability could run arbitrary code in the context of the SharePoint application pool process. The exploitation of this flaw requires the attacker to have authenticated access before they can craft and invoke a specially crafted page on a vulnerable version of Microsoft SharePoint Server.
CVE-2020-1054 and CVE-2020-1143 | Win32k Elevation of Privilege Vulnerability
CVE-2020-1054 and CVE-2020-1143 are both elevation of privilege vulnerabilities in Windows, which are a result of the Windows kernel-mode driver improperly handling objects in memory. In order to exploit these vulnerabilities, an attacker would need to log on to a system in order to execute a crafted application. Both of these CVEs are rated as ‘Exploitation More Likely’ by Microsoft.
CVE-2020-1135 | Windows Graphics Component Elevation of Privilege Vulnerability
CVE-2020-1135 is an elevation of privilege vulnerability in the Windows Graphics Component, due to improper handling of objects in memory. A local attacker could exploit this vulnerability by executing a crafted application to take control of an affected system.
CVE-2020-0901 | Microsoft Excel Remote Code Execution Vulnerability
CVE-2020-0901 is a remote code execution vulnerability in Microsoft Excel caused by an error in how objects are handled in memory. To exploit this vulnerability, an attacker must entice a user to open a specially crafted file with a vulnerable version of Microsoft Excel. While Microsoft rates this flaw as ‘Exploitation Less Likely,’ attackers frequently use malicious emails in attacks, and the current work-from-home situation offers greater opportunities for malicious actors to take advantage of flaws like this one.
CVE-2020-1171 and CVE-2020-1192 | Visual Studio Code Python Extension Remote Code Execution Vulnerability
CVE-2020-1171 is a remote code execution vulnerability that exists in Visual Studio code when the Python extension loads configuration files after opening a project, whereas CVE-2020-1192 exists when the Python extension loads workspace settings from a notebook file. Successful exploitation of either vulnerability would result in the execution of arbitrary code in the context of the current user.
If the current user has administrative rights, an attacker could create accounts with full administrative rights, install malicious applications, and view, modify or delete files. To exploit CVE-2020-1171, an attacker would need to convince a victim to open a specially crafted file in Visual Studio Code with the Python extension installed. The exploitation of CVE-2020-1192 requires an attacker to create a repository with malicious code, then convince a victim to clone this repository and open it in Visual Studio Code with the Python extension installed.
CVE-2020-1153 | Microsoft Graphics Components Remote Code Execution Vulnerability
CVE-2020-1153 is a remote code execution vulnerability in the Microsoft Graphics Components due to the way objects are handled in memory. Successful exploitation of this vulnerability would allow an attacker to execute arbitrary code. In order to exploit the flaw, the attacker would need to utilize social engineering tactics to convince a user to open a specially crafted file containing the exploit code.
Tenable solutions
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains May 2020.
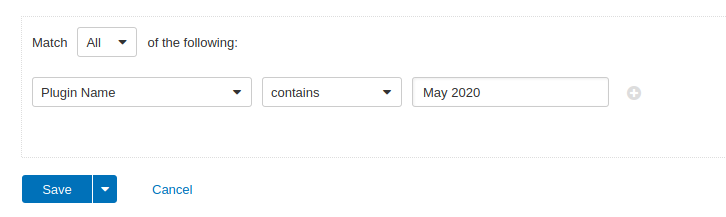
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
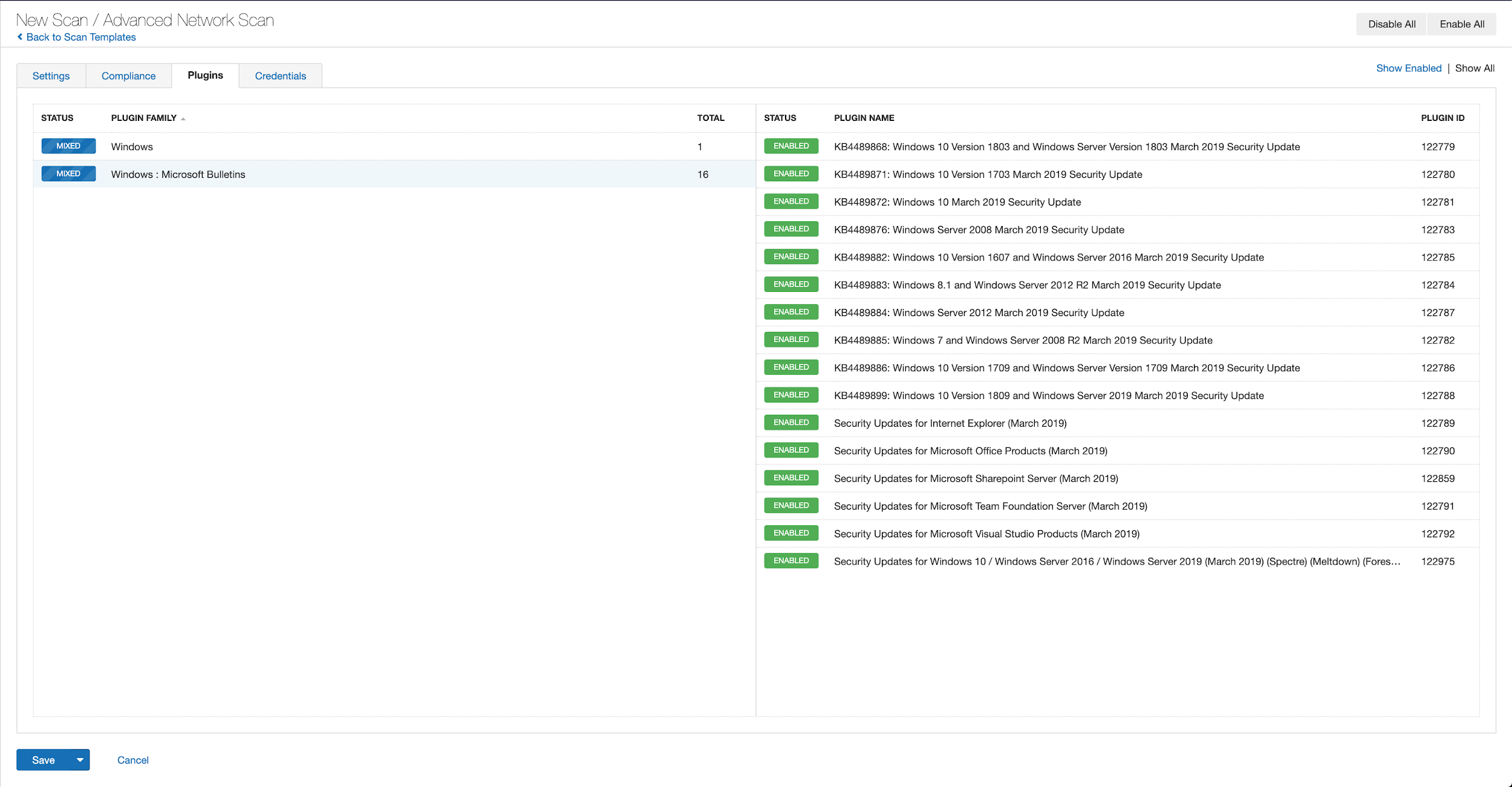
A list of all the plugins released for Tenable’s May 2020 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's May 2020 Security Updates
- Tenable plugins for Microsoft May 2020 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

