by Cody Dumont
February 13, 2014
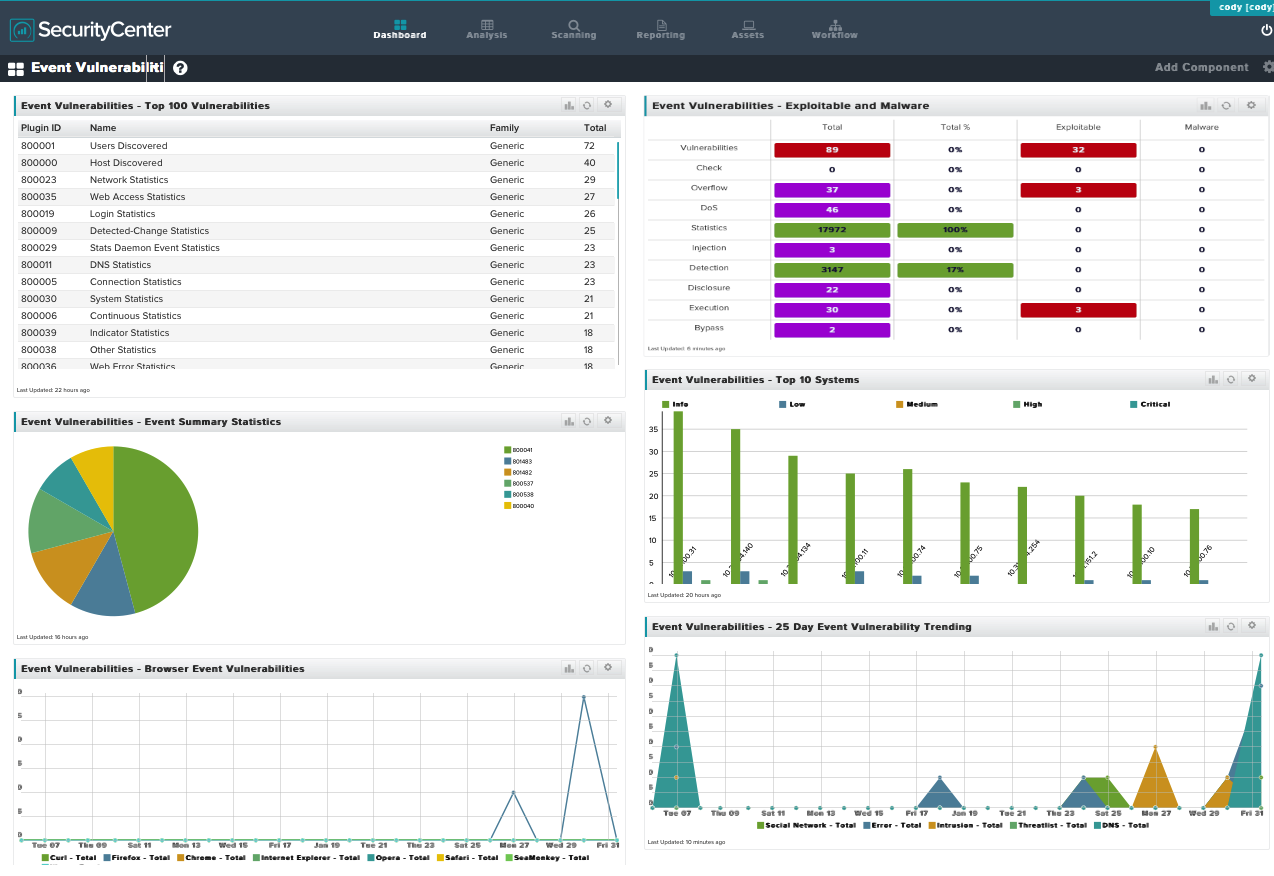
This dashboard highlights the vulnerabilities discovered from the events collected from the Log Correlation Engine (LCE). Using exploitable vulnerability and vulnerability trending graphs, this dashboard helps security managers identify vulnerabilities without scanning the remote systems.
Beginning with version 4.2.0, LCE analyzes log data to passively detect and identify a variety of vulnerabilities. LCE detects running applications and services to provide additional data for software inventory and identification. This enables Tenable vulnerability correlation and continuous monitoring to quickly determine the number of systems on a network, as well as which systems are undergoing vulnerability scanning, network monitoring, and log analysis. The Tenable plugins that report this information are plugin IDs in the range of 800000 – 899999; these are the Event Vulnerabilities type plugins.
The dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Threat Detection & Vulnerability Assessments.
The dashboard requirements are:
- SecurityCenter 4.7.1
- LCE 4.2.2
- PVS 4.0
Listed below are the included components:
- Event Vulnerabilities - Top 100 Vulnerabilities: This component displays a table of event vulnerabilities sorted by the total vulnerabilities discovered.
- Event Vulnerabilities - Event Summary Statistics: This component highlights the top 10 event statistical summary plugins. These plugins provide summary reports on the various statistics generated by the LCE “stats” daemon.
- Event Vulnerabilities - Browser Event Vulnerabilities: This component displays 25-day vulnerability trend lines for several different Internet browser vulnerabilities.
- Event Vulnerabilities - Exploitable and Malware: The component displays a matrix on the top 10 most common event vulnerability keywords. The matrix contains columns for the total number of vulnerabilities, the percentage of vulnerabilities, which have the keyword, and the number of vulnerabilities that are exploitable or exploitable by malware.
- Event Vulnerabilities - Top 10 Systems: This component displays the IP address summary of the systems with most event vulnerabilities.
- Event Vulnerabilities - 25 Day Event Vulnerability Trending: The component displays a 25-day trending graph of 5 threat orientated event vulnerabilities.