Oracle Critical Patch Update for October 2020 Addresses 402 Security Updates

Oracle’s latest Critical Patch Update surpasses the 400 mark for the second time this year with 402 security patches addressing 230 CVEs, including numerous critical vulnerabilities in Oracle Fusion Middleware products.
Background
On October 20, Oracle released the Critical Patch Update (CPU) Advisory for October 2020, its final quarterly release of security patches for the year. This update contains fixes for 230 CVEs in 402 security patches across 27 Oracle product families. This quarter’s update marks the second-highest count in Oracle CPUs, surpassed only by the July 2020 update which holds the record with over 440 patches.
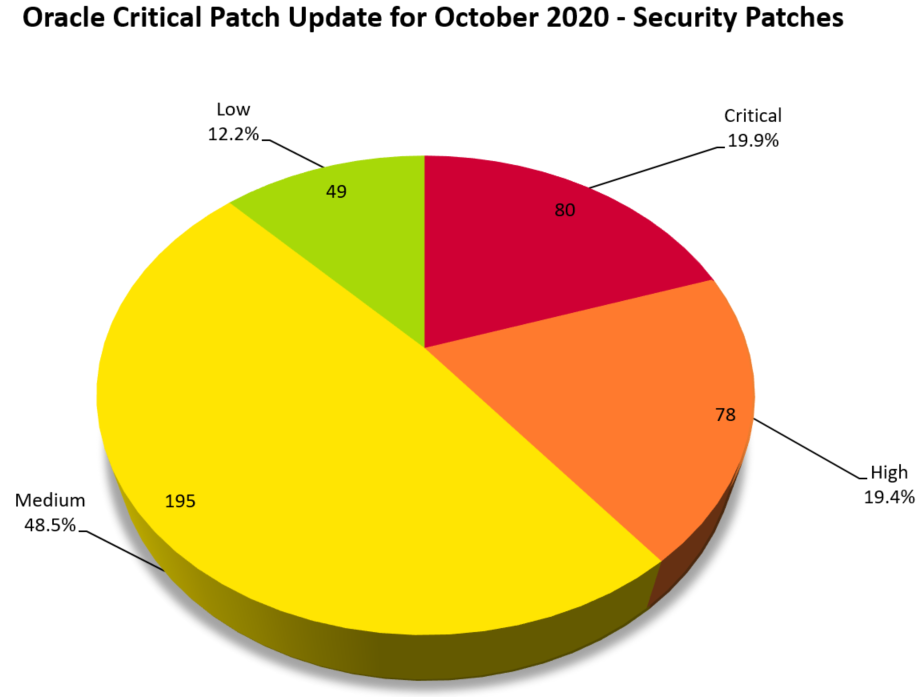
* Chart is accurate as of October 21, 2020
Analysis
This quarter’s CPU includes 35 critically rated CVEs across a wide range of Oracle products. The table below lists the product families with vulnerabilities addressed in this month’s release along with the number of vulnerabilities that are remotely exploitable without authentication.
| Oracle Product Family | Number of Patches | Remote Exploit without Auth |
|---|---|---|
| Oracle Financial Services Applications | 53 | 49 |
| Oracle MySQL | 53 | 4 |
| Oracle Communications | 52 | 41 |
| Oracle Fusion Middleware | 46 | 36 |
| Oracle Retail Applications | 28 | 25 |
| Oracle E-Business Suite | 27 | 25 |
| Oracle Database Server | 18 | 4 |
| Oracle PeopleSoft | 15 | 12 |
| Oracle Enterprise Manager | 11 | 10 |
| Oracle Communications Applications | 9 | 8 |
| Oracle Construction and Engineering | 9 | 7 |
| Oracle Hyperion | 9 | 1 |
| Oracle Java SE | 8 | 8 |
| Oracle Systems | 8 | 3 |
| Oracle Virtualization | 7 | 0 |
| Oracle Hospitality Applications | 6 | 3 |
| Oracle Insurance Applications | 6 | 6 |
| Oracle Policy Automation | 6 | 6 |
| Oracle REST Data Services | 5 | 2 |
| Oracle Utilities Applications | 5 | 3 |
| Oracle TimesTen In-Memory Database | 4 | 4 |
| Oracle Food and Beverage Applications | 4 | 3 |
| Oracle Health Sciences Applications | 4 | 4 |
| Oracle Supply Chain | 4 | 3 |
| Oracle Siebel CRM | 3 | 3 |
| Oracle Big Data Graph | 1 | 1 |
| Oracle GraalVM | 1 | 1 |
* Table is accurate as of October 21, 2020
Notable Vulnerabilities
Considering the large number of patches released in this CPU, it may be hard to digest, filter and prioritize these vulnerabilities. However, a few Oracle WebLogic Server vulnerabilities are of note due to their criticality and potential for being targeted by attackers.
CVE-2020-14825, CVE-2020-14841, CVE-2020-14859 | Oracle WebLogic Server - Component: Core
CVE-2020-14825, CVE-2020-14841 and CVE-2020-14859 are vulnerabilities in the Core component of Oracle WebLogic Server. Oracle has classified these vulnerabilities as “easily exploitable” as they would allow an unauthenticated attacker with network access via Oracle’s T3 or Internet Inter-ORB Protocol (IIOP) to compromise the server. All three vulnerabilities affect versions 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.0. CVE-2020-14841 and CVE-2020-14859 also affect versions 10.3.6.0.0 and 12.1.3.0.0.
CVE-2002-14841 Proof of Concept
On October 21, security researcher Hamid Kashfi shared a proof of concept (PoC) for CVE-2020-14841 in a tweet stating “Another Oracle Tomcat JNDI bypass: CVE-2020-14841.”
Another Oracle Tomcat JNDI bypass: CVE-2020-14841
— Hamid K (@hkashfi) October 21, 2020
PoC: https://t.co/xETErLhzPr
CVE-2020-14882 | Oracle WebLogic Server - Component: Console
CVE-2020-14882 is a vulnerability in the Console component of Oracle WebLogic Server. Oracle has highlighted this vulnerability as “easily exploitable” as it would allow an unauthenticated attacker to compromise the Oracle WebLogic server over HTTP resulting in the takeover of the targeted server. This vulnerability affects versions 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.0.
CVE-2019-17267 | Oracle WebLogic Server - Component: Centralized Thirdparty Jars (jackson-databind)
CVE-2019-17267 is a vulnerability in the Centralized Thirdparty Jars (jackson-databind) component of Oracle WebLogic Server. Oracle notes that this vulnerability is “easily exploitable” and would allow an unauthenticated attacker with network access over HTTP to compromise and take over a targeted server. Version 12.2.1.3.0 is the only version affected by this vulnerability.
Oracle has assigned all five of the vulnerabilities discussed in this section a CVSSv3.1 score of 9.8 due to their impact and ease of exploitation. Oracle WebLogic Server vulnerabilities have appeared in every Oracle CPU this year.
Oracle WebLogic Servers have always been a prime target for threat actors. On April 30,, Oracle published a blog post warning of in-the-wild exploitation of CVE-2020-2883, a deserialization vulnerability in the Oracle Coherence library of Oracle WebLogic Server that was patched in the April 2020 Oracle CPU. CVE-2020-2883 is a patch bypass of CVE-2020-2555, another deserialization vulnerability in Oracle Web Server, which was included in the January 2020 CPU.
Less than a week after the July 2020 Oracle CPU, a PoC was released for CVE-2020-14645, another vulnerability affecting the Core component of Oracle WebLogic Server. Based on this consistent interest in WebLogic Server from threat actors and researchers, we expect to see additional patches and perhaps PoCs for this product in the future.
Solution
Customers are advised to apply all relevant patches in this CPU. Please refer to the October 2020 advisory for full details.
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities will appear here as they’re released.
Get more information
- Oracle Critical Patch Update Advisory - October 2020
- Oracle Advisory to CVE Map
- Oracle October 2020 CPU Risk Matrices
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management



