by Megan Daudelin
January 15, 2016
Tenable Network Security has been certified by the Center for Internet Security (CIS) to perform a wide variety of Unix, Windows, and application audits based on the best practice consensus benchmarks developed by CIS. These best practice benchmarks contain recommended security settings designed to harden servers and applications against attack while still maintaining operational ease of use.
As defined by the Center for Internet Security, CIS Security Benchmarks programs provide well-defined, unbiased, and consensus-based industry best practices to help organizations assess and improve their security. Resources include secure configuration benchmarks, automated configuration assessment tools and content, security metrics, and security software product certifications. The Security Benchmarks program is recognized as a trusted, independent authority that facilitates the collaboration of public and private industry experts to achieve consensus on practical and actionable solutions. Because of the reputation, our resources are recommended as industry-accepted system hardening standards and are used by organizations in meeting compliance requirements for FISMA, PCI, HIPAA, and other security requirements.
The CIS RHEL Summary report is designed to display the overall compliance status of the network based on Tenable's certified Center for Internet Security (CIS) Red Hat Enterprise Linux Configuration Benchmark audits. The report can be used with all of Tenable's CIS-certified Linux and UNIX audits with minor modifications. For best results when using multiple CIS audits, ensure the results are separated into different repositories.
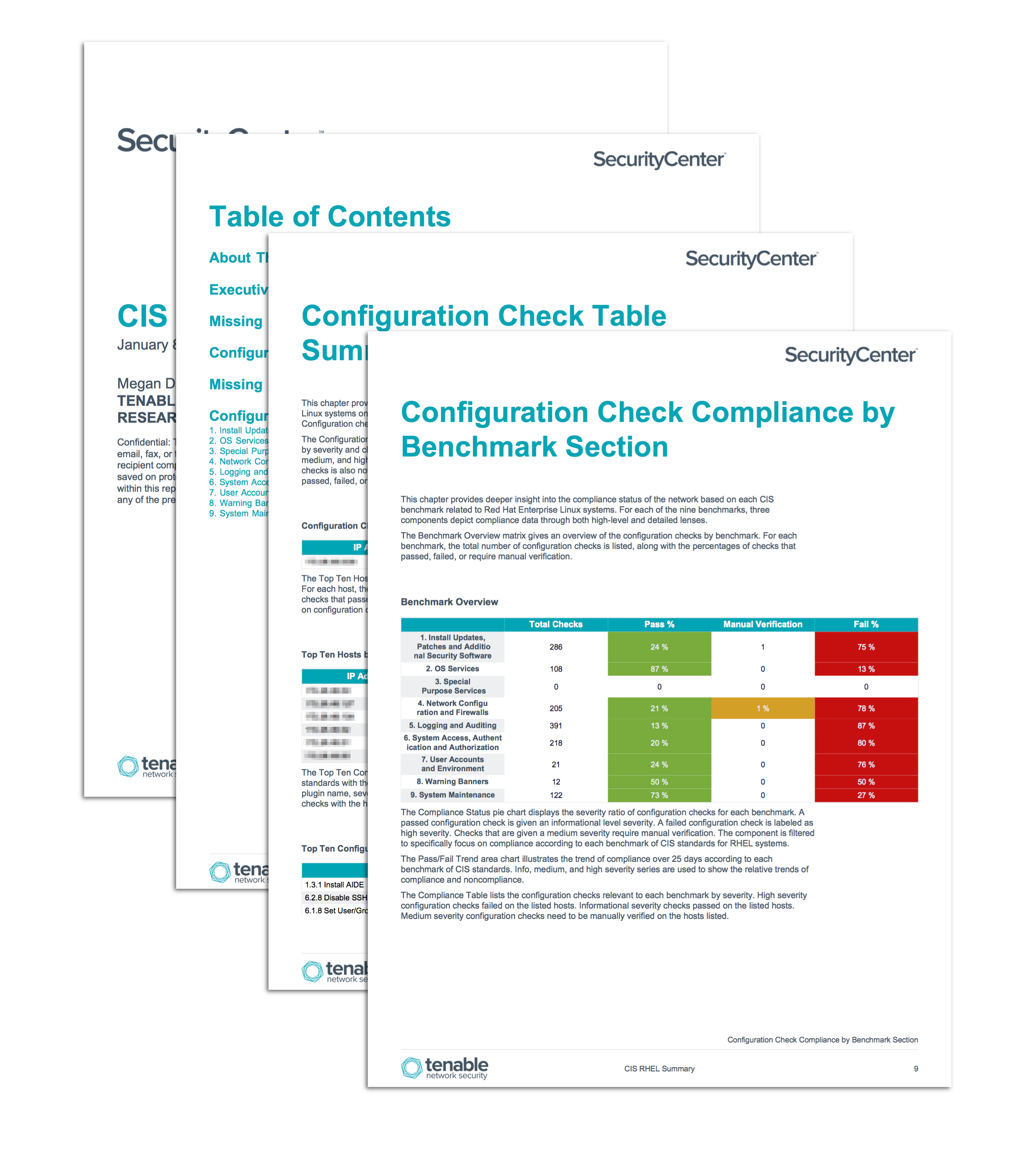
A key element of the CIS RHEL report is the Configuration Check Compliance by Benchmark Section chapter. The chapter focuses on each of the nine benchmark sections and provides detailed information about the relevant configuration checks. The sections may be correlated to the table of contents and configuration check references contained within the CIS PDF benchmark guides. Detailed information about the compliance and patch status of RHEL systems is also included in the report.
The report is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The report can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessments.
The report requirements are:
- Tenable.sc 4.8.2
- Nessus 8.5.1
- This report requires “Full Text Search” to be enabled for each analyzed repository.
Tenable.sc Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new types of regulatory compliance configuration audits. Tenable.sc CV allows for the most comprehensive and integrated view of network health.
The report contains the following chapters:
- Executive Summary: This chapter provides a high-level overview of the compliance status of the Red Hat Enterprise Linux (RHEL) systems on the network based on CIS standards.
- Missing RHEL Patches: This chapter provides an overview of the vulnerabilities associated with missing patches on Red Hat Enterprise Linux systems in the network.
- Configuration Check Summaries: This chapter provides three distinct views into the configuration compliance of Red Hat Enterprise Linux systems on the network.
- Missing RHEL Patch Summaries: This chapter provides three distinct views into the patches missing on Red Hat Enterprise Linux systems in the network.
- Configuration Check Compliance by Benchmark Section: This chapter provides deeper insight into the compliance status of the network based on each CIS benchmark related to Red Hat Enterprise Linux systems.