A Practitioner’s Perspective on Risk-Based VM: What People, Processes and Technologies Are Required?

Moving from legacy vulnerability management to a risk-based approach can be a paradigm shift, requiring not only new technologies, but changes in your existing processes and procedures. Here’s a brief overview of how you can get started.
Vulnerability management can often feel like a never-ending game of Whac-a-Mole. Fix one vulnerability and several more pop up elsewhere. As the number of new vulnerabilities continues to skyrocket, it’s become clear that legacy VM practices are no longer sufficient at keeping up and addressing the risks that matter most.
The problem is legacy VM tools are inefficient at best. They assess only traditional, on-premises IT environments, and their periodic scans don’t reflect the evolving threat landscape. They also lack the context you need to prioritize which vulnerabilities to remediate first.
Of course, this inefficiency didn’t happen overnight and isn’t the result of any one thing. Organizations have been slow to adapt to incremental changes in several different areas over time. Fortunately, the tools and best practices now exist to help your team quickly evolve your VM program to meet the demands of the modern attack surface.
Moving from reactive to proactive: The lifecycle for risk-based VM
As a general rule, you want to evolve from a highly reactive VM program, which is interrupt-driven and error-prone, to an approach that is proactive and strategic so you can maximize your efficiency and effectiveness. In other words, you need to get out of firefighting mode so you can focus on the vulnerabilities that pose the greatest risk. How can you accomplish this? In addition to investing in an expanded set of tools, your organization will need to update its VM policies and procedures to keep pace with evolving cyberthreats.
At Tenable, we think about this organizational process as a five-step lifecycle:
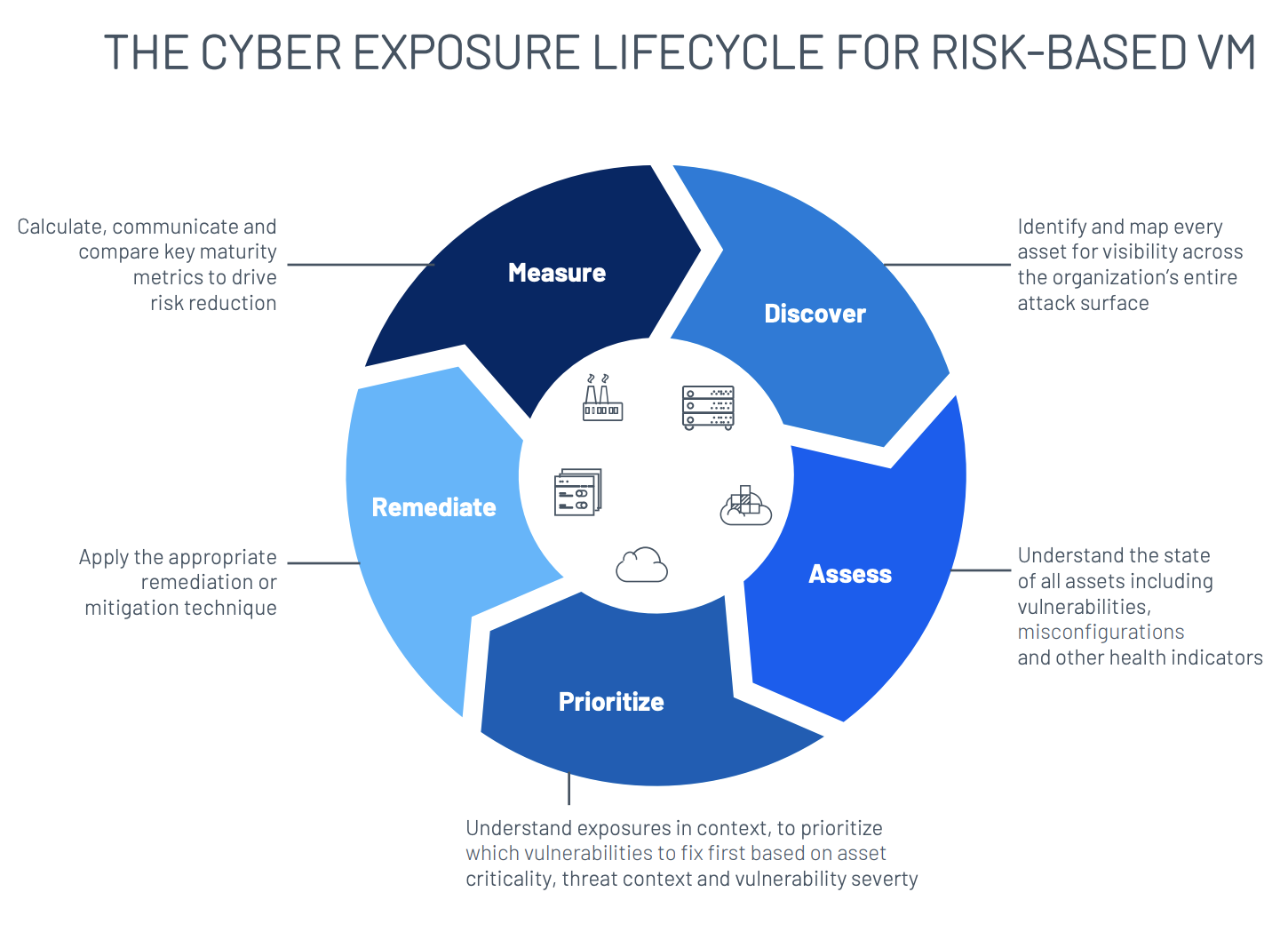
Rather than just discovering and assessing vulnerabilities, risk-based VM enables you to effectively prioritize them by understanding the full context of each vulnerability, determine the appropriate action to take, and calculate key metrics as well as compare against industry standards. A few of the many ways this can benefit your organization includes:
- Prioritize valuable security and IT resources
- Optimize the team’s efficiency
- Reduce business risk
- Minimize VM program costs
- Improve security reporting
- Build confidence across the C-suite
Discover critical business services across your attack surface
The first step in a risk-based VM strategy is to take the time to truly understand your business environment. That means determining and prioritizing business-critical services and applications, identifying service and application owners and other stakeholders, and evaluating existing security and applicable IT policies and processes.
You don’t necessarily need tools for this step, but you do need cooperation from the rest of your organization – particularly from the owners of all business-critical assets, applications and services. You need their permission to access their assets for scans, patching and other security measures. You also have to work out a schedule to ensure that your actions won’t interfere with the availability of their services.
Assess your network with frequent scans to eliminate blind spots
Next, you’ll need to fully assess all your assets. That means you’ll need a new scanner – one that can go beyond your traditional IT network to assess your entire attack surface, including any assets you have in cloud, operational technology (OT) and container environments. Having an integrated web app scanner is important too, since the majority of your organization’s sensitive data lives in, or runs through, apps – which has made the application layer a primary attack vector.
But simply upgrading your tools isn’t enough. You’ll also need to examine your security processes. Are you scanning enough of your network? Any assets your scanners can’t see puts you at risk from critical vulnerabilities that may reside on those assets. You also have to determine if you’re scanning frequently enough. Many organizations employing legacy VM methods scan monthly or less frequently. As a result, they’re basing their remediation decisions on old, outdated information. The threat landscape is dynamic in nature, so you’ll want your security intelligence to be dynamic, as well.
Prioritize vulnerabilities based on asset criticality and attacker activity
Once you can see all the vulnerabilities across your entire attack surface, you need to understand them in the context of business risk and use that data to prioritize your team’s efforts. That means you need a VM platform capable of analyzing the vulnerability data that comes from your scanners, together with other essential contextual elements, including the criticality of the affected assets and an assessment of current and likely future attacker activity.
Of course, analyzing all this data simply isn’t practical to do on your own. So, you’ll want your VM platform to employ automation and machine learning, so it’s capable of rendering an accurate decision in seconds.
As you continue to refine your prioritization strategy, make sure your assessment windows work well for each asset to minimize business disruptions while achieving reasonable service-level agreements (SLAs). This is tied to the work you did in step 1, when you took the time to understand the business environment and established agreements on patch windows. After all, achieving your SLAs is meaningless if the cost to the business is greater than the benefit of the fix.
Remediate or mitigate critical vulnerabilities
Once you’ve determined which vulnerabilities are the highest priority, you’ll want your VM platform to tightly integrate with your ticketing system so you can send tickets directly to IT, pre-populated with the information they’ll need to understand what to fix, how to fix it and why it’s a priority. Les fonctionnalités de création de tickets automatique simplifient encore le processus et le rendent plus efficace.Communications should also be bi-directional so IT can initiate scans to validate their remediations.
Keep in mind that you can’t remediate everything, and doing so isn’t necessarily the best use of your security resources. Instead, you’ll want to determine the implications of remediating each prioritized vulnerability. Is remediation feasible? If not, are mitigation factors in place that reduce or neutralize the threat exposure? Can you afford to simply accept the risk and take no action at all? Risk acceptance may be appropriate if the vulnerability is on a non-critical asset, or it may be necessary if the remediation runs the risk of breaking critical processes that are running on the asset.
In many cases, you’ll need to get agreement from each asset owner on your response plan before you take any action. And once you perform the remediation, you’ll need to validate its effectiveness before moving on to the next vuln.
Measure to communicate your security progress
Finally, you need a rich set of reporting and analysis tools to effectively communicate the team’s efficiency – to gain and maintain management’s confidence in your abilities. Outre le recours aux outils, vous devez travailler avec les différents groupes de sécurité de l'entreprise pour développer des dashboards communs garantissant un reporting cohérent.You’ll also need to work with your management to decide when and how often reporting should occur.
As with most of the prior steps we’ve discussed, the weaknesses you’ll need to address here are on the human side, rather than with the technology. You’ll need to decide as an organization what KPIs are most important, so each team can deliver consistent reports that can be easily rolled up to encompass multiple areas of responsibility, or even the company as a whole, so that the CISO can clearly report your progress to the board.
Risk-based VM is the foundation of a modern security strategy
Implemented correctly, a risk-based VM strategy can help you prioritize your remediation efforts to focus first on the assets and vulnerabilities that matter most. As a result, you’ll be able to make the most efficient use of your limited security resources by reducing the greatest amount of risk with the least amount of effort. This newfound efficiency will free some of your most senior resources to work on more strategic security initiatives.
Want to learn how to put this framework into practice? Download our whitepaper, Reference Architecture: Gestion des vulnérabilités basée sur le risque
- Risk-based Vulnerability Management
- Tenable Vulnerability Management (DO NOT USE)
- Vulnerability Management
- Vulnerability Scanning



