7 Regulatory and Compliance Frameworks with Broad Cloud Security Implications

Security teams responsible for enforcing regulatory and compliance mandates in a scalable and consistent way are often challenged to translate general legislative guidelines and controls into specific policies, tools and processes.
Cyberattacks not only pose financial or brand risk to an organization. They’re also a matter of national security that can disrupt critical supply chains and — in the case of critical infrastructure — even result in loss of life.
Geopolitical factors, such as the war in Ukraine, have emboldened state-sponsored attacks in the past year. According to the Threat Landscape 2022 report from the European Union Agency for Cybersecurity (ENISA), state-sponsored threat actors have targeted 128 governmental organizations in 42 countries that support Ukraine. Targets include the U.S., Poland, Denmark, Norway, Finland, Sweden, Turkey and other NATO countries.
Governments and industry groups around the world have long been working on ramping up the legislative and regulatory environments with an eye toward curbing attacks. Recent events, such as the 2020 SolarWinds software supply chain attack that impacted over 18,000 public- and private-sector organizations as well as those targeting critical infrastructure operators like Colonial Pipeline have spurred a rash of new regulations.
While all aspects of the attack surface are at risk, cloud infrastructure and applications have emerged as a particular target area. In a LinkedIn blog post, Thierry Breton, European Union Commissioner for Internal Market, said “attacks on cloud infrastructure have increased fivefold in one year.”
“Attacks on cloud infrastructure have increased fivefold in one year.”
—Thierry Breton, European Union Commissioner for Internal Market
In this blog, we explore:
- Mediating risk through increased legislation
- Regulations and penalties with cloud security implications
- How risk frameworks, controls and benchmarks support compliance
- Automating cloud security controls and compliance: Comment Tenable peut vous aider
Mediating risk through increased legislation
In response to increased cyberthreats, governments are enacting mandates and legislation. For example, in the U.S., Executive Order 14028 focuses on improving the security of the software supply chain. In the European Union, the Cyber Resilience Act — published by the European Commission in September 2022 — looks to ensure hardware and software products are placed on the market with fewer vulnerabilities. Such measures not only place new requirements on government agencies, they extend broadly to the organizations these agencies do business with, including cloud service providers, software development organizations, software as a service (SaaS) providers, hardware manufacturers and virtually any organization creating digital products and services.
The legislative and regulatory changes in the U.S. are not limited to the federal government — they’re also cascading down to state and local governments. Likewise, in addition to the E.U. regulations, nations within the union may also have their own requirements. In the United States, for example, 36 states have enacted new cybersecurity laws in the past two years, with many more in the works as the public sector looks to mitigate risk of cyberthreats.
Adding to government regulations, industries have also begun to define their own mandates in an effort to improve security posture and minimize risk to consumers and investors. One example of this is PCI DSS in the payment card industry.
For the security teams that must implement these mandates, the challenge is in translating what are often general legislative guidelines and controls into specific policies, tools and processes. Further, security teams are responsible for enforcing those policies in a scalable and consistent way across the enterprise. For security teams working in multinational enterprises, these challenges are compounded exponentially.
The regulatory environment impacts all aspects of cybersecurity, including traditional IT infrastructure and operational technology. In order to understand how the regulatory environment affects cloud security, you first need an understanding of which regulations apply to your particular business. The table below highlights several regulations with broad sweeping cloud security implications — and the risks that come with non-compliance. Regulations and penalties with with cloud security implications
|
Regulation |
Source |
Requirement |
Penalty |
Example |
|
General Data Protection Regulation (GDPR) |
Approved by the European Union in 2016, GDPR looks to enforce data protection guidelines for the collection and processing of personal information for anyone living in the European Union. |
Applies to any entity with a website that attracts European visitor traffic, whether that entity is actively marketing to EU residents or not. Data breaches must be reported within 72 hours. |
Organizations can be fined up to €20 million or 4% of a firm's global turnover (whichever is greater). |
In 2020, British Airways was required to pay $26 million because of inadequate security controls which led to 429,000 client records being compromised. |
|
New York Cyber Security Regulation, Part 500 (23 NY CRR 500) |
In 2017, The New York State Department of Financial Services began enforcing Cyber Security Regulation section 500 (23 NYCRR 500), which aims to protect consumers by defining minimum cybersecurity standards for regulated institutions. |
The regulation applies to nearly 3,000 financial institutions and requires they implement a cybersecurity program that aligns with the NIST Cybersecurity Framework. |
A cybersecurity event must be reported within 72 hours. Non-compliance can result in financial and other penalties ranging from a minimum of $500/day per incident of non-compliance to $2,500 depending on the industry. Penalties can increase from there based on intentional violation and duration. |
In 2022, Carnival Companies was fined $5 million, had to pay $1.25 million in a multi-state settlement, and lost their license to sell insurance as a result of four separate breaches. The breaches occurred between 2019-2022, and included ransomware and phishing attacks which exposed nonpublic personal information (NPI) of consumers and employees. |
|
Health Insurance Portability and Accountability Act (HIPAA) |
Passed by the U.S. Congress, the intent of the HIPAA Privacy Rule is to limit the use and disclosure of electronically protected healthcare information (ePHI), such as medical records, without explicit authorization by individuals. |
The regulation applies to healthcare providers, health plans and healthcare clearinghouses that conduct healthcare transactions electronically. |
Penalties for breaches can be both civil and criminal. Civil can range up to $63,000 per violation, with a $1.9 million yearly cap. Criminal can be up to $100,000 and 10 years in prison if the intent was to sell the information for financial gain. |
In 2021, Excellus Health Plan was fined $5.1 million for failing to put the necessary security controls in place, which allowed hackers to access the personal records of 9.3 million people for over a year. |
|
Payment Card Industry Data Security Standard (PCI DSS) |
Released in December 2004, PCI DSS was an industry-led initiative created to better manage cardholder data and reduce credit card fraud. It was defined by the PCI Security Standards Council (PCI SSC), which includes American Express, Visa, MasterCard, Discover and others. |
While not a federal regulation, the industry standard is mandatory for all entities that store, process, and/or transmit cardholder data. The standard includes specific cloud computing guidelines which provide guidance on the use of cloud technologies and for maintaining controls in cloud environments. |
Non-compliant organizations that experience a data breach can face fines up to $500,000, loss of their merchant account and damages. |
In 2017, Target was required to pay $18.5 million in a settlement with 47 states, for which it spent $202 million in legal fees. The breach which resulted in the loss of 40 million credit card records, is one of the most visible PCI DSS breaches. |
Source : Tenable, April 2023
How risk frameworks, controls and benchmarks can help
Fortunately, a number of federal and industry sponsored organizations have been established to help enterprise and government organizations improve their cybersecurity posture. These organizations collect best practices and define risk frameworks, as well as supporting cybersecurity controls and benchmarks.
Frameworks provide a set of processes, best practices and specifications to help organizations assess and manage risk. They lay the foundation for effective cybersecurity programs.
Controls identify ‘what should happen’ in order to mitigate a specific category of risk. Inventory of software assets, data protection, and secure configuration are examples of control categories. Each control category has a set of safeguards outlining what steps should be taken.
Benchmarks take the concept of controls to the next level, providing prescriptive guidance on how to implement and configure specific technology, such as cloud instances, applications and identities, in a secure way.
While some standards may be developed by specific government agencies, most have broad applicability regardless of country or body of origin, and many have direct alignment or overlap of controls. Below we highlight five worth noting.
National Institute of Standards and Technology Cybersecurity Framework
Part of the U.S. Department of Commerce, the National Institute of Standards and Technology (NIST) has developed numerous cybersecurity standards and best practices, including the NIST Cybersecurity Framework, a 40-page document providing high level guidance on how to prioritize, manage and reduce cybersecurity risk. The framework references a number of detailed documents for prescriptive controls. One of the most comprehensive of these is NIST Special Publication 800-53 Revision 5. The 460-page publication provides deep controls for cloud-based systems as well as other computing platforms, including general purpose computing systems, cyber-physical systems, mobile devices, internet of things (IoT) devices and others. NIST also publishes cybersecurity resource guides, such as Implementing the Health Insurance Portability and Accountability Act (HIPAA) Security Rule, to help organizations comply with specific regulations.
benchmarks CIS
The Center for Internet Security (CIS) is a nonprofit organization that develops crowdsourced, globally recognized best practices for securing IT systems and data. Similar to the NIST Cybersecurity Framework, CIS Critical Security Controls (CIS Controls) are a prioritized set of safeguards designed to mitigate cyberattacks. The Controls have been mapped to different regulatory and industry mandates, such as NYDFS 500. Additionally, CIS Benchmarks offer specific configuration guidelines for over 25 different vendor product families, such as Amazon Web Services (AWS), Microsoft Azure Cloud and Google Cloud Platform (GCP). Benchmarks are highly valuable because they provide prescriptive steps that must be taken in order to achieve the recommended configuration for a given vendor offering.
International Organization of Standards 27001 (IS027001)
Similar to CIS, the International Organization for Standards (ISO) is an independent, international organization that develops consensus based best practices and standards. One of the most well recognized is ISO 27001, a broadly recognized standard for information security management systems (ISMS). While not directly provided by ISO, organizations can obtain third-party certification of compliance with ISO 27001. While there is much overlap between standards like ISO 27001 and NIST Control Frameworks, there are differences. Generally speaking, NIST offers more granular controls, but on its own does not address the full spectrum of requirements needed for ISO 27001 certification. In that respect, these two frameworks are complimentary.
Automating cloud security controls and compliance: Comment Tenable peut vous aider
The regulations, controls and benchmarks covered here are just a fraction of the many that enterprise and government organizations must contend with. This makes scaling expertise challenging.
For over two decades, Tenable Research has brought to bear its expertise in regulations and standards to help organizations meet their unique security requirements. This same expertise is embedded in many Tenable solutions, in the form of pre-defined audits, policies and compliance reporting. For example, Tenable One for cloud security helps organizations harden their cloud security posture across multicloud environments by providing out-of-the-box policies which map directly to popular controls, benchmarks and regulations, such as NIST 800-53, CIS Benchmark for AWS, and GDPR, respectively.
This greatly reduces the need for specialized knowledge for every variety of standard or regulation. Security staff can apply policies for a given standard or regulation by selecting from a drop down menu and scanning for non-compliant configurations. They can also establish proactive guardrails to prevent deployment of non-compliant configurations. Below are some examples of the types of compliance reporting capabilities available in Tenable One for cloud security.
Compliance report: CIS 1.2 for AWS
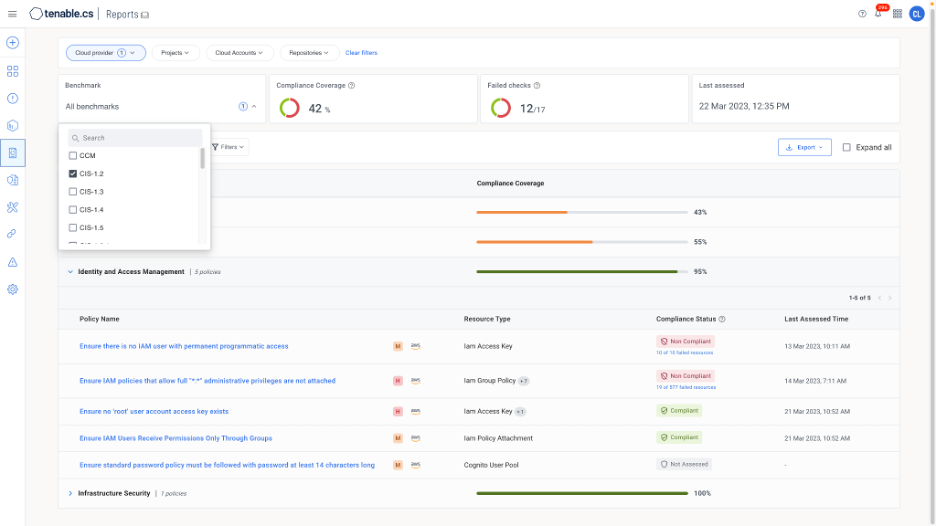
Source : Tenable, April 2023
Using a menu-based approach, organizations can select and run compliance reports for a given standard or regulation and share those reports with asset owners for remediation, as well as governance risk and compliance (GRC) teams and external auditors to meet ongoing compliance requirements.
Compliance report: RGPD
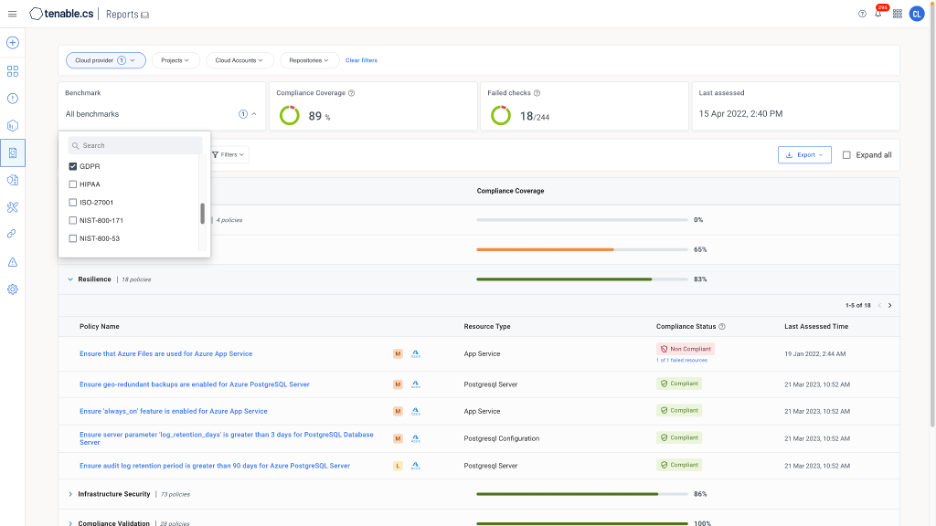
Source : Tenable, April 2023
Because Tenable One for cloud security supports hybrid environments in addition to multicloud, organizations can run policy audits and report compliance for on-premises environments — including IT and private clouds — providing an end-to-end view of compliance.
To learn more about how Tenable can help, check out episode three of the Tenable Cloud Security Coffee Break Series, The Challenges of Multicloud Compliance, where you’ll hear from Phillip Hayes, Tenable’s Director of Information Security, on how we address multicloud compliance for our own SaaS-based solutions and see a live demonstration of policies and compliance reporting in action.
En savoir plus
- Visit the Tenable Solution Page on Cloud Security Posture Management: tenable.com/cspm
- View the Solution Infographic: Unlock scalable cloud security for today's hybrid, multicloud world
- Cloud
- Exposure Management
- Government


