by Andrew Freeborn
January 20, 2016
Organizations face threats that are typically thought of as originating from external sources. Defenses such as appliances and software packages were traditionally deployed and continue to be a common practice with defense in depth strategies. Many resources are spent focusing on keeping out external threats to deter the adversary. Unfortunately, modern attacks are not limited from external to internal threat vectors.
Attacks to organizations can originate from an internal presence or slip past external defenses to create an internal presence. Many times, attacks will beacon out to signal presence to an attacker or exfiltrate data. Analysts need a dashboard that can detect these kinds of threats to known bad external networks. Connections to or from known bad external networks can quickly signify malicious activity. This dashboard assists analysts in detecting malicious network activity internal and external to the organization from known bad external networks.
When organizations use Tenable’s Log Correlation Engine (LCE), they have access to events specific to these threats from adversaries. The event type is known as “threatlist” and combines a number of sources to provide organizations with up to date information needed to detect known bad IP addresses. As adversaries continue to change and evade mechanisms used to locate their IP address on the Internet, the threatlist event type is constantly updated.
LCE can be configured to specify which IP addresses should be included for internal IP address spaces. These IP addresses are configured in LCE as “included IP addresses”. There are two types of IP address spaces, inbound and outbound, as far as threatlist events are concerned. These help the analyst determine the direction of the network event. Threatlist events are a source of reliable detection methods to detect malicious events in the organization. Examples of inbound network events in the threatlist event type include detecting inbound SSH connections, VNC sessions and suspicious proxy traffic originating from the Internet. Examples of outbound network events in the threatlist event type include RDP sessions, scanning activity, FTP connections and data leakage out to the Internet. These events and others may not be typical to the organization and should be investigated as soon as possible. Analysts can detect these events with this dashboard and secure the network from unauthorized activity.
The dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Threat Detection & Vulnerability Assessments. The dashboard requirements are:
- SecurityCenter 4.8.2
- LCE 4.6.1
Tenable provides continuous network monitoring to identify vulnerabilities, reduce risk and ensure compliance. SecurityCenter Continuous View (CV) includes Nessus, Passive Vulnerability Scanner (PVS) and Log Correlation Engine (LCE). SecurityCenter CV performs log normalization from hundreds of unique data sources. LCE performs automatic discovery of users, infrastructure, and vulnerabilities across more technologies than any other vendor including operating systems, network devices, hypervisors, databases, tablets, phones, web servers and critical infrastructure.
This dashboard contains the following components:
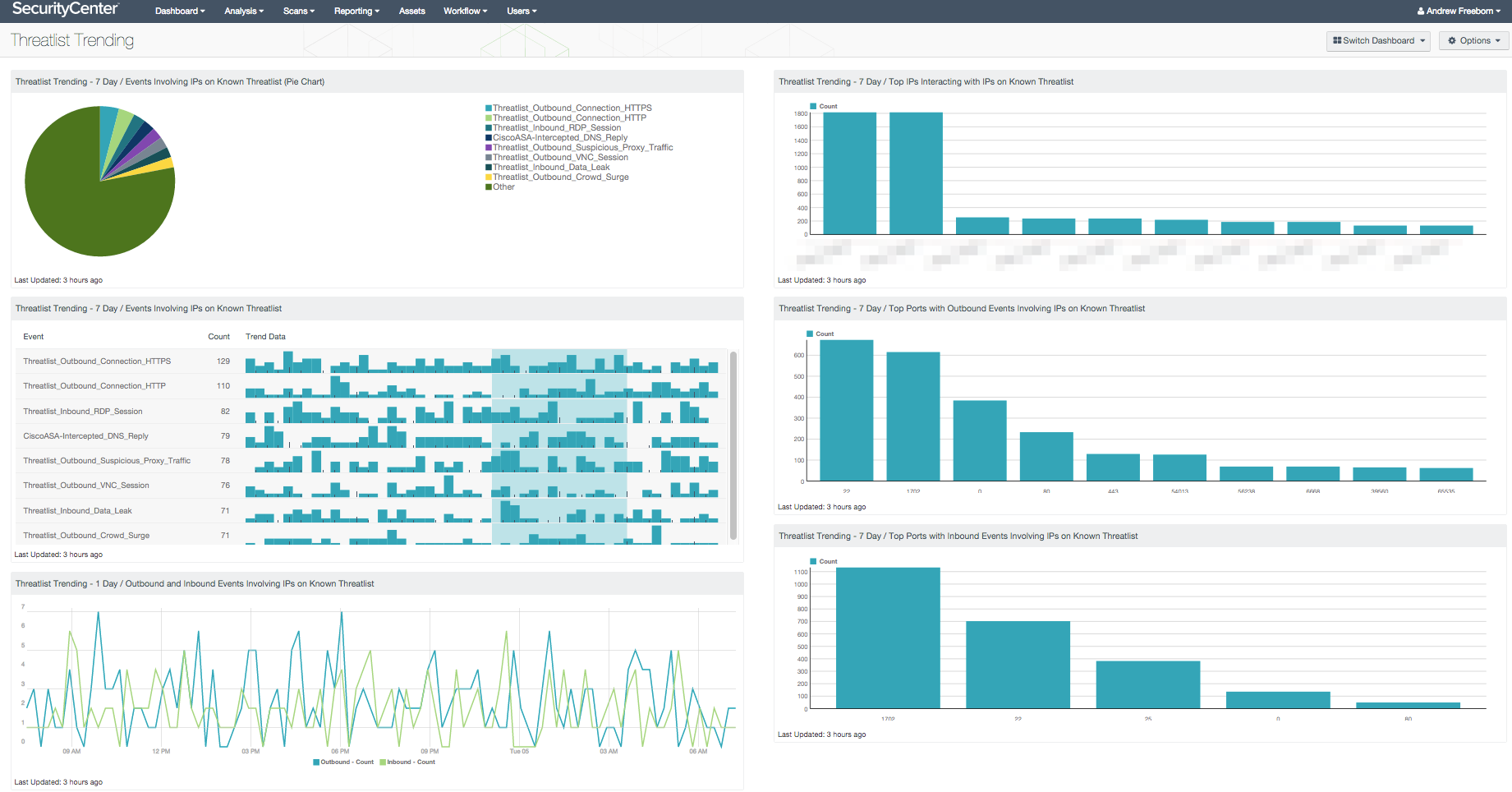
- 7 Day / Events Involving IPs on Known Threatlist (Pie Chart): The pie chart component displays event information relating to IP addresses found in the “threatlist” event type
- 7 Day / Events Involving IPs on Known Threatlist: The table component displays event information relating to IP addresses found in the “threatlist” event type
- 1 Day / Outbound and Inbound Events Involving IPs on Known Threatlist: This component displays line graphs of outbound and inbound events from the “threatlist” event type over the last 24 hours
- 7 Day / Top IPs Interacting with IPs on Known Threatlist: This bar chart component displays information about network traffic interacting with known malicious IP addresses
- 7 Day / Top Ports with Outbound Events Involving IPs on Known Threatlist: This component displays the IP addresses identified by the “threatlist” normalized events over the past 24 hours
- 7 Day / Top Ports with Inbound Events Involving IPs on Known Threatlist: This component displays the IP addresses identified by the “threatlist” normalized events over the past 24 hours