Cybersecurity Snapshot: For Strong Cloud Security, Focus on Configuration

Check out the NCSC’s advice about proper configuration in cloud security. Plus, a detailed guide about LockBit ransomware. Also, don’t miss OWASP’s revised list of top API security risks. Plus, CISA’s warning about remote network management tools. Et bien plus encore !
Dive into six things that are top of mind for the week ending June 16.
1 – NCSC: Configuration is key for cloud security
The U.K.’s National Cyber Security Centre (NCSC) has expanded its cloud security guidance with recommendations for using software-as-a-service (SaaS) apps and public cloud platforms securely. En conclusion : It’s all about proper configuration.
Here’s a sampling of the NCSC’s advice:
SaaS
- Understand the apps and their purpose, so you can balance usability and security in your configuration
- Manage user onboarding and offboarding via a continuous “joiners, movers and leavers” process to grant and remove access
- Adopt robust user authentication, including granular, unique user attributes and best practices like single sign-on (SSO) and multi-factor authentication (MFA)
- Minimize the number of administrative users, apply the principle of least privilege, and log and monitor privileged access
- Have plans for incident response and disaster recovery that are tested and well-defined
Cloud platforms – infrastructure-as-a-service (IaaS) and platform-as-a-service (PaaS)
- Authenticate user identities, using SSO, MFA, strong password requirements and authentication monitoring
- Apply granular access controls so that both user and service identities only access data and services they need
- Leverage automation to enforce security by using a wide variety of automation tools to detect, alert and block unauthorized changes
- Establish observability to view and analyze all your cloud resources, and monitor cloud-service changes and issues
- Protect your data at rest and in transit, and only store and process data in the cloud while necessary
To get all the details, check out the NCSC’s announcement “New cloud security guidance: it's all about the config,” along with a summary of the guidance, and specific, detailed sections about SaaS security and IaaS/PaaS platform security.
For more information about cloud security, check out these Tenable resources:
- “The Role of Open Source in Cloud Security: A Case Study with Terrascan by Tenable” (blog)
- “Five Core Principles for Hybrid Cloud Security” (blog)
- “5 Must-Haves for Hybrid Cloud Security” (on-demand webinar)
VIDEOS
Drift happens: Understanding malicious and non-malicious changes
Sécuriser K8s avec la gestion de la posture de sécurité de Kubernetes (KSPM)
2 – Comprehensive guide on LockBit ransomware released
It’s everything you always wanted to know about LockBit but were afraid to ask.
Cybersecurity agencies from seven countries published this week a joint advisory about LockBit, which they said ranked as the world’s most deployed ransomware variant last year and continues causing mayhem in 2023.
The LockBit operation uses a ransomware-as-a-service (RaaS) model, with affiliates recruited to carry out attacks using its tools and infrastructure. But because LockBit affiliates function independently, they employ a wide variety of tactics, techniques and procedures (TTPs).
“This variance in observed ransomware TTPs presents a notable challenge for organizations working to maintain network security and protect against a ransomware threat,” reads the 30-page document, titled “Understanding Ransomware Threat Actors: LockBit.”

In the U.S. alone, there have been around 1,700 LockBit ransomware attacks since 2020, resulting in around $91 million in paid ransoms.
Authored by cyber agencies from the U.S., Canada, Australia, U.K., France, Germany and New Zealand, the guide offers a deep dive into all things LockBit, including its evolution; tools used by attackers; TTPs; exploited vulnerabilities; recommended mitigations; and trends and statistics.
“Arming organizations with this knowledge will enable them to better understand, recognize and face this threat,” said Sami Khoury, Head of the Canadian Centre for Cyber Security, in a statement.
To get all the details, check out the announcement from the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the full guide, as well as coverage from The Record, Infosecurity Magazine, The Register and Computer Weekly.
3 – OWASP revamps its top 10 API security risks
OWASP just revised its list of the 10 most critical API security weaknesses and risks for the first time since 2019. So if you’re a developer, designer or architect involved in developing and maintaining APIs, check it out. The list describes each risk, ranks its exploitability and explains its impacts. It also offers recommendations for preventing each of the following risks:

- Broken object level authorization
- Broken authentication
- Broken object property level authorization
- Unrestricted resource consumption
- Broken function level authorization
- Unrestricted access to sensitive business flows
- Server side request forgery
- Mauvaise configuration de sécurité
- Improper inventory management
- Unsafe consumption of APIs
“By nature, APIs expose application logic and sensitive data such as personally identifiable information (PII), and because of this, APIs have increasingly become a target for attackers. Without secure APIs, rapid innovation would be impossible,” reads the project’s Foreword section.
To get all the details, go the OWASP API Security Project main page and check out the list.
For more information about API security:
- “What is API security?” (TechTarget)
- “API Security Is the New Black” (Dark Reading)
- “5 best practices to ensure the security of third-party APIs” (CSO)
- “Honda API flaws exposed customer data, dealer panels, internal docs” (BleepingComputer)
- “12 API security best practices to protect your business” (TechTarget)
VIDEO
Getting API security right (NDC Conferences)
4 – CISA zooms in on internet-accessible network management tools
Does your company use remote administration tools to manage internal networks via the public internet? You might want to check out what the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has to say about them.
CISA finds them so risky when they’re improperly configured that this week it issued an order instructing civilian federal agencies to either disconnect them from the internet or secure them via zero trust capabilities that enforce access control.
“Too often, threat actors are able to use network devices to gain unrestricted access to organizational networks, in turn leading to full-scale compromise,” CISA Director Jen Easterly said in a statement. After such a tool is detected, agencies will have 14 days to take corrective action.
An example of these tools, which CISA calls “internet-exposed management interfaces,” would be an internet-accessible, web-based console for managing a router in an agency’s internal network.
While the order, titled “Binding Operational Directive 23-02: Mitigating the Risk from Internet-Exposed Management Interfaces,” is aimed specifically at federal civilian agencies, its advice might be helpful for any organization that uses this type of tool.
Practice Banned by BOD 23-02: Networked Management Interfaces Accessible from the Internet
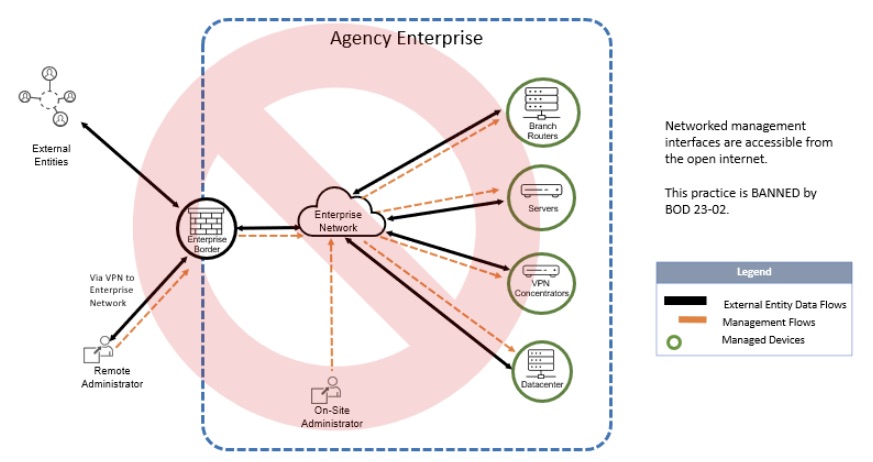
(Source : CISA)
To get all the details, check out:
- The announcement “CISA Directs Federal Agencies to Secure Internet-Exposed Management Interfaces”
- Binding Operational Directive 23-02
- Implementation guidance for the directive
- Coverage and commentary from The Record, FCW and FedScoop
5 – Accenture: Cybersecurity boosts business
Cybersecurity helps grow sales and reduce costs. That’s a key takeaway from Accenture’s “State of Cybersecurity Resilience 2023” report, released this week.
Specifically, organizations with closely aligned cybersecurity programs and business objectives are:
- 18% more likely to hit revenue growth targets and market share goals
- 26% more likely to shrink the cost of cybersecurity breaches and incidents
For the study, Accenture polled 3,000 respondents – 2,500 security executives and 500 business leaders – from companies with $1 billion-plus in revenue, located in 14 countries and from 15 industries.

It identified 30% as “cyber transformers” – those that make cybersecurity the foundation of their business’ digital transformation efforts, becoming highly resilient and reaping significant business benefits. These “cyber transformers” share four key characteristics:
- Excel at integrating cybersecurity and risk management
- Enhance cyber operations via cybersecurity-as-a-service
- Show more commitment to protect their ecosystem
- Rely heavily on transformation
Among the report’s recommendations for boosting digital transformation with cybersecurity are:
- Require cyber controls before the deployment of new business services and products
- Apply cybersecurity incrementally as digital transformation milestones are attained
- Appoint a representative to orchestrate cybersecurity across all transformation initiatives
To get all the details, read the report’s announcement, a summary and the full report.
For more information about the importance of cybersecurity to business:
- “The Devastating Business Impacts of a Cyber Breach” (Harvard Business Review)
- “Top 6 benefits of zero-trust security for businesses” (TechTarget)
- “6 Ways Cybersecurity Can Boost Revenue” (InformationWeek)
- “Study: Cybersecurity having greater impact on business growth” (Tenable)
- “Cybersecurity Drives Improvements in Business Goals” (Dark Reading)
6 – Most CISOs ain’t ready to be board directors
Are CISOs in publicly traded companies ready to become board members? Apparently not many.
The question is in the spotlight, as the U.S. Securities and Exchange Commission (SEC) mulls requiring publicly traded companies to disclose the cybersecurity expertise of their boards. If such a rule is approved, companies would be incentivized to add cyber experts to their boards. Their CISOs would be a logical option.
However, only 14% of CISOs in Russell 1000 companies – an index of the publicly-traded companies with the largest market capitalization – are strong candidates for a board position, while half of them could be “viable” candidates.
That’s according to the report “CISO as Board Directors - CISO Board Readiness Analysis” from IANS Research, Artico Search and The Cap Group, which also found that about 6% of Russell 1000 CISOs have experience as a board director.

So what makes a CISO a suitable board candidate? The study identifies several factors, including:
- Having broad experience in other non-tech functions, which helps them better understand the business holistically and strategically
- Holding an advanced degree in areas like tech, engineering, business or law
To get all the details, read the report’s announcement and download the report.
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Government


