Cybersecurity Snapshot: The Latest on Supply Chain Security – SBOM Distribution, Open Source Flaws and a New Security Framework

Check out what CISA says about the sharing of software bills of materials. Plus, why you should tread carefully with open source components. Also, the SLSA supply chain security framework is ready. In addition, security worries hold back enterprise IoT adoption. And much more!
Dive into six things that are top of mind for the week ending April 21.
1 – CISA shines spotlight on SBOM sharing methods
They say sharing is caring, and this week the U.S. Cybersecurity and Infrastructure Security Agency (CISA) turned its attention to how to better distribute software bills of materials (SBOMs).
Because they list the “ingredients” in a software product, SBOMs are key for supply chain security. With SBOMs, security teams can identify unsafe components in their organizations’ software. (Cue your memories of scrambling to find all Log4j instances in your environment.)
Due to regulatory and industry pressure, software producers are making SBOMs more prevalent and sophisticated. Now CISA is looking at ways to streamline SBOM sharing with its “Software Bill of Materials Sharing Lifecycle Report”.
“The purpose of this report is to enumerate and describe the different parties and phases of the SBOM sharing lifecycle and to assist readers in choosing suitable SBOM sharing solutions,” reads the 23-page document.
CISA breaks down the SBOM-sharing lifecycle into three phases: discovery, access and transport. It describes three levels of sophistication for each – low, medium and high – and offers examples of SBOM-sharing solutions.
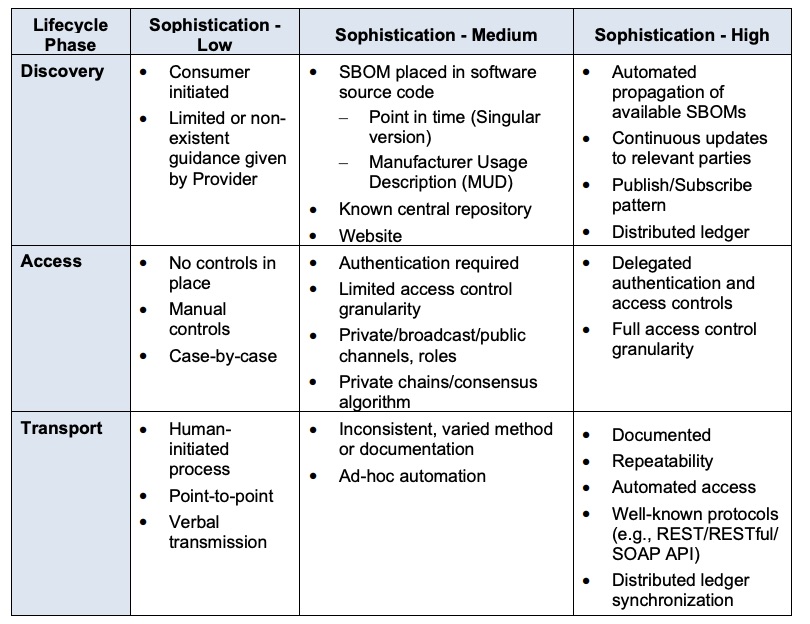
(Source: CISA’s “Software Bill of Materials Sharing Lifecycle Report”, April 2023)
For more information about SBOMs:
- “Software bill of materials: Managing software cybersecurity risks” (McKinsey)
- “Securing the Software Supply Chain: Recommended Practices for Developers” (U.S. National Security Agency)
- “The State of Software Bill of Materials (SBOM) and Cybersecurity Readiness” (Linux Foundation)
- “The White House wants new transparency into software components” (Protocol)
- “Federal Vendors Given a Year to Craft SBOM To Guarantee Secure Software Development” (CPO Magazine)
VIDEOS
Understanding the Role of Software Bill of Materials in Cybersecurity Readiness (Linux Foundation)
SBOM is Coming: Why You Should Care and How You Can Help (Cloud Native Computing Foundation)
2 – Insecure open source components create supply chain risks
Here’s another reminder to be careful and perform due diligence when using open source software (OSS) components in your applications.
After analyzing almost 42,000 OSS components from the 44 most popular Apache Software Foundation projects, supply chain security management vendor Lineaje found that:
- Direct software dependencies – those your code calls directly and overtly, and are thus easy to track and manage – make up only 10% of all OSS components
- The other 90% are so-called transitive, or indirect, dependencies, which are those called by your direct dependencies, or by other indirect dependencies
Transitive dependencies are less visible, and thus more difficult to detect and check for security issues, such as unpatched vulnerabilities.

Lineaje, an early-stage startup in which Tenable Ventures is investing, also found in its analysis that:
- 68% of the analyzed OSS components weren’t developed under the Apache Software Foundation umbrella
- 82% of the OSS components are “inherently risky” because of vulnerabilities, security issues, weak code quality and concerns about their maintenance
- Slightly over 64% of vulnerabilities detected in these OSS components can’t be fixed because no patches have been released for them
- Another almost 26% of the vulnerabilities do have fixes but are in “deep transitive dependencies” which developers can’t patch
- 3% of the OSS components were of unknown origin, and 5.3% came from a “dubious” origin
For more details, download Lineaje’s report “What’s in Your Open Source Software?” and check out an infographic.
For more information about OSS security:
- “U.S. Congress tackles open source software security” (Tenable)
- “The Open Source Software Security Mobilization Plan” (The Linux Foundation and The Open Source Security Foundation)
- “Software Supply Chain Best Practices” (Cloud Native Computing Foundation)
- “Are You Ready for the Next Log4Shell? Tenable’s CSO and CIO Offer Their Advice” (Tenable)
- “8 notable open-source security initiatives of 2022” (CSO Magazine)
VIDEO
Open Source Security and the OpenSSF’s Best Practices WG (Open Source Security Foundation)
3 – Version 1.0 of supply chain security spec SLSA is out
And clearly this week we’ve got a fever and the only prescription for it is more cowbell – sorry, more supply chain security news!
The Open Source Software Security Foundation (OpenSSF) this week issued the “stable release” version 1.0 of the Supply Chain Levels for Software Artifacts framework, better known as SLSA.
In the works for about two years, SLSA provides specs and guidelines for protecting software supply chains, which have become an attractive target for attackers. In these attacks, a threat actor stealthily compromises a software product that its maker then unwittingly distributes to its users via legit channels, as happened in the SolarWinds breach.

Version 1.0 represents a significant development of the framework, including changes intended to make it easier to adopt, according to OpenSSF. Specifically, SLSA’s level requirements, previously in a single track, are now split into multiple tracks – each focused on one area of the software supply chain.
SLSA aims to help both software makers and users by providing:
- A common vocabulary for software supply chain security
- A way to evaluate the integrity of the software artifacts you use
- An actionable security checklist
- A way to measure compliance efforts
To get more details about SLSA 1.0:
- Read the OpenSSF’s announcement
- Find out what’s new in version 1.0
- Visit SLSA 1.0’s main page
- Check out coverage from SDXCentral, The New Stack and CSO Magazine.
4 – Are you consolidating cyber vendors? If so, why?
Those were two questions we asked participants at a recent Tenable webinar about the benefits of a unified exposure management platform. Check out how they answered.
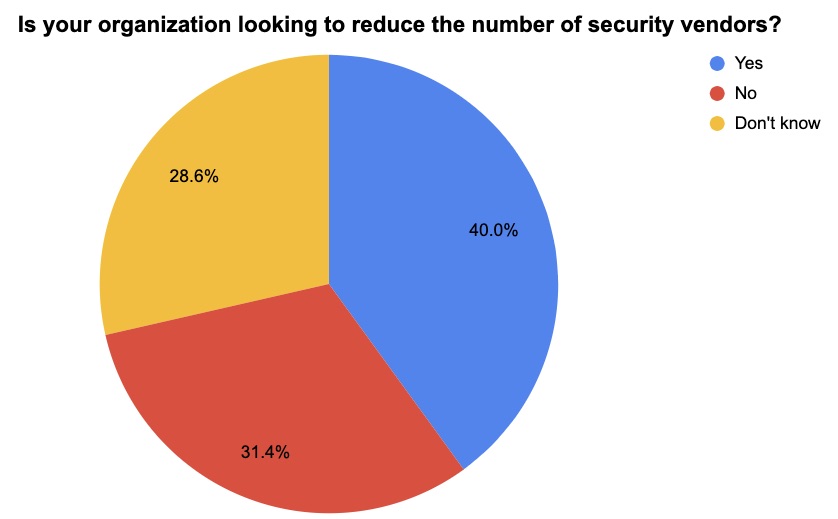
(Source: 35 webinar attendees polled by Tenable, March 2023)
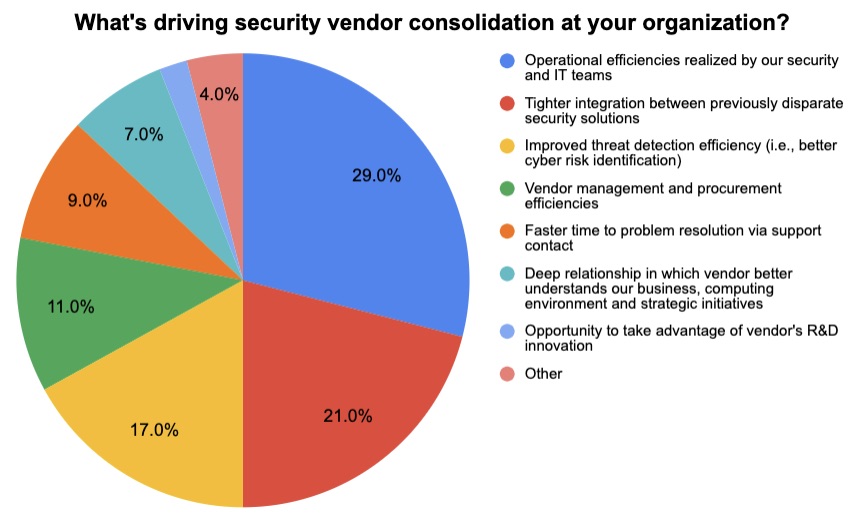
(Source: 37 webinar attendees polled by Tenable, March 2023. Respondents could choose more than one answer.)
For more information about cyber vendor consolidation and exposure management platform benefits, check out these Tenable resources:
- “Exposure Management: 7 Benefits of a Platform Approach” (blog)
- “Seven Benefits of a Unified Exposure Management Platform” (on-demand webinar)
- “3 Real-World Challenges Facing Cybersecurity Organizations: How an Exposure Management Platform Can Help” (white paper)
- “The shift to integrated cybersecurity platforms: a growing trend among CISOs” (blog)
5 – McKinsey: Cybersecurity flaws hinder IoT adoption
Cybersecurity concerns remain a drag on the use of internet of things (IoT) products by businesses.
Security flaws and weaknesses ranked as the top impediment to IoT adoption by enterprises, according to a McKinsey survey of enterprise tech buyers.
Specifically, 32% of 117 respondents cited cybersecurity as the main roadblock for IoT adoption and spending. These respondents indicated they would boost their IoT budget and deployment by 25% or more if their cybersecurity concerns were addressed.
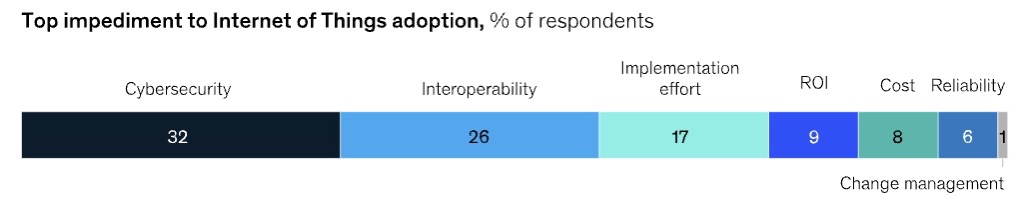 (Source: McKinsey’s “Cybersecurity for the IoT: How trust can unlock value”, April 2023)
(Source: McKinsey’s “Cybersecurity for the IoT: How trust can unlock value”, April 2023)
“Cybersecurity risk multiplies due to the interconnectedness of IT and operational technology within the IoT, especially in use cases that involve the transmission of critical data or the operation of critical business processes,” reads a McKinsey article about the survey results.
For more information about IoT cybersecurity challenges and best practices:
- “Vendors of IoT products must step up vulnerability disclosures” (Tenable)
- “The dark web’s criminal minds see Internet of Things as next big hacking prize” (CNBC)
- “IoT Security Assurance Framework” (IoT Security Foundation)
- “Three strategies for navigating the fragmented IoT security ecosystem” (IoXT Alliance)
VIDEO
Do IoT Devices Make Your Network Unsecure? (Cyber Gray Matter)
6 – How to protect quantum computers from cyberattacks
When cybersecurity experts discuss quantum computers, which are expected to ship by 2030, they focus on how attackers could use these super-powerful machines to cause mayhem, such as to break public-key cryptographic algorithms and steal confidential data.
Less attention has been paid to how organizations that in the future use these systems for legitimate purposes should protect them from attackers. That’s the topic of the article “Cybersecurity of Quantum Computing: A New Frontier” from Carnegie Mellon University’s Software Engineering Institute (SEI).
“If quantum computers are to become such valuable assets, it is reasonable to project that they will eventually be the target of malicious activity,” wrote Thomas Scanlon, senior cybersecurity engineer and researcher at SEI’s Computer Emergency Readiness Team (CERT) division.

Scanlon outlines six key areas for future quantum security research:
- Building large-scale secure control systems to prevent intrusions
- Securing high-performance multitenant and distributed systems
- Understanding potential attack vectors
- Developing formal safety and security computing methods
- Constructing a multi-layered instrumentation framework
- Developing tools to verify and control quantum algorithms
“Increased quantum deployment will raise many technical questions about how data is prepared and transferred to quantum computers, how algorithms are implemented in quantum computers, and how quantum computing results are returned and verified,” Scanlon writes.
For more information about quantum computing’s cybersecurity issues:
- “CISA: Critical infrastructure must prep for quantum computing threat” (Tenable)
- “President Biden Signs Quantum Cybersecurity Preparedness Act into Law” (Infosecurity Magazine)
- “Quantum apocalypse: Experts warn of ‘store now, decrypt later’ hacks” (Silicon Republic)
- Cloud Security Alliance’s Quantum-safe Working Group
- “Inside NIST's 4 Crypto Algorithms for a Post-Quantum World” (DarkReading)
VIDEO
Post-Quantum Cryptography: the Good, the Bad, and the Powerful (U.S. National Institute of Standards and Technology)
Quantum Computers Explained (Cleo Abram)
Cybersecurity in the Quantum Future (Center for Strategic & International Studies)
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Government
- Internet of Things
- Legislation
- NIST
- OT Security
- Risk-based Vulnerability Management
- Security Frameworks


