by Stephanie Dunn
January 26, 2017
Organizations will always have a certain number of vulnerabilities and risks present within their environment. Each organization will have a unique risk tolerance based on their industry and compliance requirements, and may not fully understand which vulnerabilities present the greatest risk. Threats exist in user productivity software, hardware devices, and many other devices that are frequently used by the organization. Without having a clear and continuous view of existing vulnerabilities, organizations will struggle to identify and respond to threats in a timely manner. Information presented within this dashboard will provide organizations with the actionable intelligence needed to improve overall security posture and protect critical assets.
The National Institute of Standards and Technology (NIST) developed the NIST Special Publication (SP) 800-53 revision 4, “Security and Privacy Controls for Federal Information Systems and Organizations” to provide federal information systems and organizations with security controls and processes to protect against a diverse set of threats including hostile cyber attacks, natural disasters, structural failures, and human errors. By integrating these controls, organizations will be able to achieve a more consistent level of security and flexibility that can be customized for use with specific industries, standards, and business requirements, and complement other established information security standards. Data presented within this dashboard aligns with NIST 800-53 security controls that support vulnerability management, risk assessment, and risk remediation efforts. This dashboard aligns with the following controls:
- Flaw Remediation (SI-2)
- Risk Assessment (RA-3)
- Vulnerability Scanning (RA-5)
There are many patch management solutions that can automatically deploy patches to specific kinds of systems and/or software within a network. Unfortunately, some of these solutions do not support software that most modern organizations use. For example, an organization may use Windows Server Update Services (WSUS) to address vulnerabilities found within Microsoft Office or Microsoft Windows systems. However, this solution won’t address vulnerabilities found within third-party applications such as Google Chrome, Adobe Flash, and Oracle Java that are frequently exploited by attackers. To maintain all of those systems, some organizations use multiple patch management solutions to ensure that systems are patched in a timely manner.
Analysts need a way to ensure that patch management solutions are providing consistent and reliable information about patched systems. Although this will address some operating system or security-based vulnerabilities, many of these solutions do not address other vulnerabilities present within the network. Using credentialed scanning, Tenable's Tenable.sc Continuous View (CV) integrates vulnerability data gathered from Tenable Nessus, and monitors vulnerabilities detected by patch management solutions. Using this information will help to close this gap on vulnerabilities that may have been missed by these solutions.
The components in this dashboard cover vulnerability data reported from patch management solutions. Tenable supports a variety of patch management solutions, including Microsoft System Center Configuration Manager (SCCM), Windows Server Update Services (WSUS), Dell KACE, IBM BigFix, and Symantec Altiris. When Tenable.sc CV correlates all of the information, analysts can see where vulnerability remediation efforts can best pay off for the organization such as identifying specific vulnerabilities posing the greatest risk. When comparing two critical vulnerabilities, it may not always be clear which vulnerability should be remediated first. While both critical vulnerabilities need to be addressed, this dashboard provides clear information about all vulnerabilities in the environment. Having accurate and relevant information will help to address security gaps, and prioritize response efforts.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.4.2
- Nessus 8.4.0
- LCE 6.0.0
- NNM 5.8.1
- complianceData
Tenable's Tenable.sc CV is the market-defining continuous network monitoring solution, and assists in securing an organization’s internal network. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and regulatory compliance data. Active scanning periodically examines systems to detect vulnerabilities within operating systems, software applications, and hardware. Agent scanning enables scanning and detection of vulnerabilities on transient and isolated devices. Passive listening provides real-time discovery of vulnerabilities on operating systems, protocols, network services, wireless devices, web applications, and critical infrastructure. Host data and data from other security products is analyzed to monitor activity from patch management solutions and services. Tenable.sc CV provides an organization with the most comprehensive view of the network and the intelligence needed to fully understand the impact of vulnerabilities on the network.
The following components are included within this dashboard:
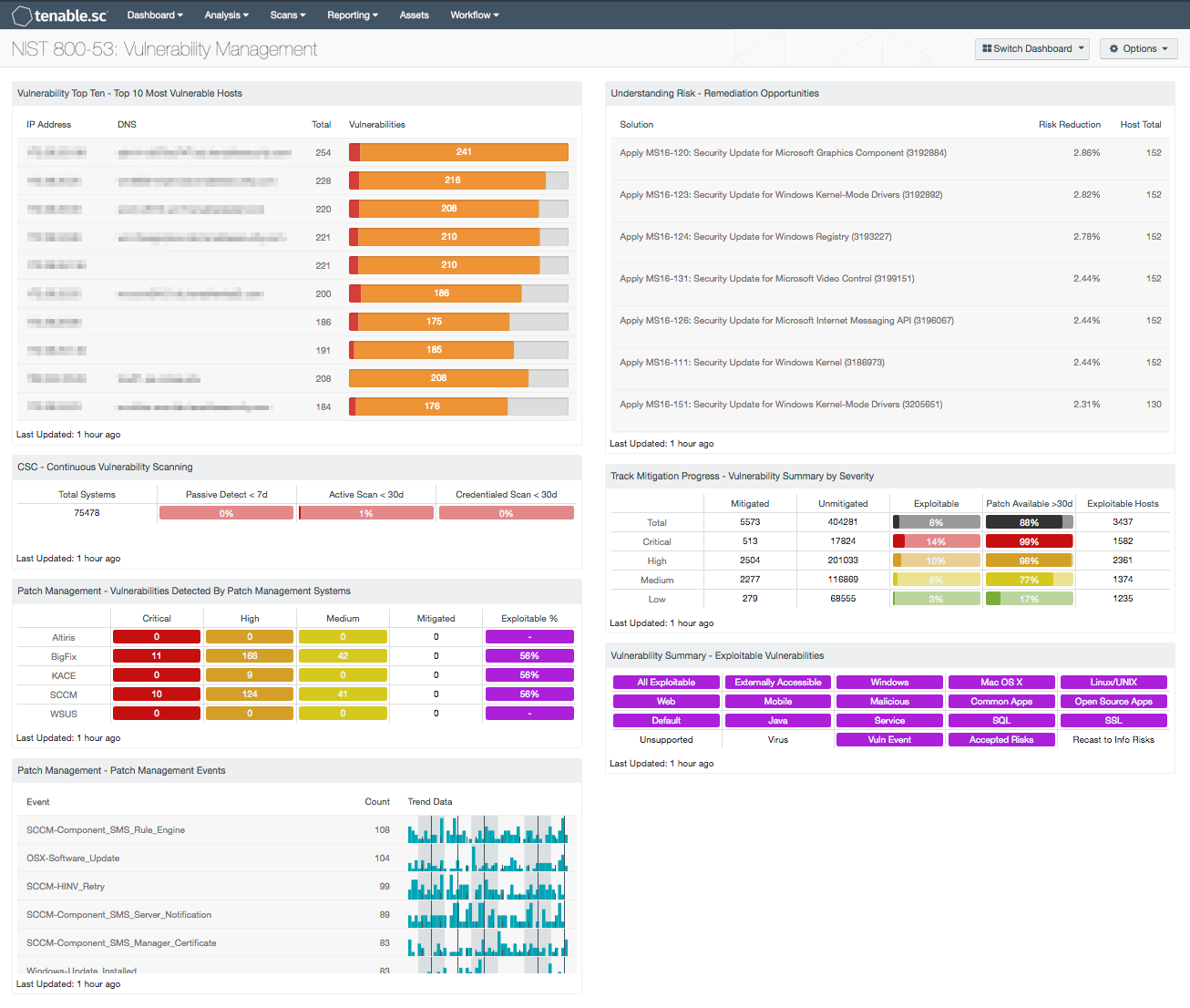
- Vulnerability Top Ten - Top 10 Most Vulnerable Hosts: This component shows the top ten hosts with exploitable vulnerabilities of high or critical severity. Editing the filters in the component and changing the tool from IP Summary to Class C Summary or Port Summary can give information on exploitable vulnerabilities per subnet or per port, respectively.
- CSC - Continuous Vulnerability Scanning: This matrix assists in monitoring the vulnerability detection and scanning performed by the Tenable's Nessus Network Monitor (NNM) and Tenable Nessus. Presented are the percentages of total systems that have had recent passive vulnerability detections, active vulnerability scans, and credentialed scans. This information highlights detection coverage and whether vulnerability scans are being regularly executed. The timeframes may be altered to fit organizational requirements.
- Patch Management - Vulnerabilities Detected By Patch Management Systems: This matrix presents an overview of detected vulnerabilities reported by patch management systems. Tenable supports a wide variety of patch management solutions including SCCM, WSUS, IBM BigFix, Dell KACE K1000, and Symantec Altiris. Vulnerabilities are filtered by the Windows: Microsoft Bulletins plugin family, and presents a list of Microsoft vulnerabilities that have been reported by a patch management system. Each column presents the total count of vulnerabilities per severity level, mitigated vulnerabilities, and percentage of exploitable vulnerabilities.
- Patch Management - Patch Management Events: This component includes a list of detected events from patch management systems over the last 72 hours. The list is ordered so that the highest number of patch management events are at the top. Log events from patch management systems are forwarded to the Tenable Log Correlation Engine (LCE) server. Some events are passively detected by the Tenable Nessus Network Monitor (NNM) and then forwarded to LCE. Tenable supports a wide variety of patch management solutions and services including SCCM, WSUS, Windows Update, IBM BigFix, OS X Software Update, and Linux Yum Updates. Event data can detect changes in patch management solutions that analysts monitor to determine if further action is needed. Built-in patch management services can alert analysts if a patch failed to install correctly, or a host needs to be restarted.
- Understanding Risk - Remediation Opportunities: This table displays the top remediations for the network. For each remediation, the risk reduction for the network if the remediation is implemented is shown, along with the number of hosts affected. The table is sorted so that the highest risk reduction is at the top. Implementing the remediations will decrease the overall vulnerability of the network. Adding filters to the component, such as filtering on only critical severity vulnerabilities or filtering on a specific asset group, can narrow the focus of the component, giving remediation opportunities in specific areas.
- Track Mitigation Progress - Vulnerability Summary by Severity: This component assists in tracking vulnerability mitigations. In the matrix, the row with red is critical severity vulnerability information, the row with orange is high severity, the row with yellow is medium severity, and the row with green is low severity. The Mitigated column displays the number of vulnerabilities that have been moved to the mitigated database. A vulnerability is moved to the mitigated database when the vulnerability is no longer detected by a rescan; the vulnerability is assumed to be remediated. The Unmitigated column displays the number of current vulnerabilities that are not yet remediated and have not been moved to the mitigated database. The Exploitable column displays the percentage of those unmitigated vulnerabilities that are known to be exploitable. The Patch Available column displays the percentage of the unmitigated, exploitable vulnerabilities that have had a patch available for more than 30 days. Ideally, both of these percentages should be 0%, because all exploitable vulnerabilities and all vulnerabilities with patches available should have been mitigated already. The Exploitable Hosts column displays the number of hosts on the network that have unmitigated, exploitable vulnerabilities.
- Vulnerability Summary - Exploitable Vulnerabilities: This matrix displays warning indicators for exploitable vulnerabilities actively and passively detected on the network, including vulnerabilities by OS, web vulnerabilities, application vulnerabilities, and vulnerabilities by keywords such as "Java" and "unsupported". Exploitable vulnerabilities that are externally accessible (i.e., accessible from hosts outside of the configured network address range) are very dangerous and must be remediated as soon as possible. Exploitable vulnerabilities that have been marked as accepted risks or recast to Informational within SecurityCenter are also noted; these vulnerabilities should likely be re-evaluated.