How to Perform Efficient Vulnerability Assessments with Tenable

Policy configuration choices in vulnerability assessment tools like Tenable Nessus, Tenable Security Center and Tenable Vulnerability Management enable security professionals to effectively gather data that can be analyzed to aid in prioritizing remediation.
In practicing preventive cybersecurity, most security teams want to gather as much information as quickly and efficiently as possible so they can accurately evaluate risk in their environment. Most security professionals we work with prefer to spend their time making appropriate risk-based decisions, not waiting on scans to complete or trying to figure out how to test for the latest zero-day or Microsoft Patch Tuesday releases.
Tenable’s toolsets offer a wide variety of scan policy knobs and switches; while these options are important, they can make it challenging for security pros to ‘set it and forget it’ from an assessment perspective. This blog highlights some of the do’s and don’ts of scan configuration to help users get some time back so they can focus on other tasks.
Make time for discovery before initiating broad vulnerability scans
In larger or dynamic networks, Tenable recommends doing discovery prior to undertaking a full vulnerability scan of a large subnet(s). Discovery reduces the time spent trying to scan empty IP space and can alert users faster to outliers that may have bypassed proper processes. Here are some options for performing discovery in bigger environments:
- Network Discovery Scans in Tenable Vulnerability Management and Tenable Security Center
- Nessus Network Monitor in Discovery Mode in Tenable Vulnerability Management and and Tenable Security Center
- Third-party integrations like Cisco or Forescout
Use basic or advanced scan policies for vulnerability scans
When running a standard vulnerability scan against a target, use the “Basic Network Scan” or “Advanced Network Scan” policies. These policies have the exact same starting configuration but the advanced scan is simply a replica that allows for granular customization (this concept also applies to agent scan policies). In most scenarios for most customers, these policies will be able to scan any target efficiently and safely with the default settings for the majority of vulnerabilities in an environment.
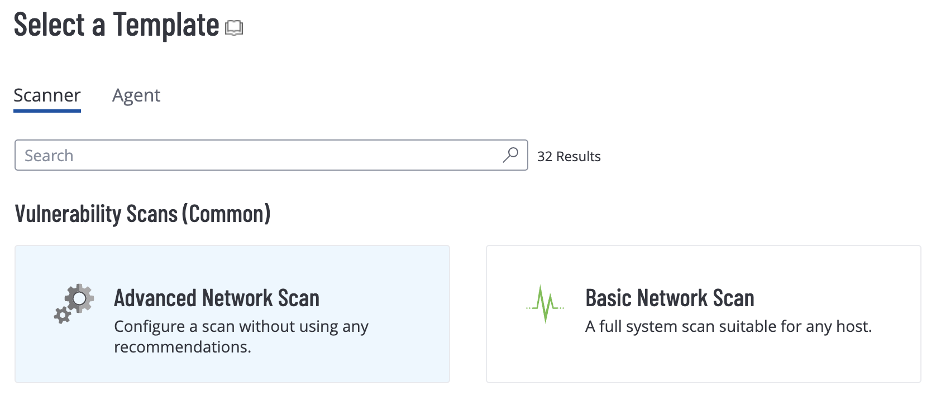
Source: Tenable, September 2023
Use credentials or agents
Having good authentication across your vulnerability scans is not only critical for obtaining high quality results, it also increases the efficiency of the scan and, in some cases, can reduce the overall license usage as Tenable will collapse results that it can correlate into the same licensed asset.
Scan frequently
Tenable recommends frequent host assessments to keep up on the latest vulnerabilities and changes made to targets; how often users perform this function will depend a little on organizational requirements, but Tenable recommends no less than twice a week for most scenarios. Some Tenable technologies, like Agentless Assessment, Inventory Scanning, Live Results, and Nessus Network Monitor, allow for more continuous monitoring and live updates of vulnerability data without re-scanning the target.
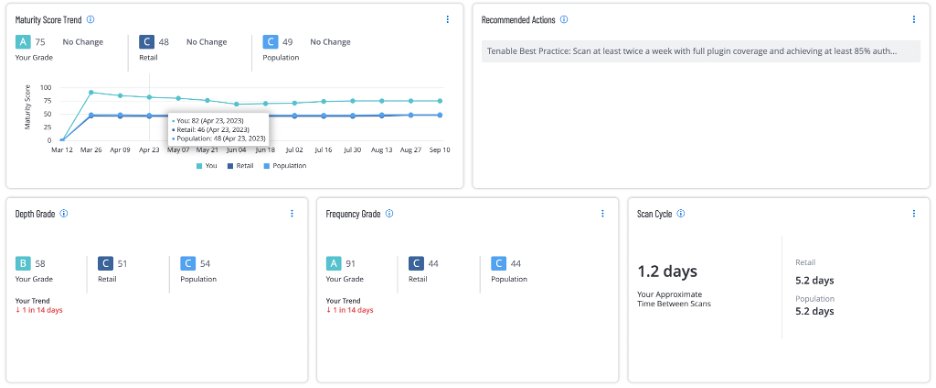
Source: Tenable, September 2023
Three things to avoid when performing a scan
1. Selecting individual plugins/families in a scan policy
Nessus, when used as an agent or when run standalone or as a managed scanner, automatically runs the correct plugins against each target at scan time. While highly targeted scan policies with limited plugins may run faster in some scenarios, most customers should not cherry-pick plugins to run against their systems, as doing so can result in missing future detections, missing new CVEs when released and lower confidence in the accuracy of the assessments. Tenable recommends not to modify the plugin families or individual plugins of scan policies in most scheduled scan jobs. For example, when scanning for monthly Microsoft Patch Tuesday advisories, simply re-scan with a basic or advanced scan policy with all plugins enabled; there is no need to create a separate scan policy with only these plugins.
2. Using tactical scan policies
Tactical scan policies are designed for limited, targeted use when discovery and insight to a particular vulnerability or set of vulnerabilities is extremely time sensitive. Given the rapidly changing threat landscape, Tenable recommends not relying on these for vulnerability detection over time, as these risks will also be detected by regularly scheduled comprehensive vulnerability scans.
3. Disable ‘'Show missing patches that have been superseded’’
When enabled, this option will include superseded patch information in the scan report. Disabling this setting will hide superseded findings and limit visibility into older missing patches, including potential Critical severity findings. The same view (“show me only the patches I need to apply”) can be reproduced by:
- Using the output of plugin 66334, 'Patch Report'. This provides the same output as disabling 'Show missing patches that have been superseded', but in a specific plugin. All other dependent plugins still trigger.
- Using Tenable Security Center, choose the Remediation Summary Analysis Tool under Analysis - Vulnerabilities or Solutions.
- Using Tenable Lumin, choose Vulnerability Management - Solutions.
Six assessment guidelines to remember
- When scanning large or dynamic networks, perform discovery first.
- Use the basic or advanced scan policies in most circumstances; they will cover most scanning scenarios automatically.
- Perform fully authenticated assessments wherever possible; these provide up to 45 times more findings and insights than uncredentialed assessments.
- Scan at least twice a week to track environmental changes and discover newly released vulnerabilities or existing ones introduced into your environment.
- Limit customizing the plugins, as doing so can lead to overlooked risks or false positives; Nessus automatically determines what tests to run against a target;.
- Don’t disable “Show missing patches that have been superseded” as doing so will provide a false sense of security by hiding potentially critical findings.
Learn more
- 'Show missing patches that have been superseded' setting explained (KB Article)
- Useful plugins to troubleshoot credential scans (KB Article)
- Tuning Network Assessments for Performance and Resource Usage (Blog)
- CISA Directive 22-01: How Tenable Can Help You Find and Fix Known Exploited Vulnerabilities (Blog)
- Security Metrics - How Often Should We Scan? (Blog)
- Patch Report (Plugin)
- Developing and Maintaining a Software Inventory (Cyber Exposure Study)
- Assets - Tenable Vulnerability Management (Documentation)
- Scan and Policy Settings (Documentation)
- Nessus Scan Tuning Guide (Documentation)
- Tenable Vulnerability Management Scan Tuning Guide (Documentation)
- Tenable Security Center Scan Tuning Guide (Documentation)
- Vulnerability Management
- Vulnerability Scanning


