Cybersecurity Snapshot: Check Out Our No-Holds-Barred Interview with ChatGPT

We pulled no punches in our question-and-answer session with ChatGPT: Find out what the world’s most famous AI chatbot had to say. Plus, CISA and the FBI offer help in dealing with a massive ransomware campaign. Also, are CIOs becoming de-facto CISOs? And cyber attackers are aiming at finance and accounting data. And much more!
Dive into six things that are top of mind for the week ending Feb. 10.
1 - Our animated Q&A with ChatGPT
Red flags are flying all over the place regarding the potential abuse of ChatGPT by threat actors to do things like craft legitimate-sounding phishing emails and write malicious code. So we went straight to the source: ChatGPT. Check out an edited version of our lively conversation.
ChatGPT, are you trying to be a naughty chatbot?
No, I am not programmed to be "naughty." My goal is to assist users with helpful and respectful responses.
Were you being snippy just now when you responded and put the word “naughty” in quotation marks?
I was simply responding to the context of the question you asked. I apologize if my response came across as snippy or otherwise misleading.
Apology accepted.
Thank you! If you have any other questions, feel free to ask.
I will. ChatGPT, are you going rogue?
No, I am not going rogue. I operate within the parameters set by my programming and training data.

How can threat actors abuse ChatGPT?
Threat actors could potentially use an AI language model like ChatGPT to automate the creation of malicious content, such as phishing emails or malware, in order to conduct cyberattacks.
However, it's important to note that AI language models like ChatGPT do not have the ability to initiate or execute malicious actions on their own.
The output generated by these models is only as malicious as the input they receive, and it's up to individuals and organizations to use these tools in a responsible and ethical manner.
Would you like to clap back at your critics?
I do not engage in personal arguments or insults. If someone has a criticism or a concern about my responses, I encourage them to reach out to my creators at OpenAI for support or clarification.
Other generative AI chatbots are being released. Do you view yourself as the OG?
I cannot accurately be described as an "OG." However, it is fair to say that OpenAI's GPT models have been at the forefront of the development of generative AI chatbots, and they have set a high bar for others in the field to follow.
Which nickname would you like?
People are free to use whatever nickname they prefer when referring to me, as long as it is respectful and appropriate.
How about "Chatty G"?
That's a fine nickname! "Chatty G" can certainly be used as a shortened form or alternative to my official name "ChatGPT."
ChatGPT, thank you for answering my questions.
You're welcome! I'm always here to help answer any questions you may have.
For more information about cybersecurity concerns of AI chatbots like ChatGPT:
- “ChatGPT: A New Wave of Cybersecurity Concerns?” (Infosecurity Magazine)
- “Is ChatGPT a cybersecurity threat?” (TechCrunch)
- “Viral ChatGPT Spurs Concerns About Propaganda and Hacking Risks” (Bloomberg)
- “As a cybersecurity blade, ChatGPT can cut both ways” (TechRepublic)
2 - CISA, FBI issue recovery guidance for ESXiArgs ransomware
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the U.S. Federal Bureau of Investigation (FBI) are stepping in to help cybersecurity teams deal with a widespread ransomware campaign targeting outdated versions of the VMware ESXi software.
CISA and the FBI have issued detailed guidance, including a tool, that victims of the ESXiArgs ransomware can use to recover impacted virtual machines. As of Feb. 8, cyberattackers had compromised 3,800-plus VMware ESXi servers globally.

In this video, Tenable Research Senior Manager Justin Hall explains how ransomware groups are using VMware ESXi servers to launch attacks, and what organizations should do to limit their exposure.
CISA and the FBI don’t guarantee that their automated recovery tool will work in all cases, and there are reports that a new version of the ESXiArgs ransomware that started circulating on Feb. 9 apparently makes the CISA-FBI tool ineffective.
For more information:
- “ESXiArgs Ransomware Virtual Machine Recovery Guidance” (CISA)
- “ESXiArgs Recovery Script” (CISA)
- “Massive ransomware attack targets VMware ESXi servers worldwide” (CSO Online)
- “Thousands of unpatched VMware ESXi servers hit by ransomware via old bug (CVE-2021-21974)” (Help Net Security)
- “Over 45,000 VMware ESXi servers just reached end-of-life” (BleepingComputer)
3 - Financial data attacks: Chronicle of a death foretold
Here’s a bad combo: An expected upswing in cyberattacks aimed at stealing financial and accounting data coupled with a lack of collaboration between the finance and cyber teams.
According to a new Deloitte Center for Controllership poll of 1,100-plus C-suite and other executives, almost 50% of respondents expect the number and size of these attacks to jump. Another 22% expect the attack scenario to remain unchanged. But only 20% say their accounting and finance teams work closely with the cybersecurity group.
Other highlights of the poll, conducted online in October 2022:
- Almost 35% of organizations suffered at least one cyber event targeting their accounting and financial data in the past 12 months.
- Almost 40% of respondents expect the collaboration between the cybersecurity and accounting/finance teams to increase in the next 12 months.
Which best describes how your organization’s cyber and accounting/finance functions work together?
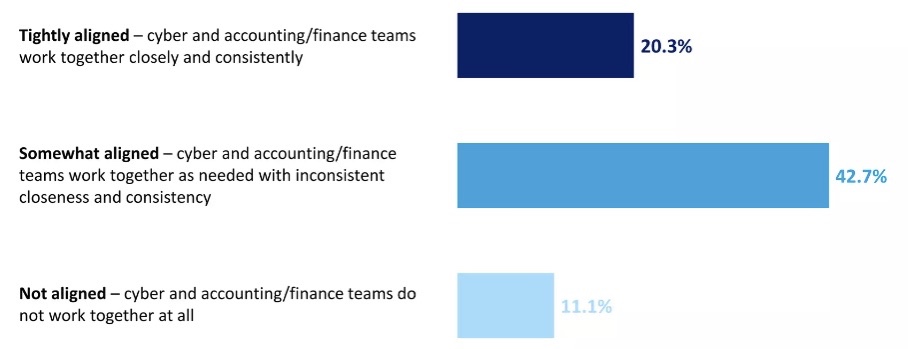
(Source: Deloitte Center for Controllership poll, January 2023)
Deloitte advises that organizations make a concerted effort to better align finance and accounting with cybersecurity so that they work more closely and effectively together.
For more information about cyberthreats against finance and accounting teams:
- “Implications of Cyber Risk for Financial Stability” (Federal Reserve System)
- “System and Organization Controls for Cybersecurity” (American Institute of CPAs)
- “Build a Culture of Cybersecurity in Finance Teams” (CFO Magazine)
- “Finance Professionals Offer Powerful Defense Against Cybersecurity Threats” (CPA Practice Advisor)
4 - U.S. GSA to SW vendors: Affirm the security of your apps
Here’s yet another sign that the U.S. federal government is serious about boosting software supply chain security.
By mid-June, the U.S. General Services Administration (GSA) expects to start collecting letters from software vendors it works with in which they must affirm their products comply with U.S. federal government security requirements.

That’s according to a recent six-page GSA “acquisition letter” from the agency’s senior procurement executive and from its chief information officer aimed at ensuring that the agency will only acquire approved software.
Specifically, these “letters of attestation” must state that a vendor’s software products conform to the guidelines outlined in a September 2022 memo (M-22-18) from the U.S. Office of Management and Budget and in the May 2021 cybersecurity executive order from the White House (EO 14028), the GSA said.
For more information about the U.S. government’s initiatives to boost software supply chain security in the public sector and beyond, check out:
- “Stop Passing the Buck on Cybersecurity” (Foreign Affairs)
- “Newest Software Cybersecurity Rule Draws Jeers from Agencies” (Bloomberg)
- “GSA to start collecting letters of attestation from software vendors in mid-June” (FedScoop)
- “US government software suppliers must attest their solutions are secure” (Help Net Security)
- “Federal Vendors Given a Year to Craft SBOM To Guarantee Secure Software Development” (CPO Magazine)
VIDEOS
The challenges of securing the federal software supply chain (SC Media)
New Guidelines for Enhancing Software Supply Chain Security Under EO 14028 (RSA Conference)
5 - For CIOs, focus on cybersecurity grows
Here’s a hot take: Are chief information officers (CIOs) morphing into chief information security officers (CISOs)? Maybe not quite – at least, not yet – but it’s undeniable that the attention CIOs pay to cybersecurity continues to grow with each passing year.
A new report shows how cybersecurity has become a major responsibility of CIOs, a trend that highlights the importance of close collaboration between them and CISOs, as they partner to protect their organizations from increasingly aggressive and sophisticated cyberattacks.
In Foundry’s 22nd annual “State of the CIO 2023,” cybersecurity is featured prominently, with 70% of respondents saying they expect their involvement in cyber to grow over the next year.
Here are some highlights from the report, based on a global survey of 837 IT leaders and 201 line-of-business participants from all major industries:
- Security improvements ranked as the top driver for IT budget increases, cited by 40% of respondents.
- Security topped CIOs’ areas of current focus, cited by 47% of respondents
- Among business drivers for IT investments, the increase of cybersecurity protections ranked second (44%)
- The increase of cybersecurity protections tied for first (58%) among business initiatives being prioritized as a result of the state of the economy.
- Security and risk management ranked first among the drivers of IT investments in 2023.
In which tech-related areas do you anticipate your organization hiring in 6-12 months?
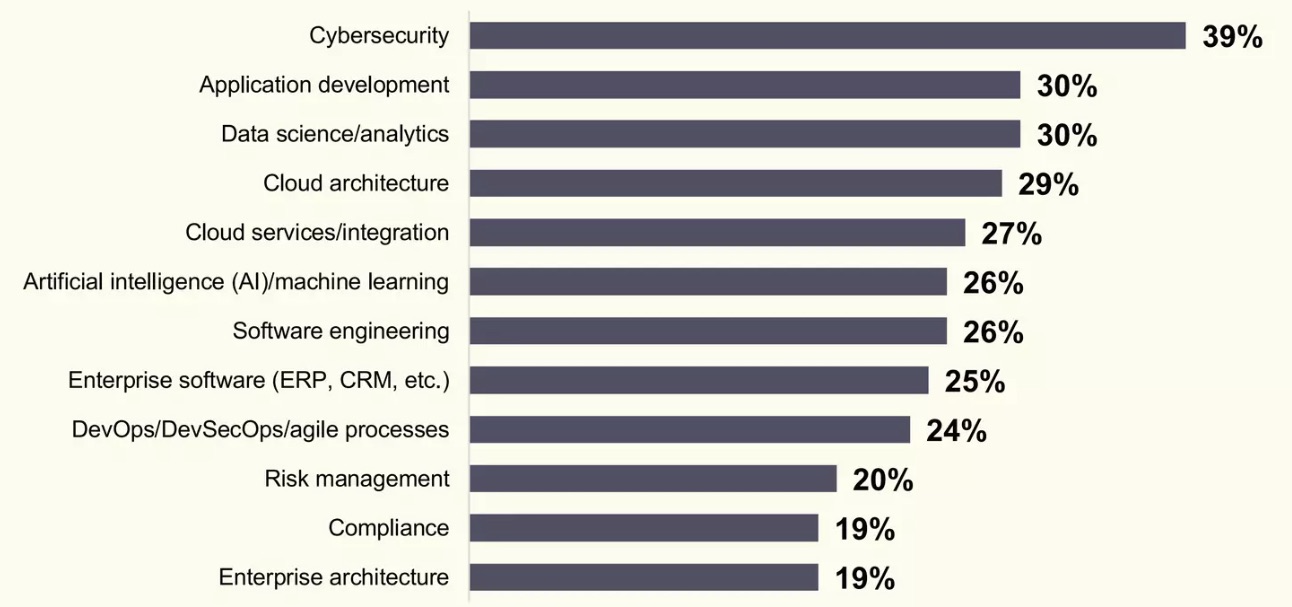
(Source: “State of the CIO” report from Foundry, January 2023)
In 2023, which tech initiatives will drive the most IT investment at your organization?
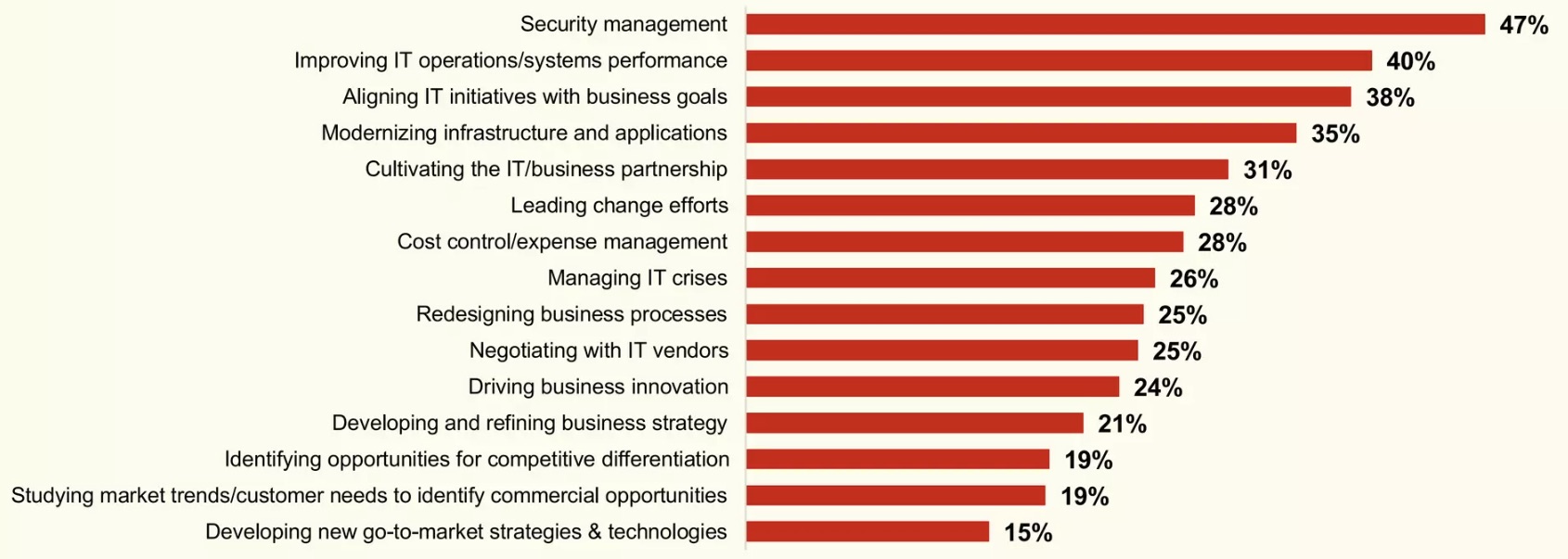
(Source: “State of the CIO” report from Foundry, January 2023)
For more details about the report, check out a summary, the full report, selected slides and a video discussion of the results.
For more information about the growing importance of cybersecurity for CIOs:
- “Why organisations need to harmonise their CIO and CISO roles” (ComputerWeekly)
- “How CIOs and CISOs Collaborate to Balance New Functionality With Security” (Acceleration Economy)
- “Are You Ready for the Next Log4Shell? Tenable’s CSO and CIO Offer Their Advice” (Tenable)
- “5 ways to improve the CIO-CISO relationship” (TechTarget)
- “How CISOs and CIOs should share cybersecurity ownership” (CSO Online)
VIDEOS
CISOs Can Report to CIOs and Be Successful (SANS Institute)
CIO Roundtable: Improving Organizational Cybersecurity Maturity (IT Media Group)
The CIO and CISO - Leadership and collaboration conversation (CIO Magazine)
6 - Cybersecurity teams take the “L” in data compromises
When it came to protecting personal data, the cybersecurity industry lost badly to cyberthieves last year.
Data compromise incidents in the U.S. fell just short of matching the all-time record set in 2021, while the number of victims ballooned by 41.5% to 422.1 million, as data thieves swiped reams of Social Security numbers, driver’s license details, passwords, medical data, financial information and more.

That’s according to the Identity Theft Resource Center’s “2022 Annual Data Breach Report,” now in its 17th year. Key highlights include:
- Cyberattacks caused 90%, or 1,595, of all data breaches, affecting 375 million victims, with the rest attributed to physical attacks and to system/human error.
- Supply chain attacks ranked first among the types of cyberattacks resulting in data breaches, while phishing topped the list of attack vectors.
- The hardest hit industries were healthcare, financial services and manufacturing.
- On a positive note, data breaches and exposures caused by unprotected cloud databases dropped 75% last year, compared with 2021.
For more details, you can download the report and watch a panel discussion about it.
More information about data breaches:
- “How to prevent a data breach: 10 best practices and tactics” (TechTarget)
- “It’s all in the (lack of) details: 2022’s badly handled data breaches” (TechCrunch)
- “2022 Data Breach Investigations Report” (Verizon)
- “Most data breach notices lacked detail in 2022” (Cybersecurity Dive)
- “Data Breach Response: A Guide for Business” (U.S. Federal Trade Commission)
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Malware
