by Michael Willison
February 5, 2015
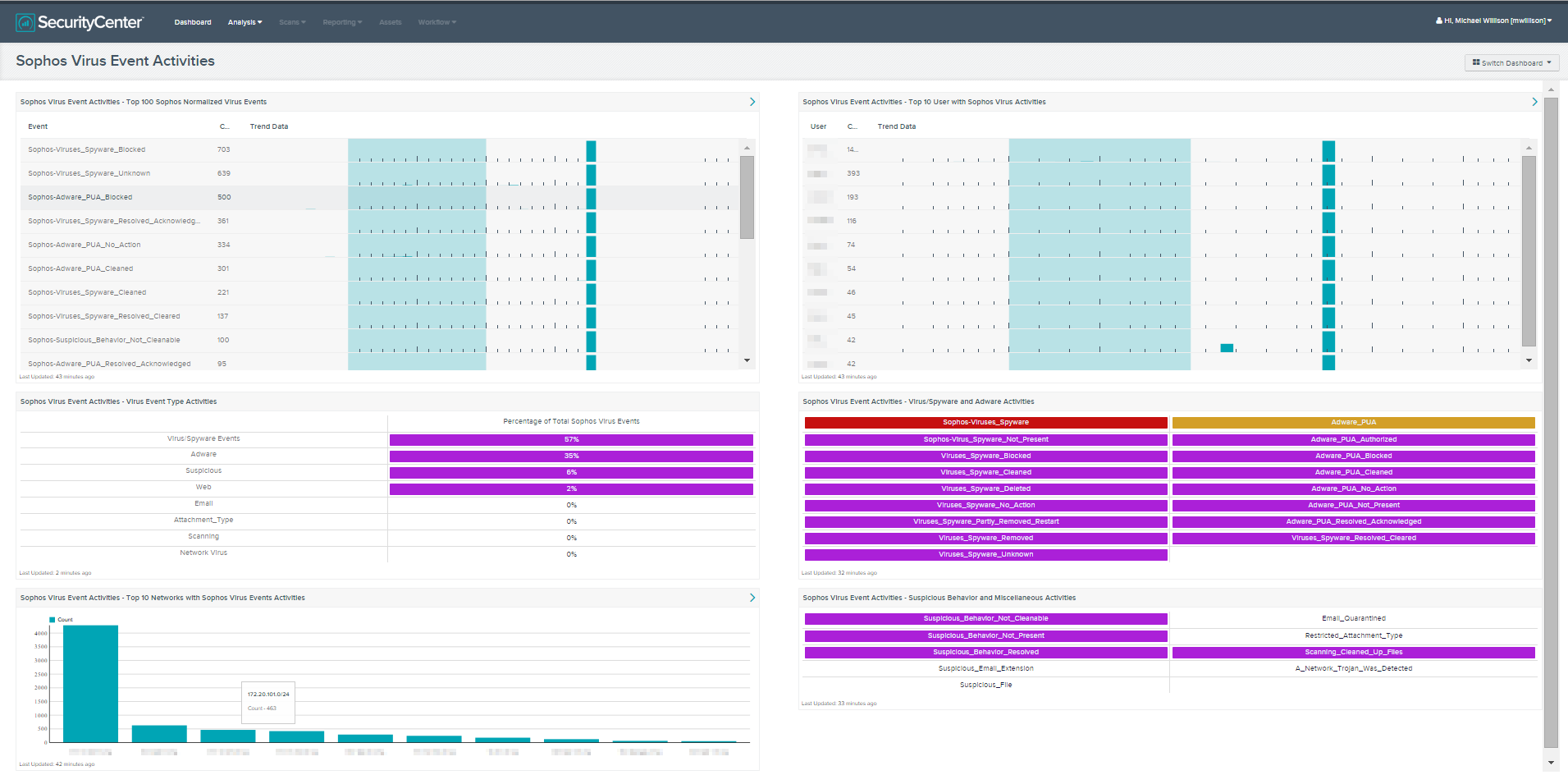
What viruses, spyware, and or adware are being detected by Sophos Endpoint security protection? Understanding the virus threat landscape on the network will help an analyst determine what threats are attempting to attack systems. SecurityCenter Continoues View (CV), in conjunction with the Log Correlation Engine (LCE), provides a single location to display virus event activities detected by Sophos.
Sophos Endpoint security protection detects viruses, spyware, adware, and malicious activities on the network. This dashboard queries the LCE for Sophos events and displays them through six components. The components included with this dashboard are a summary of the top 100 normalized Sophos virus events, top 10 users with Sophos virus events, the top 10 networks with Sophos virus normalized events, and three indicator tables that show activities detected during the last 7 days.
The dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Discovery & Detection.
The dashboard requirements are:
- SecurityCenter 4.7
- LCE 4.4.0
SecurityCenter Continuous View (CV) provides a centralized solution that allows for the most comprehensive and integrated view of network health. SecurityCenter CV with Log Correlation Engine (LCE), provides continuous network monitoring for Sophos virus event activity on the network. This central point of view provides the security analyst with the ability to continuously monitor Sophos virus activities.
This dashboard collection contains the following components:
- Sophos Virus Event Activities - Top 100 Sophos Normalized Virus Events: This component will display the top 100 Sophos normalized virus events over the last 7 days. For each Sophos normalized virus event, a trending chart is provided. By monitoring the top 100 virus events along with the trending data, the analyst can determine if the organization is under attack in a single location or globally.
- Sophos Virus Event Activities - Virus Event Type Activities: This component displays the percentage of Sophos virus events by detection over the last 7 days. There are eight types of virus event activities for Sophos Endpoint security protection. These are virus/spyware, adware, suspicious, web, email, attachment, scanning, and network. This component will provide the analyst the knowledge of which of these virus event types is being detected and is most prevalent during the last 7 days.
- Sophos Virus Event Activities - Top 10 Networks with Sophos Virus Events Activities: This component displays the top 10 subnets with Sophos virus events activities over the last 7 days. Viewing the data trending in this manner helps the analyst in several ways. The first helps to understand which subnets are being attacked most often and if this is a critical subnet network. By understanding the most at risk networks, other security policies may need adjustment, such as firewall rules or routing policies.
- Sophos Virus Event Activities - Top 10 User with Sophos Virus Activities: This component displays the top 10 users with the most Sophos virus events over the last 7 days. Understanding which users are experiencing the most virus events will allow the analyst to determine the appropriate action needed to address the compromise. In some cases, these actions may include educating users on company policy or ensuring systems are patched properly. Other mitigation efforts may include updating a host based firewall rule or reviewing other system configurations.
- Sophos Virus Event Activities - Virus/Spyware and Adware Activities: The Adware Potentially Unwanted Applications (PUA) and Virus/Spyware are two of the major types of threats detected from Sophos Endpoint security protection. The Virus/Spyware indicator will turn red if an event was detected in the last 7 days. The Adware_PUA indicator will turn orange if an event has been detected in the last 7 days. All other indicators are the type of actions against either Virus/Spyware or Adware_PUA events. Any of these other indicators will turn purple if an event was detected in the last 7 days.
- Sophos Virus Event Activities - Suspicious Behavior and Miscellaneous Activities: This component has nine indicators to display if any Sophos-detected suspicious virus behavior or miscellaneous activities have taken place in the last 7 days. A purple indicator represents a detection of information associated with these events. There are five indicators for suspicious virus event activities. The miscellaneous virus event indicators are restricted attachment type, scanning clean up files, and if a network Trojan was detected.