by Steve Tilson
October 17, 2017
As organizations continue to evolve, wireless technologies are now being utilized as much as the hardwired infrastructures. With this high utilization, Wi-Fi security is more important than ever. The KRACK (Key Reinstallation Attack) vulnerability affects all modern, protected Wi-Fi networks. This weakness in WPA2 can allow attackers to steal sensitive information such as passwords and credit card numbers, and even inject and manipulate data.
SecurityCenter CV utilizes both active and passive Nessus plugins to detect a wealth of Wi-Fi infrastructure vulnerability data and compliance information. Tenable quickly developed new plugins targeting the KRACK weakness. Information provided by SecurityCenter CV can assist security teams in assessing their devices and monitoring when they are secured by vendor-released updates.
Further key components in this dashboard assist security analysts in assessing their wireless infrastructure and finding devices that are communicating wirelessly. Components can assist security teams in obtaining an inventory of wireless access points and devices, and detecting wireless vulnerabilities. This information will enable organizations to better understand, manage, and ultimately reduce their cyber risk in the wireless arena.
This dashboard is available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Threat Detection & Vulnerability Assessments. The dashboard requirements are:
- SecurityCenter 5.4.0
- Nessus 6.11.1
- Nessus Network Monitor 5.3.0
Tenable SecurityCenter Continuous View® (SecurityCenter CV™) is the market-defining continuous network monitoring solution, which assists organizations in tracking vulnerabilities within the enterprise. SecurityCenter CV™ is continuously updated with information about advanced threats, zero-day vulnerabilities, and new regulatory compliance data. Active scanning periodically examines systems to determine vulnerabilities and compliance concerns. Agent scanning enables scanning and detection of vulnerabilities on transient and isolated devices. Passive listening provides real-time discovery of vulnerabilities in operating systems, protocols, network services, wireless devices, web applications, and critical infrastructure. SecurityCenter CV provides an organization with the most comprehensive view of the network and the intelligence needed to effectively address vulnerabilities such as KRACK.
The following components are included:
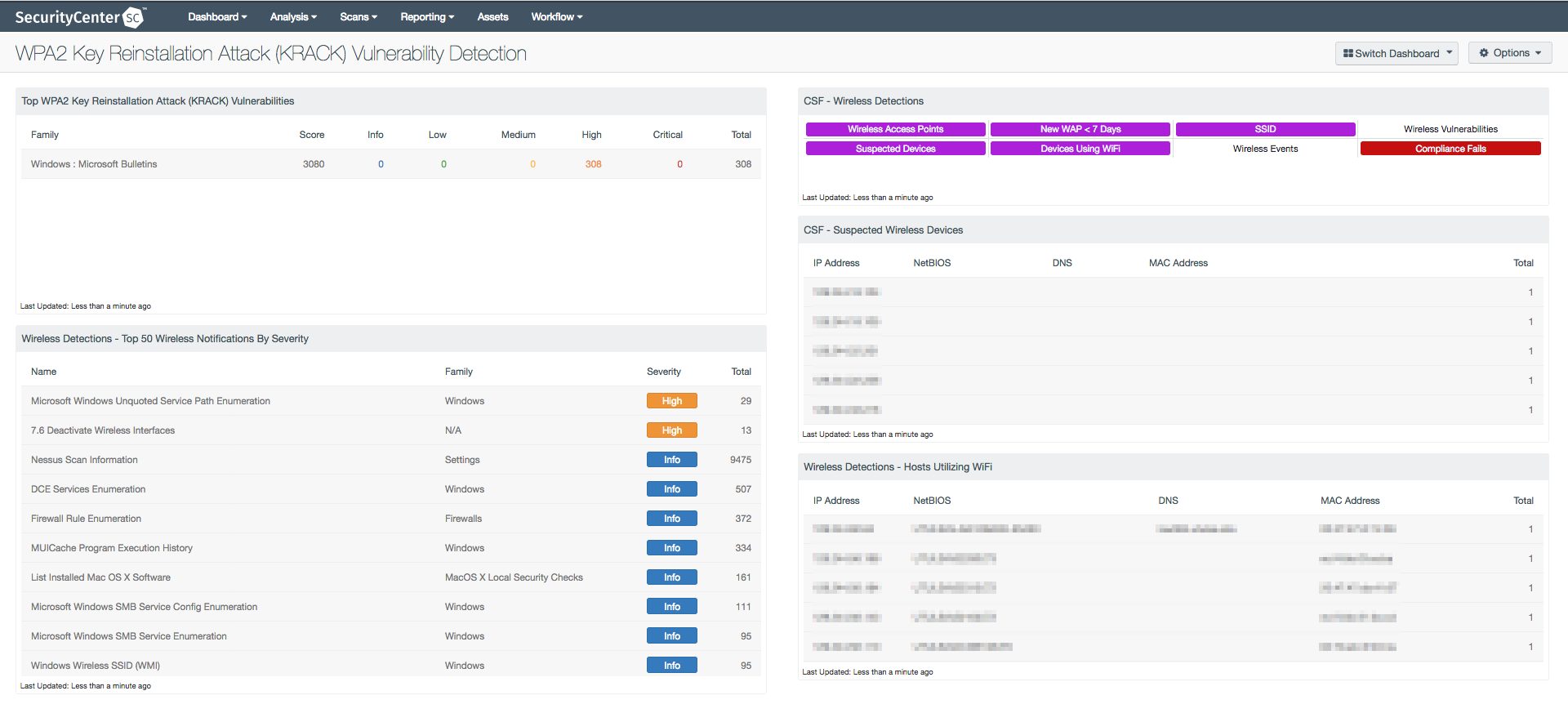
Top WPA2 Key Reinstallation Attack (KRACK) Vulnerabilities: This component displays information on discovered KRACK vulnerabilities by plugin family. This information enables the analyst to determine if KRACK vulnerabilities are present and the types of machines that are most vulnerable.
Wireless Detections - Top 50 Wireless Notifications By Severity: This component displays a list of the Top 50 most prevalent detections using the vulnerability summary tool, sorted by total. The table presents the analyst with a method to view detections in a readable format.
CSF - Wireless Detections: This component presents a breakdown of detected wireless access points, wireless vulnerabilities, and wireless event activity on the network.
CSF - Suspected Wireless Devices: This component displays devices by IP address, NetBIOS, DNS, and MAC address that contain wireless interfaces.
Wireless Detections - Hosts Utilizing Wi-Fi: This component displays host with active wireless interfaces.