by Liz Hutto
January 19, 2022
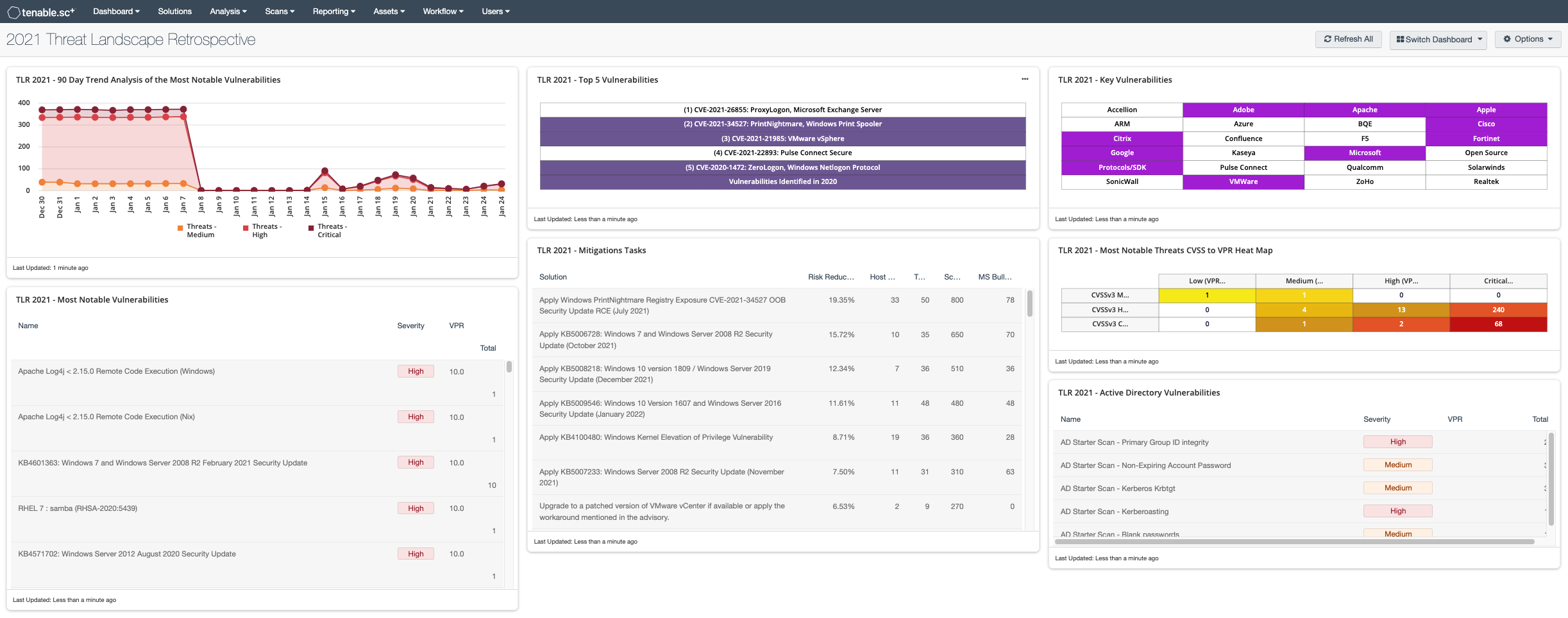
2021 was certainly a turbulent year, punctuated with the revelation of a critical vulnerability in the widely-used Apache Log4j library. The lingering Covid-19 pandemic had already accelerated online and cloud migration, providing ripe targets for attackers. Organizations were faced with higher risks from interconnectivity resulting in major disruption from breaches, ransomware attacks, and attacks on the software supply chain. Tenable’s 2021 Threat Landscape Retrospective (TLR) provides valuable lessons learned as attackers relentlessly exploited the software supply chain. Cyber security practices need to evolve to address modern technology deployments. This dashboard leverages Tenable’s 2021 Threat Landscape Retrospective to identify the most notable vulnerabilities that occurred in 2021.
The migration to cloud platforms, SaaS, IaaS, and managed service providers has changed the definition of the perimeter. Applying outdated cyber security tactics to modern cloud infrastructure is ineffective to combat current threats. A Risk-Based Vulnerability Management (RBVM) approach that evolves with the changing threat landscape is necessary to prioritize identification of unnecessary services and software, limit third-party code, implement a secure software development lifecycle, and perform accurate asset detection across the entire attack surface. Modern vulnerability management programs must include information technology, operational technology, and internet of things (IoT), whether they reside in the cloud or on premises. RBVM requires identifying and fixing critical vulnerabilities and misconfigurations in cloud and Active Directory. Unpatched vulnerabilities represent lucrative opportunities for ransomware attackers, leading to successful ransomware attacks and breaches, such as the Kaseya, SolarWinds, Colonial Pipeline, and Conti attacks.
Organizations usually perform a “lessons learned” meeting after a breach to discuss what went right, what went wrong, and how to improve their response moving forward. Tenable’s Security Response Team (SRT) continuously provides valuable insight and perspective on new threats that may affect an organization’s cyber security posture. SRT’s research enables organizations to prioritize and create remediation plans for the evolving threat landscape. This dashboard uses CVE filters to display the top five most notable threats and provides indicators for the remaining threats identified in 2021. The content enables organizations to understand the full scope of the current attack surface and refine their security strategy accordingly.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards (ARCs), and assets. The dashboard is easily located in the Tenable.sc Feed in the Security Industry Trends category.
The dashboard requirements are:
- Tenable.sc 5.20.0
- Nessus 10.0.2
Tenable Research delivers world class cyber exposure intelligence, data science insights, alerts, and security advisories. The Tenable Research teams perform diverse work that builds the foundation of vulnerability management. The Security Response Team (SRT) tracks threat and vulnerability intelligence feeds and provides rapid insight to the Vulnerability Detection team, enabling them to quickly create plugins and tools that expedite vulnerability detection. This fast turnaround enables customers to gain immediate insight into their current risk posture. Tenable Research has released over 165,000 plugins and leads the industry on CVE coverage. Additionally, the SRT provides breakdowns for the latest vulnerabilities on the Tenable Blog and produces an annual Threat Landscape Retrospective. The SRT continuously analyzes the evolving threat landscape, authors white papers, blogs, Cyber Exposure Alerts, and additional communications to provide customers with comprehensive information to evaluate cyber risk.
This dashboard contains the following components:
TLR 2021 - 90 Day Trend Analysis of the Most Notable Vulnerabilities: This trend graph provides a 90-day analysis of the most notable vulnerabilities in 2021, leveraging the CVEs identified in Tenable's 2021 Threat Landscape Retrospective (TLR).
TLR 2021 - Most Notable Vulnerabilities: This table provides a list of the most notable vulnerabilities in 2021, leveraging the CVEs identified in Tenable's 2021 Threat Landscape Retrospective (TLR).
TLR 2021 - Top 5 Vulnerabilities: This table features the top five vulnerabilities of 2021 defined in Tenable's 2021 Threat Landscape Retrospective (TLR).
TLR 2021 - Mitigations Tasks: This table provides a list of patches that mitigate the most notable vulnerabilities in 2021, leveraging the CVEs identified in Tenable's 2021 Threat Landscape Retrospective (TLR).
TLR 2021 - Key Vulnerabilities: This indicator matrix displays a list of vendors that had 2021’s most significant vulnerabilities.
TLR 2021 - Most Notable Vulnerabilities CVSS to VPR Heat Map: This matrix provides a correlation between CVSSv3 scores and VPR scores for the vulnerabilities that include the 315 CVEs discussed in the Tenable's 2021 Threat Landscape Retrospective (TLR).
TLR 2021 - Active Directory Vulnerabilities: This table displays multiple Active Directory (AD) findings with relevant configuration improvement recommendations.