Tweetable Exploit for X.org Server Local Privilege Escalation (CVE-2018-14665) Released

A researcher has published a local privilege escalation exploit that fits in a single tweet for xorg-x11-server. Vendors are rolling out fixes and mitigation advice.
Contexte
On October 25, a tweetable proof-of-concept (PoC) exploit for a newly discovered local privilege escalation (LPE) vulnerability in xorg-x11-server was released.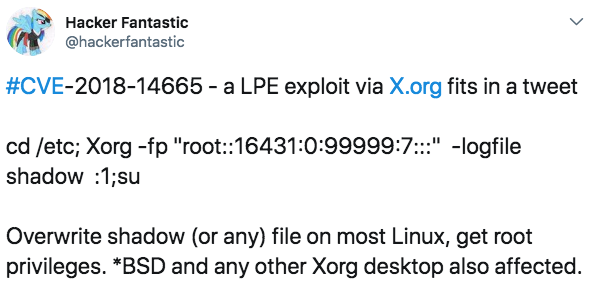
Not surprisingly, exploitable scripts were quickly available on the web due to the trivial nature of this exploit.
Impact assessment
This vulnerability allows Linux and Unix hosts running xorg-server in setuid (privileged) mode to have files overwritten via the -logfile and -modulepath parameters. While vendors are still assessing the impact of the vulnerability on their products, Red Hat has determined that Red Hat Enterprise Linux versions 7.4 and later are affected. However, this vulnerability affects only local users, as the default Pluggable Authentication Modules (PAM) configuration prevents exploitation over SSH connections. It’s also relatively uncommon for server-based Linux or Unix administrators to run X.org. At this time, other vendors are releasing patches along with mitigation advice where applicable. For example, OpenBSD tweeted:
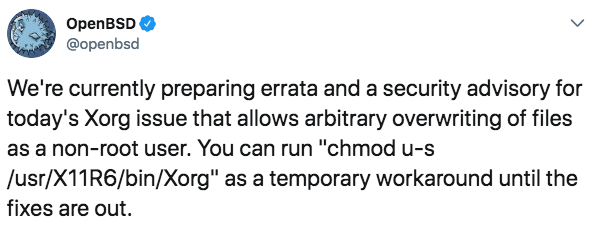
Because of the limited range of affected versions and the specific and often non-default configurations required to trigger this exploit, the attack’s scope appears to be narrow. However, it’s likely that malicious individuals will still seek out vulnerable systems.
Vulnerability details
This vulnerability was first introduced as a regression as part of security checks for “dangerous options” in xorg-server 1.19.0. According to the X.org security advisory:
The -modulepath argument can be used to specify an insecure path to modules that are going to be loaded in the X server, allowing to execute unprivileged code in the privileged process. The -logfile argument can be used to overwrite arbitrary files in the file system, due to incorrect checks in the parsing of the option.
The affected versions are xorg-x11-server 1.19.0 through 1.20.2.
Urgently required actions
Check for Linux and Unix systems running xorg-x11-server 1.19.0 through 1.20.2 and confirm when vendor fixes become available. In the interim, apply any vendor mitigations related to removing the setuid bit and disable and/or remove xorg-x11-server on any server or desktop systems where it is not needed. According to X.org:
If a patched version of the X server is not available, X.Org recommends to remove the setuid bit (ie chmod 755) of the installed Xorg binary. Note that this can cause issues if people are starting the X window system using the 'startx', 'xinit' commands or variations Thereof.
X.org recommends the use of a display manager to start X sessions, which does not require Xorg to be installed setuid.
Identification des systèmes affectés
Une liste de plug-ins Tenable permettant d'identifier cette vulnérabilité apparaîtra ici au fur et à mesure de leur publication.
En savoir plus
- Xorg Security Advisory
- Red Hat Advisory
- OpenBSD Errata
- Proof of concept script for vulnerable servers
Learn more about Tenable.io, the first Cyber Exposure platform for holistic management of your modern attack surface. Get a free 60-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


