DNSpooq: Seven Vulnerabilities Identified in dnsmasq

Researchers identify seven vulnerabilities in popular Domain Name System software.
Background
On January 19, researchers from the JSOF Research lab disclosed seven vulnerabilities in dnsmasq, a widely used open-source application for network infrastructure. Dubbed “DNSpooq” by the JSOF team, the acronym is a play on words as the vulnerabilities allow for Domain Name System (DNS) spoofing. The JSOF team also released a detailed whitepaper with technical details around their research.

Image Source: JSOF
The vulnerabilities were discovered over the summer of 2020 and JSOF coordinated with the CERT Coordination Center (CERT/CC) and various other entities to alert vendors that implement dnsmasq within their own products and services.
While JSOF notes that over 40 vendors may be affected by these flaws, due to varying implementations, it is unclear which vendors may be impacted by these vulnerabilities or if they are impacted at all.
Analysis
The seven flaws that comprise of DNSpooq can be split into two categories of vulnerabilities: DNS cache poisoning and buffer overflow. While it is possible that the buffer overflow vulnerabilities can be used to gain remote code execution (RCE), the more likely scenario is a denial of service (DoS) condition when successfully exploited.
Poison the Well: DNS Cache Poisoning Attacks
The researchers identified the following three DNS Cache Poisoning vulnerabilities:
| CVE | Impact | CVSSv3 |
|---|---|---|
| CVE-2020-25684 | DNS Cache Poisoning | 4 |
| CVE-2020-25685 | DNS Cache Poisoning | 4 |
| CVE-2020-25686 | DNS Cache Poisoning | 4 |
All three vulnerabilities are the result of DNS cache poisoning, a type of attack that could allow an attacker to inject a malicious DNS entry into the cache, which could be used to redirect network packets to a malicious server. This particular type of attack can be abused to re-route traffic including HTTP, SSH, remote desktop protocol and others.
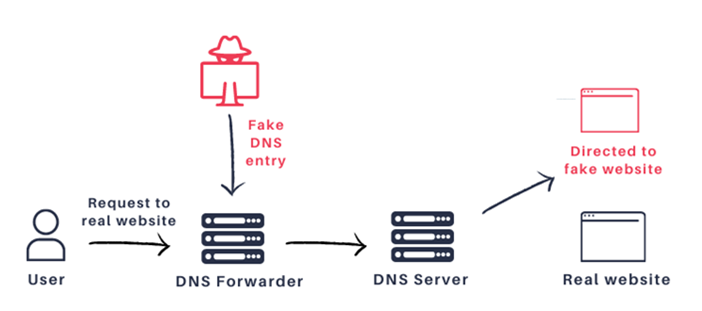
Image Source: JSOF
The cache poisoning attacks are made possible by abusing a weak hash to reduce entropy. The transaction ID (TXID) and source port should be random and provide 32 bits of entropy, however JSOF found that the hashing algorithm used is not cryptographically secure and an attacker could abuse this to reduce the entropy significantly. When DNS Security Extensions (DNSSEC) is disabled, a custom CR32 algorithm is used for hashing.
The research outlines at least three potential scenarios in which an attacker could exploit the flaws. The first scenario outlines the potential to attack a dnsmasq resolver that has port 53 open to the internet. This would allow an attacker to send crafted DNS packets using a spoofed IP address and a registered domain name. JSOF believes “approximately 1 million vulnerable dnsmasq instances” are vulnerable according to a Shodan search.
The second and more likely scenario would be an attacker abusing the flaws from a machine an attacker controls within the local area network (LAN). While an attacker with access to a machine within a LAN can likely leverage other vulnerabilities more easily, this scenario could be exploited by an insider threat. The attacker could impact all devices connected to the LAN and redirect traffic to steal confidential or sensitive information.
The third and most complex scenario involves using malicious JavaScript to attempt to inject malicious DNS queries within the local LAN when a user on that same LAN browses an attacker-controlled website or a website with malicious advertisements. JSOF notes in their whitepaper that not all browsers allowed for this attack scenario, and there could be other mitigating factors on a network that would prevent this attack from being successful.
Over the Top: Buffer Overflow Flaws
The four remaining flaws in the table below are buffer overflow vulnerabilities:
| CVE | Potential Impact | CVSSv3 |
|---|---|---|
| CVE-2020-25681 | Remote Code Execution, Denial of Service | 8.1 |
| CVE-2020-25682 | Remote Code Execution, Denial of Service | 8.1 |
| CVE-2020-25683 | Remote Code Execution, Denial of Service | 5.9 |
| CVE-2020-25687 | Remote Code Execution, Denial of Service | 5.9 |
CVE-2020-25681 and CVE-2020-25862, the two highest rated flaws earning an 8.1 CVSSv3 score, could be abused to achieve RCE. However, as is the case with the other CVEs listed in this advisory, the most likely scenario would be a DoS condition.
DNSSEC: When the Cure Becomes Worse Than The Disease
In a bit of irony, in order for a device to be affected by the four buffer overflow vulnerabilities, the DNSSEC feature must be enabled. Devices with DNSSEC disabled would NOT be affected by the buffer overflow flaws. However, JSOF notes it is important to enable DNSSEC as it is used to prevent cache poisoning attacks.
Chaining attacks to increase effectiveness
While the highest rated CVSS score is an 8.1 and the lowest being only a 4, JSOF notes that these vulnerabilities by themselves are low impact. However, chaining one or more of the vulnerabilities together can give an attacker a more robust attack with a much higher impact. While chained attack scenarios have become more common lately, it does highlight how important every component within a network can be. With DNS being a major backbone of the internet, these seven vulnerabilities highlight that common protocols and network software are a prime target for skilled threat actors.
Proof of concept
At the time this blog post was published, no proof-of-concept (PoC) code had been made available for any of these vulnerabilities. Based on the complexity in some environments, we don’t anticipate to see a reliable PoC in the near future.
Solution
To address these vulnerabilities, version 2.83 of dnsmasq has been released. When this blog was published, it was not clear if each of the vendors contacted through coordination with CERT/CC and JSOF have responded. However, we expect patches for various software from multiple vendors and network hardware to be released over time.
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities will appear here as they’re released. We have also released an audit and compliance check that can be obtained from our GitHub page.
For our standalone plugin for dnsmasq, identified as plugin ID 145073, users are required to enable the “Show potential false alarms” setting, also known as paranoid mode, in their scan policy in order to enable this plugin in a scan.
We also recommend enabling only this specific plugin in a paranoid scan. Scan policies configured to have all plugins enabled will see an increase in the number of triggers, as it will include all paranoid plugins during the scan.
Enabling Paranoid Mode
To enable this setting for Nessus and Tenable.io users:
- Click Assessment > General > Accuracy
- Enable the “Show potential false alarms” option
To enable this setting for Tenable.sc (formerly SecurityCenter) users:
- Click Assessment > Accuracy
- Click the drop-down box and select “Paranoid (more false alarms)”
Get more information
- JSOF Blog post for DNSpooq
- JSOF Technical Whitepaper
- US CERT ICS Advisory (ICSA-21-019-01)
- CERT Coordination Center Vulnerability Note VU#434904
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


