Duplicator WordPress Plugin Vulnerability Exploited in the Wild

Attackers are targeting a recently patched flaw in a popular WordPress plugin with over 1 million active installations.
Contexte
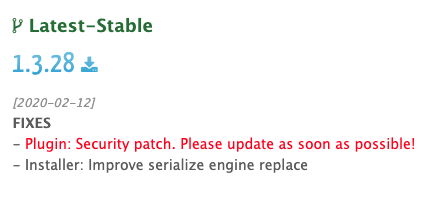
On February 12, Snap Creek, makers of the popular WordPress plugin Duplicator, released version 1.3.28 and Duplicator Pro version 3.8.7.1 to address a serious vulnerability.
Duplicator is a plugin used by WordPress site administrators to “migrate and copy WordPress sites.” According to statistics from WordPress.org, Duplicator has over 1 million active installations, and according to Snap Creek, it has been downloaded over 15 million times.
Analyse
According to researchers at Wordfence, an unauthenticated arbitrary file download vulnerability exists in Duplicator versions 1.3.26 and below and Duplicator Pro versions 3.8.7 and below.
The vulnerability exists due to the implementation of a pair of functions, duplicator_download and duplicator_init. The functions can be accessed by unauthenticated users because they were implemented using the wp_ajax_nopriv_ hook. Researchers note that because the functions were “hooked into init,” they would be executed on every WordPress page that’s loaded, whether the user is logged in or not.
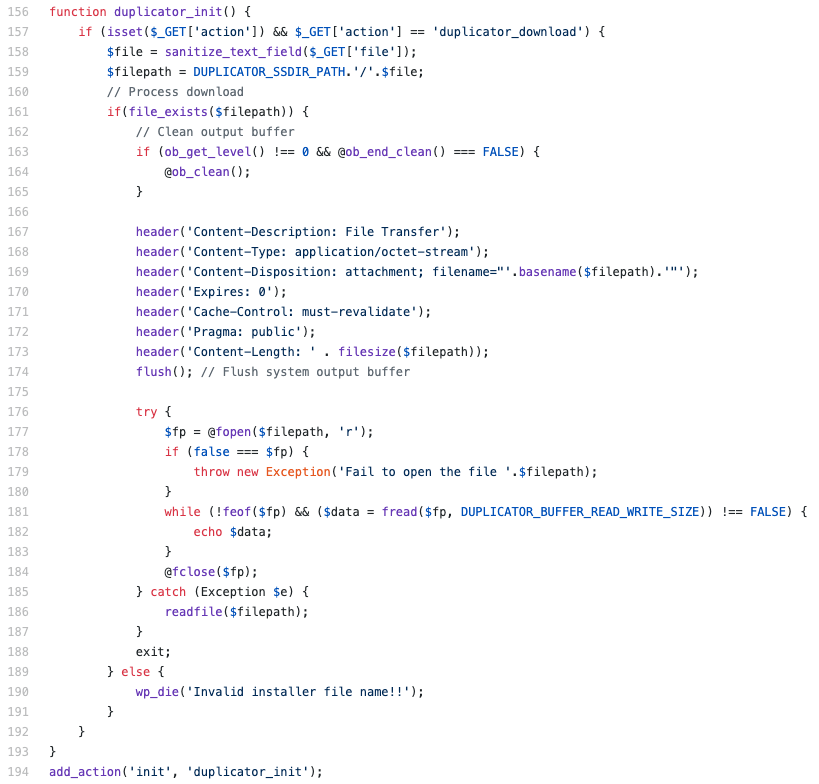
Within these functions, the file parameter was sanitized but not validated, so an attacker could use path traversal to access files outside of Duplicator’s specified path.
An unauthenticated, remote attacker could exploit this vulnerability by sending a specially crafted request to a WordPress site using the vulnerable version of the Duplicator plugin. This would allow them to download files outside of the intended directory. An attacker would need some knowledge of the target file structure or attempt to download commonly known files.
![]()
These files could include the wp-config.php file, referred to as “one of the most important files” in a WordPress installation. This is because the configuration file contains database credentials and authentication keys and salts. An attacker could use this information to create their own administrator account on the vulnerable site or “inject content or harvest data.”
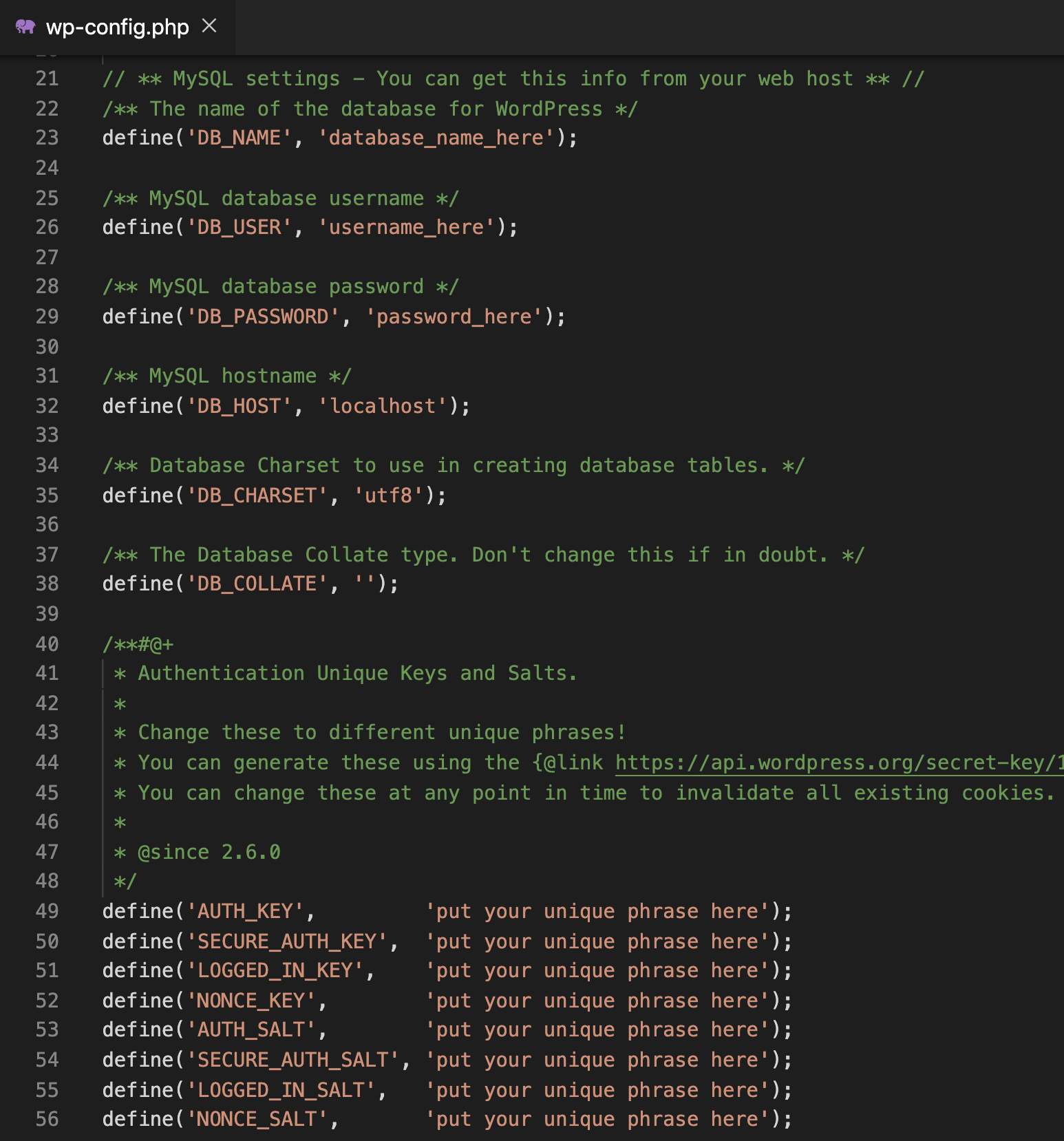
Wordfence has reportedly blocked over 60,000 attempts to download the wp-config.php file using this vulnerability. They note that of the 60,000 attempts, 50,000 occurred before February 12, prior to Snap Creek releasing a fix for the vulnerability, indicating this was exploited in the wild as a zero-day.
Démonstration de faisabilité (PoC)
At the time this blog post was published, there was no proof of concept (PoC) available for this vulnerability. However, there is enough information available in Wordfence’s blog post along with the indicators of compromise to easily craft a PoC.
Solution
Snap Creek addressed this vulnerability in Duplicator version 1.3.28 and Duplicator Pro version 3.8.7.1 on February 12. Duplicator and Duplicator Pro users are strongly encouraged to upgrade to versions 1.3.28 and 3.8.7.1 or greater as soon as possible.
Wordfence provided indicators of compromise to identify attacks exploiting this vulnerability. The bulk of the attacks they’ve seen originate from the following IP address:
- 77.71.115.52
Additionally, review HTTP logs for requests that include the following query strings:
- action=duplicator_download
- file=/../wp-config.php
The most reliable indicator is whether the request contains the file parameter, as that is required to exploit this vulnerability.
Identification des systèmes affectés
Une liste de plug-ins Tenable permettant d'identifier cette vulnérabilité apparaîtra ici au fur et à mesure de leur publication.
En savoir plus
Rejoignez l'équipe SRT de Tenable sur Tenable Community.
Apprenez-en plus sur Tenable, la première plateforme de Cyber Exposure qui vous permet de gérer votre surface d'attaque moderne de manière globale.
Profitez d'un essai gratuit de 30 jours de Tenable.io Vulnerability Management.
- Vulnerability Management

