Comprehensive Vulnerability Management for a Changing IT Landscape
A comprehensive vulnerability management program is the foundation for effective security. Yet, many organizations find it challenging to run an effective program where vulnerabilities are quickly identified and remediated. And for many organizations, not fixing vulnerabilities has consequences. In their Market Overview: Vulnerability Management report published in April 2015, Forrester Research noted that 53% of external attacks are carried out by hackers exploiting software vulnerabilities.
Many organizations find it challenging to run an effective program where vulnerabilities are quickly identified and remediated
There are many reasons why vulnerability management is challenging. The top concerns we hear frequently from customers are:
- The volume of reported vulnerabilities is overwhelming. In 2015, the National Vulnerability Database shows an average of 25 new vulnerabilities reported every day.
- There are limited available resources to fix vulnerabilities and tackle the challenge of prioritizing remediation. In the Technology Adoption Profile: Vulnerability Management Trends in APAC, an April 2016 commissioned study conducted by Forrester Consulting on behalf of Tenable, 34% of respondents said it was difficult to prioritize which vulnerabilities are most important.
- The IT landscape is changing, bringing with it new vulnerabilities. As more organizations embrace cloud services and applications as well as BYOD/mobile, these technologies can potentially introduce an entirely new set of vulnerabilities into the IT landscape.
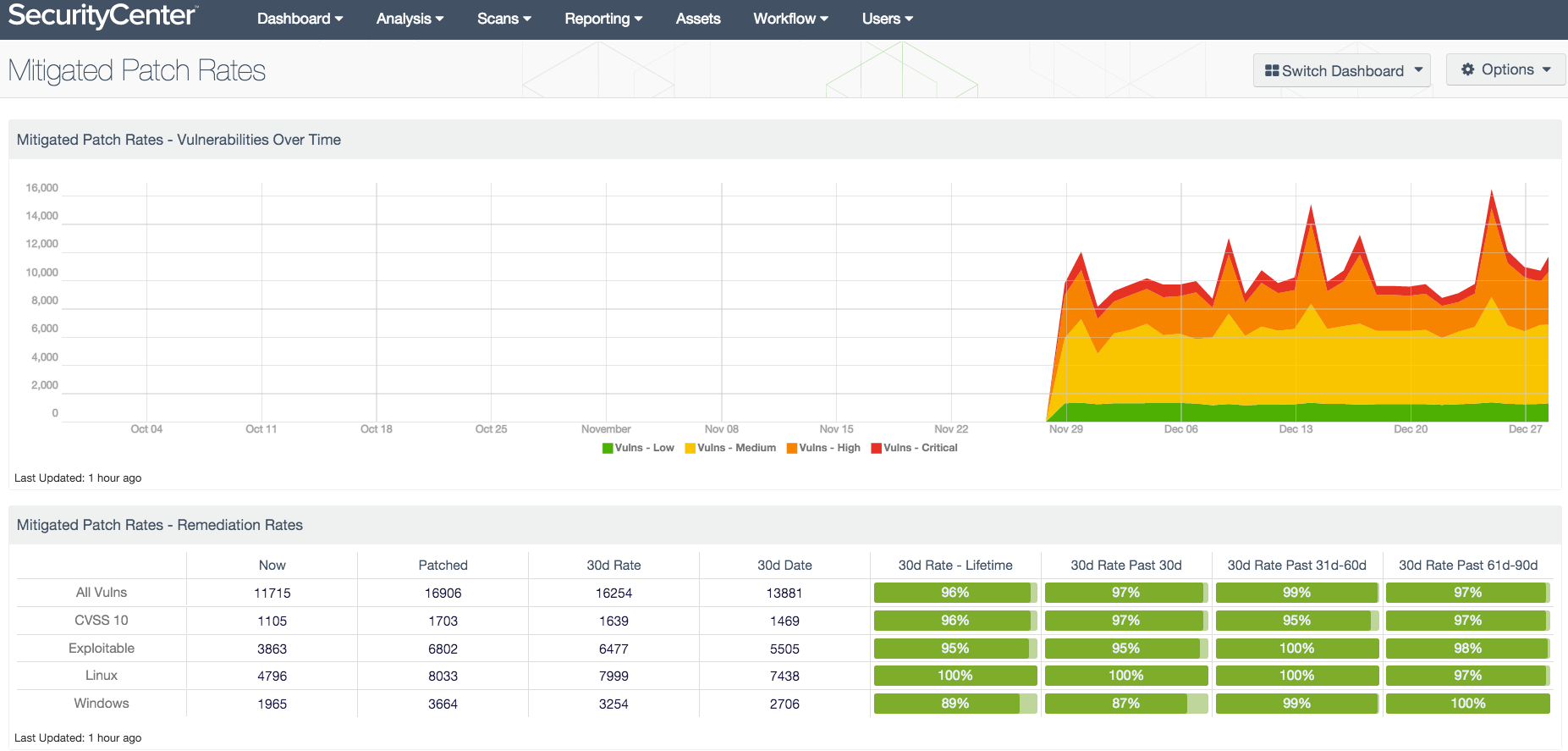
Adding to the challenge is the desire to track whether the vulnerability management program is improving or not. Again, the sheer volume of data makes tracking impossible for many.
The need for a reliable, proven vulnerability management solution
Tenable has a deep and rich history in vulnerability management. As the creators of Nessus®, we’ve seen our flagship product develop over the years from an open source tool with a few Linux checks to a full function solution that today has more than 76,000 checks. These cover nearly 30% more vulnerabilities across 32% more technologies than competitive solutions.
Tenable has a deep and rich history in vulnerability management
Vulnerability management is more than just scanning though, so at Tenable we’ve introduced complementary technologies to help organizations run their comprehensive vulnerability management programs.
Agents - Last year, we introduced agents for Nessus. Agents help organizations extend their vulnerability management programs to those hard-to-scan assets that hide out in the network. These might be transient devices like laptops that aren’t typically connected to the network when an active scan is taking place. Or they might be assets that you’d like to run authenticated scans on, but which are also assets where it’s difficult to get access to their credentials on an ongoing basis. Agents are also helpful for organizations that want to run scans more frequently without burdening network resources. Since agents are distributed and use local system resources, you can have many agent scans running on many assets at any time with minimal impact to your network.
Passive scanning - Tenable’s passive listening and event monitoring capabilities also detect and monitor services and applications in use and their vulnerabilities – even in cloud and virtualized environments.
These capabilities have the added benefit of being able to provide data continuously so your organization has updated information about vulnerabilities between active scans.
Results you can use
Tenable technologies that help you collect vulnerability data are just one part of the equation. It’s equally important to us to help customers interpret all that data. To accomplish this, our solutions offer meaningful reports and dashboards that put results into context.
The Tenable research team helps by providing daily content updates, new dashboards, and pre-built reports that provide the critical context for your vulnerability management program. Reports showing information such as vulnerabilities over 30 days old or the percentage of hosts compliant with configuration audits, enable you to make better business decisions and prioritize your efforts to optimize your security posture.
Looking ahead
We see comprehensive vulnerability management remaining a foundation for effective security for years to come. We do see the landscape changing though, as organizations move IT assets to the cloud and embrace new technologies like cloud and mobile. As a result, we’ll continue to invest in our vulnerability management technologies to give customers effective ways to manage vulnerabilities in whatever IT environment they’re operating.
Comprehensive vulnerability management will remain a foundation for effective security for years to come
If you want to keep up with the latest and greatest vulnerability management updates from Tenable, visit the Vulnerability Management section of our website where we post links to our latest white papers, webcasts and other materials that you might find interesting.
- Vulnerability Management