Quick Credential Debug Scan

What scans do you use? Tenable customers can assess their security risks from information gathered by vulnerability and compliance scans. In this blog, I’ll show you how to build a customized scan that helps diagnose authentication issues that show up when running those scans. I call it the Quick Credential Debug Scan, or QCD for short.
QCD is popular because of its speed and its light impact on the target. QCD performs key tests required to access the target system. Even though the scan requires credentials, the scan does not probe for vulnerability or compliance information.
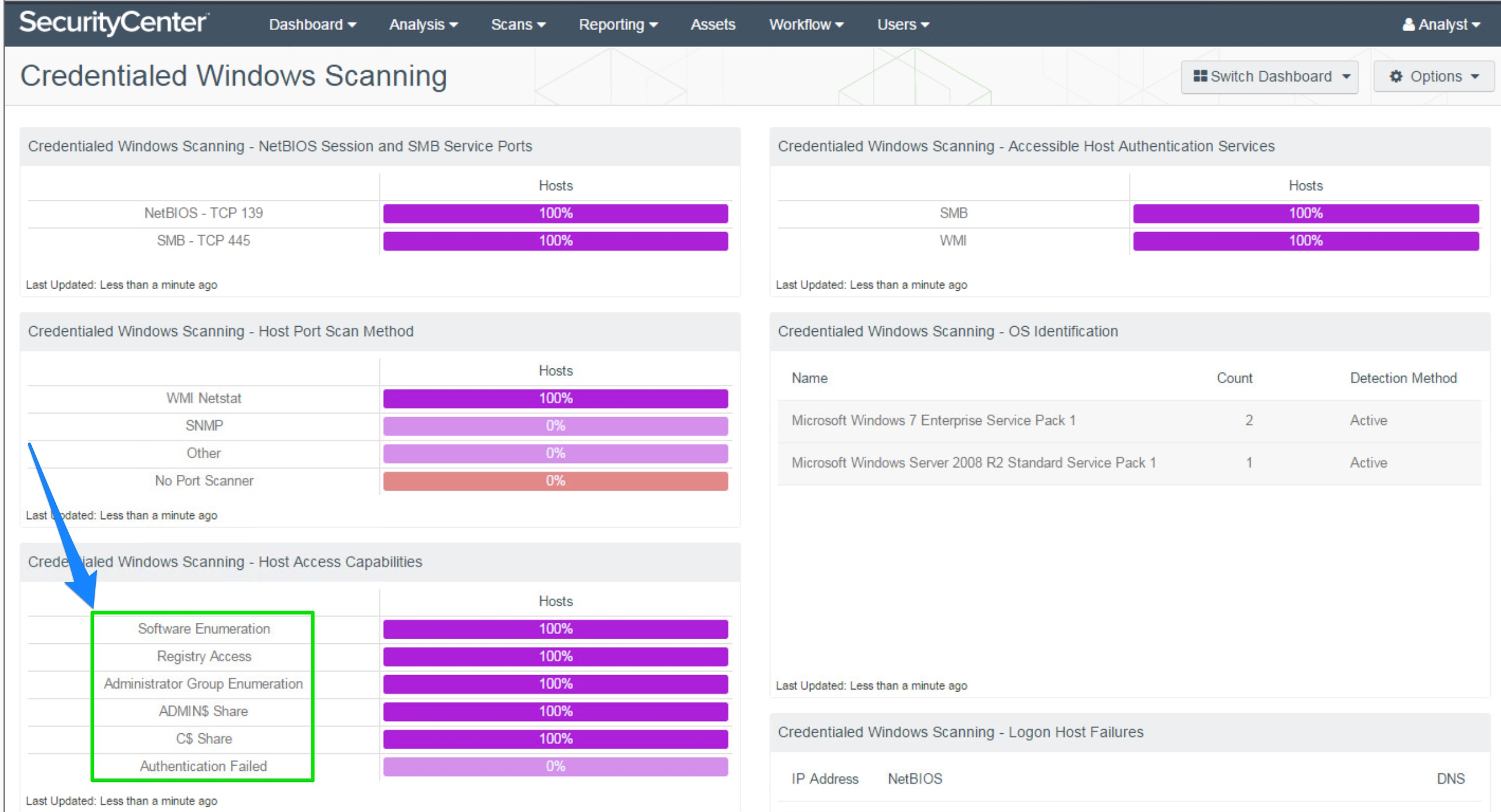
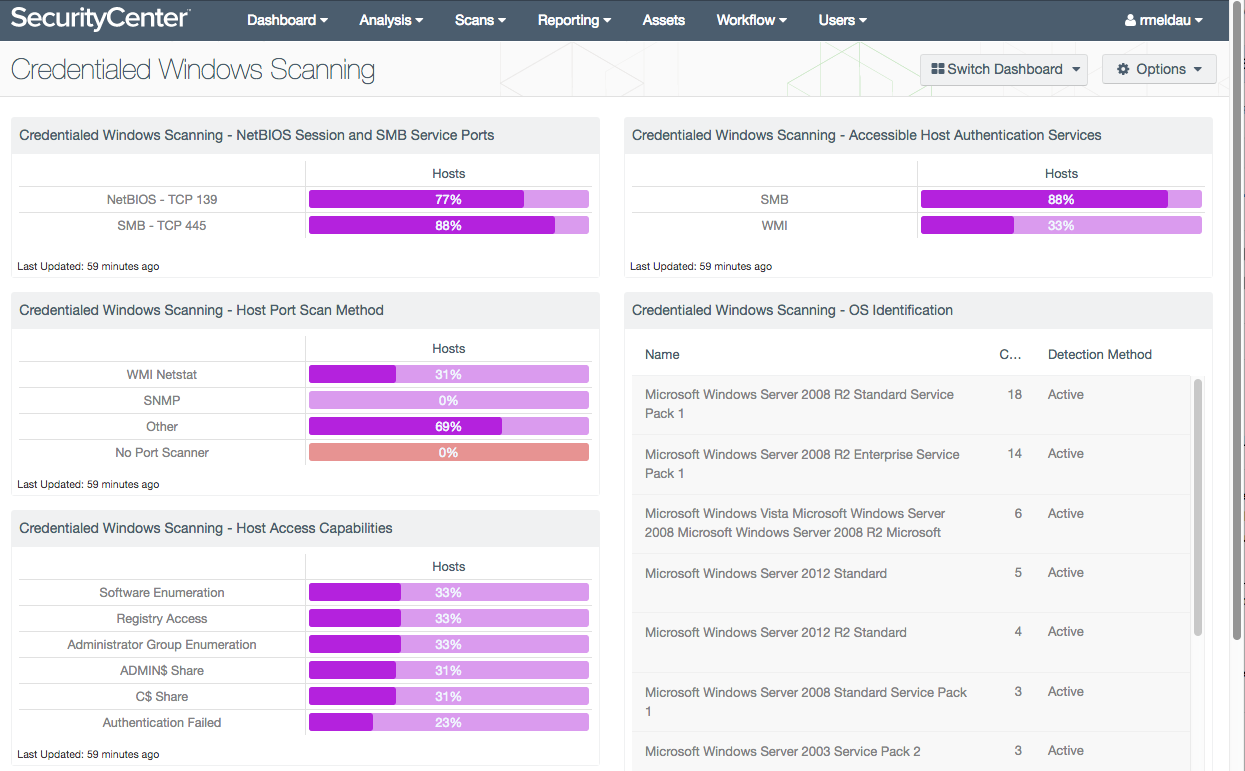
The Host Access Capabilities component in the Credentialed Windows Scanning dashboard shows some of the diagnostic results tested by QCD:
The QCD scan is built with tests recommended by Tenable customers and other sources. QCD works with Tenable scanning products: from Tenable.io™ and SecurityCenter® to Nessus® Manager and Professional. The scan contains a customized policy which includes specific tests or “plugins” (referenced by plugin id number in the Building the Scan section below). Note that “scan” and “scan policy” are used synonymously in this blog.
History of the QCD scan policy
When I first started working with Nessus and SecurityCenter, I scanned using vulnerability and compliance scans. Often, when scanning systems for the first time, I had authentication issues. I would make changes and then rerun the vulnerability scan. I did not like the load and the duration of the vulnerability scans; I realized I needed a debug scan, but did not have the time to figure out which plugins to include.
After joining Tenable, I worked with some savvy customers who had built a useful debug scan. I incorporated their selections with a few others in composing the QCD scan policy. QCD helps validate access to Windows and Linux targets. The QCD includes a short list of plugins so the scan runs quickly and with little impact on the target system.
To fix those scan access issues, QCD helps debug in two places: first, with scan credentials; second, with system access settings. Typically I may run QCD many times as I experiment with different settings until the scan runs cleanly.
For example, when my scan returns plugin Authentication Failure - Local Checks Not Run (21745), then I log into the target system’s service account manually. Once I have determined the correct login manually, I update the scan credentials. Then I run QCD to verify that the problem has been solved.
Another example is when I see the Microsoft Windows SMB Registry Not Fully Accessible Detection (10428) plugin, my next step is to turn on the registry service scan option. Then I run QCD to verify that the change solves the problem. Sometimes this process may take several iterations before all the systems are scanning without any issues.
Building the scan
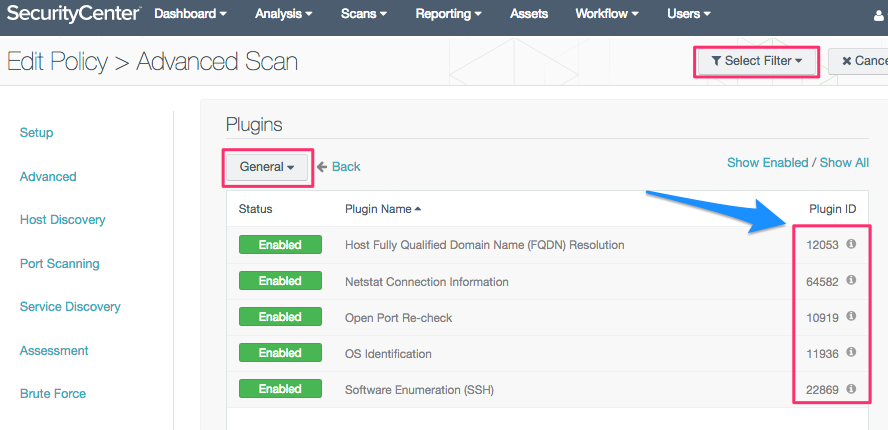
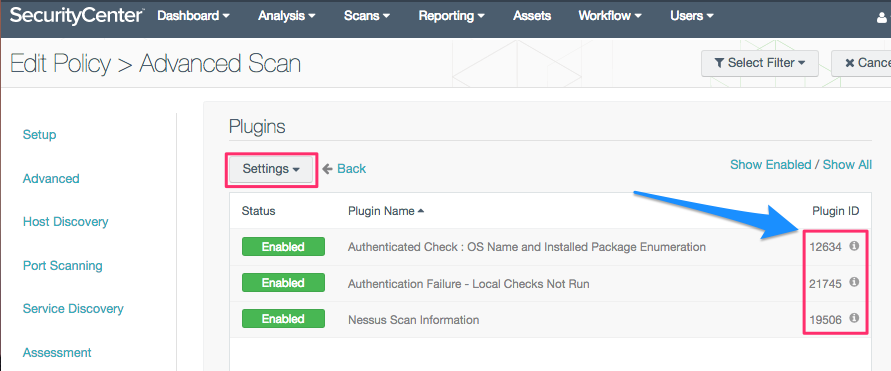
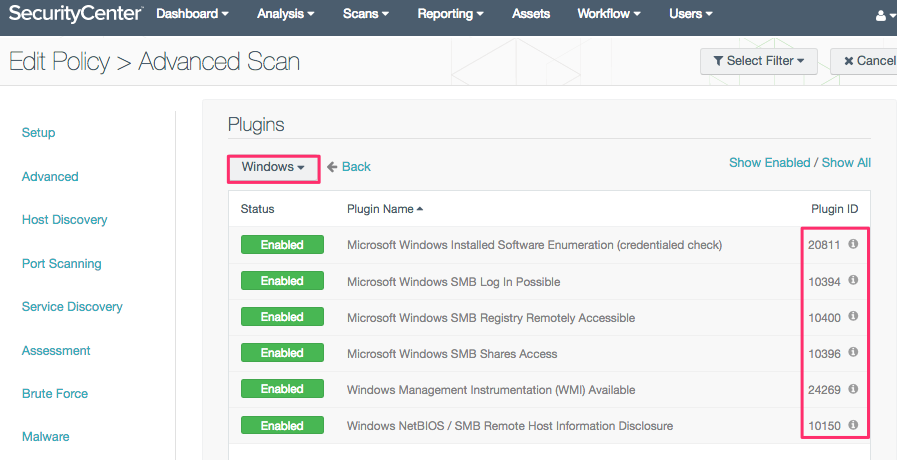
The custom QCD (Advanced) scan policy can be built by selecting a few individual plugins. The QCD scan pulls plugins from three families: General, Settings, and Windows.
These plugins provide the following functions:
- Login checks: 10394, 12634, 21745
- Access checks: 10400, 24269
- Software summary: 20811, 22869
- OS identification: 11936
- Other info: 10150, 10396, 10400, 10919, 12053, 19506, 64582
The QCD scan policy includes the following plugins (plugin id numbers are in parentheses):
- Windows family
- (10150) Windows NetBIOS / SMB Remote Host Information Disclosure
- (10394) Microsoft Windows SMB Log In Possible
- (10396) Microsoft Windows SMB Shares Access
- (10400) Microsoft Windows SMB Registry Remotely Accessible
- (20811) Microsoft Windows Installed Software Enumeration (credentialed check)
- (24269) Windows Management Instrumentation (WMI) Available
- General family
- (10919) Open Port Re-check
- (12053) Host Fully Qualified Domain Name (FQDN) Resolution
- (22869) Software Enumeration (SSH)
- (11936) OS Identification
- (64582) Netstat Connection Information
- Settings family
- (12634) Authenticated Check: OS Name and Installed Package Enumeration
- (19506) Nessus Scan Information
- (21745) Authentication Failure - Local Checks Not Run
The following SecurityCenter screenshots illustrate how to create the QCD. SecurityCenter provides a handy search filter which helps locate the plugins.
You can build this scan policy yourself or download the XML file available on the Tenable Community.
Other plugins can be included. Let us know what plugins you have found useful for debugging scan access on community.tenable.com.
Seeing the results
Two dashboard templates are helpful in looking at scan issues and the results from the QCD scans. The Credentialed Windows Scanning and Credentialed Linux Scanning dashboard display many of these plugin results. Remember to refresh the element after running the scan.
The Host Access Capabilities component in the bottom left of the Credentialed Windows Scanning dashboard lays out six of the most common access issues in the Windows environment. The Linux dashboard has similar checks.
Summary
Try the Quick Credential Debug scan to rapidly solve your scan access issues while reducing impact on the target systems. And share your observations with us at the Tenable Community!
- Nessus
- SecurityCenter
- Tenable Vulnerability Management
- Vulnerability Scanning