5 Ways to Protect Scanning Credentials for Windows Hosts

This is the second installment in our three-part series exploring how to use Tenable products to protect credentials used for network assessments. Here, we provide specific guidance for Microsoft Windows systems.
In my last post, I covered general best practices for protecting credentials when performing network assessments. When it comes to protecting credentials in a Microsoft Windows Active Directory environment, though, we have specific guidance.
Please note that enabling some of these controls may affect other parts of your network and systems. Before you implement any of these changes, you should test all settings thoroughly to determine if they are appropriate for your environment. Not all organizations will be able to implement all these settings. When configuring service account(s) for use in credentialed scanning, below are some key considerations unique to Windows hosts.
5 tips for credentialed scanning of Windows hosts
- Disable interactive log on.
Usually, accounts used for remote administrative authentication, like Nessus performs, don’t need to behave like a standard user account. To this end, enabling functionality that prevents unnecessary access like “Deny log on locally ” or “Deny log on through Remote Desktop Services” is a good idea. - Restrict delegated access.
Like interactive logon, Microsoft allows account privileges to be delegated under certain circumstances to enable specific functionality. This is not necessary for vulnerability scanning and should be disabled.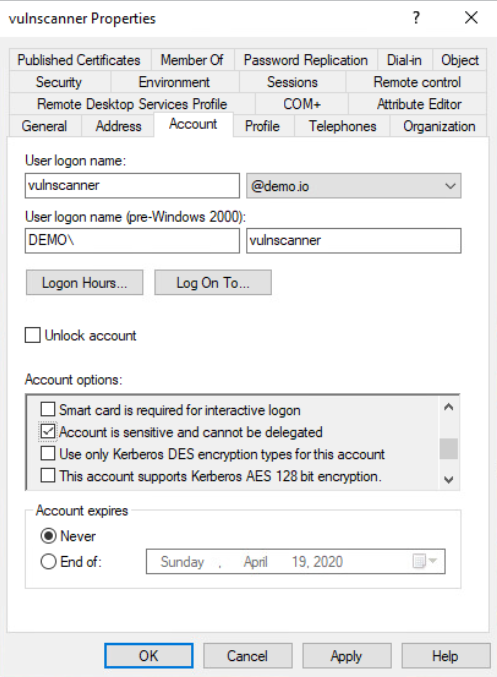
- Add the account to the “Protected Users” group.
If your Active Directory (AD) domain supports it, the “Protected Users” group adds additional security to how credentials are treated when authenticating to a host. The controls provided to this group are especially important if you can’t take advantage of all the other suggestions listed here. If your domain doesn’t support this functionality yet, try to implement the controls it provides individually where possible. - Secure SMB protocols.
It seems every few years, there’s a new critical vulnerability in the SMB protocol or the network services that live behind it. While keeping up-to-date on patches is critical, you can make several proactive configuration changes to further secure this service: - Prioritize or force Kerberos authentication.
Kerberos is the authentication protocol of choice for modern Windows systems. It has several benefits over NTLM, including preventing relay attacks, and is relatively easy to implement. By default, Nessus will disable the use of insecure protocols like NTLMv1 and LM.
Things to avoid:
- Do not use Domain Admin accounts (and other “High” privileged accounts).
Accounts in the “Domain Admin” group are extremely powerful and should be tightly controlled and restricted. Nessus does not require Domain Admin level privilege (or any domain-wide privilege) for remote network scanning, it only requires administrative access to the local machine being assessed.
- Do not use domains as security boundaries.
In AD, different domains that are part of one forest are not segmented. A compromise in one almost always means the entire forest is compromised. Segregating your privileged accounts and systems into another forest is essential. If using domain credentials to authenticate, especially if using higher-privileged accounts, ensure they’re part of a separate forest.
- Do not reuse accounts between scanning and users or other IT operations.
I noted this tip in our general best practices, but it deserves repeating. Accounts should be single-use.
In the next installment of this three-part series, I’ll discuss ‘nix credentialed assessments and options for securing that process.
Note: There are alternatives to credentialed network scanning, such as agents and passive assessments.
Learn More
Read the online documentation:
Other blog posts in this series:
- Overview: How to Protect Scanning Credentials
- 5 Ways to Protect Scanning Credentials for Linux, macOS and Unix Hosts
Explore related webinars:
- Automate Your Credentialed Vulnerability Assessments
- Overcoming the Challenges of Credentialed Scanning
Watch how-to videos:
- Nessus
- SecurityCenter
- Tenable Vulnerability Management
- Vulnerability Management
- Vulnerability Scanning