Public Exploit Modules Available for Cisco Prime Infrastructure Vulnerability

Users of Cisco Prime Infrastructure Software are urged to update to the latest version to address one of two vulnerabilities that, when chained, could lead to remote code execution with system-level permissions.
Contexte
Cisco released an advisory for CVE-2018-15379, an arbitrary file upload and command execution vulnerability for its Cisco Prime Infrastructure (CPI) software. The CPI management software is designed to allow businesses to manage their network device configurations all in one place, rather than individually by device. CPI also offers integration with Cisco Identity Services Engine (ISE) and location-based tracking through the Cisco Mobility Services Engine (MSE).
Vulnerability details
The CPI management tool has two vulnerabilities that, when exploited in tandem, could allow remote code execution. Pedro Ribeiro of Agile Information Security released a Proof of Concept (PoC) that outlines exploitation in greater detail. The researcher also states that exploit modules are publicly available for this vulnerability.
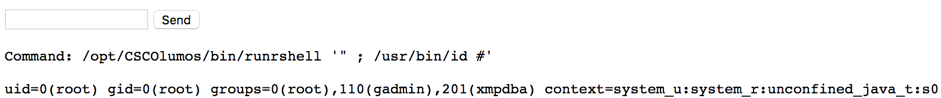
An attacker can first upload a JavaServer Page (JSP) web shell file using a Trivial File Transfer Protocol (TFTP) client to the /localdisk/tftp/ directory through the default TFTP port (port 69) to gain a shell as the "prime" user, which is unprivileged. From there, an attacker can inject commands through an unsanitized portion of the /opt/CSCOlumos/bin/runrshell binary to gain root access in their open shell.
Tenable researchers were also easily able to establish a web shell that accepted command input on a CPI target running version 3.2 in our lab. A standard id command displayed the status of the current user:

However, the privilege escalation can be easily demonstrated with this command:
Urgently required actions
Cisco has available workarounds, such as disabling the TFTP server listed in their advisory. However, we suggest updating to the fixed version (3.4.1) provided by Cisco. An important note is that this fix only addresses the TFTP file upload vulnerability. If an attacker were to gain access to the host in some other fashion that allows them to invoke the unsanitized binary, then the code execution vulnerability would still be exploitable.
Instructions for updating Cisco Prime Infrastructure Software are included in the advisory.
Identification des systèmes affectés
A list of Nessus plugins to identify this vulnerability can be found here.
En savoir plus
Learn more about Tenable.io, the first Cyber Exposure platform for holistic management of your modern attack surface. Get a free 60-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


