by Megan Daudelin
June 27, 2016
The Tenable.sc Research team created the PCI Access Control dashboard. User accounts are necessary to allow users to perform their assigned duties. Analysts need to be able to monitor and protect user accounts for not only the needs of the organization but to also adhere with PCI security requirements. This dashboard can assist security teams with monitoring access control measures and adhering to PCI requirements. The dashboard is currently available within the Feed.
The Payment Card Industry Security Standards Council (PCI SSC) maintains, evolves, and promotes Payment Card Industry standards for the safety of cardholder data across the globe. The PCI SSC provides organizations with technical and operational requirements for organizations accepting or processing payment transactions, and for software developers and manufacturers of applications and devices used in those transactions.
The Payment Card Industry Data Security Standard (PCI DSS) helps entities understand and implement standards for security policies, technologies and ongoing processes that protect their payment systems from breaches and theft of cardholder data. The standards have historically been revised on a 2-3 year cycle, but the PCI SSC is transitioning to a posture of revising the PCI DSS as required based on changes to the current threat landscape. The current standard revision is PCI DSS Version 4.x. Any organization that handles payment card information must comply with the PCI DSS and must demonstrate compliance annually. Tenable Security Center is able to help organizations monitor ongoing PCI DSS compliance.
Users of all access control levels play an important part in all organizations. Some users ensure the security of an organization whereas others further the business goals. Regardless of the user account, if the user account is active and has permissions, there could be a possibility of compromise. Analysts need to ensure that care is taken to protect all user accounts and monitor for suspicious activity. Many organizations have a sense of belief that all user accounts are trusted within the network boundaries and are performing authorized activities. Attackers use various techniques to get credentials of any user account possible to get a foothold into the inside of the organization. Tenable has products such as Nessus, NNM, and LCE to provide organizations with a continual view into the network. Using these products within Tenable Security Center, analysts can help detect threats to user accounts with tools such as this dashboard.
With this dashboard, organizations can assess their level of adherence with PCI security requirements focusing on access control. The components in this dashboard are focused on PCI Control Objective 4, Implement Strong Access Control Measures. The components in this dashboard cover elements within PCI Requirements 7, and 8.
Within this dashboard, user account focused components are provided to help analysts see activities detected in the organization around user accounts. All user accounts such as regular user accounts and administrative accounts should be monitored for unusual activity. Multiple industry recommendations from standards such as PCI and NIST CyberSecurity Framework (CSF) are provided to help analysts see potential malicious indicators around user accounts. Examples of these indicators, such as privilege changes and group membership changes, alert analysts as changes may not be expected and should be validated. Analysts can use these components to help determine what typical activity should be on a network and then be more aware of when abnormal activity takes place within the organization.
Organizations can configure repositories or asset lists in order to tailor the focus of the dashboard. When the dashboard is added from the Tenable Security Center Feed, the appropriate assets, IP addresses, or repositories can be specified. Assigning one of the options to the dashboard will update all filters in the components. By creating static or combination asset lists that include all systems in the Cardholder Data Environment (CDE), each component can be filtered to display results directly related to ongoing PCI security. Using an asset list filter will also allow traffic into and out of the CDE to be monitored. In order to accurately measure an organization’s PCI security posture, asset lists need to be applied as filters to provide results focused on the CDE.
This dashboard is available in the Tenable Security Center Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable Security Center Feed under the category Compliance & Configuration Assessments. The dashboard requirements are:
- Tenable Security Center
- Nessus
- NNM
Tenable's Tenable Security Center provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. Tenable Security Center is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. Tenable Nessus Network Monitor (NNM) performs deep packet inspection to enable discovery and assessment of operating systems, network devices, hypervisors, databases, tablets, phones, web servers, cloud applications, and critical infrastructure. Tenable Log Correlation Engine (LCE) performs deep log analysis and correlation to continuously discover and track systems, applications, cloud infrastructure, trust relationships, and vulnerabilities. By integrating with Nessus, and NNM, Tenable Security Centers continuous network monitoring is able to detect systems and vulnerabilities across the enterprise.
This dashboard contains the following components:
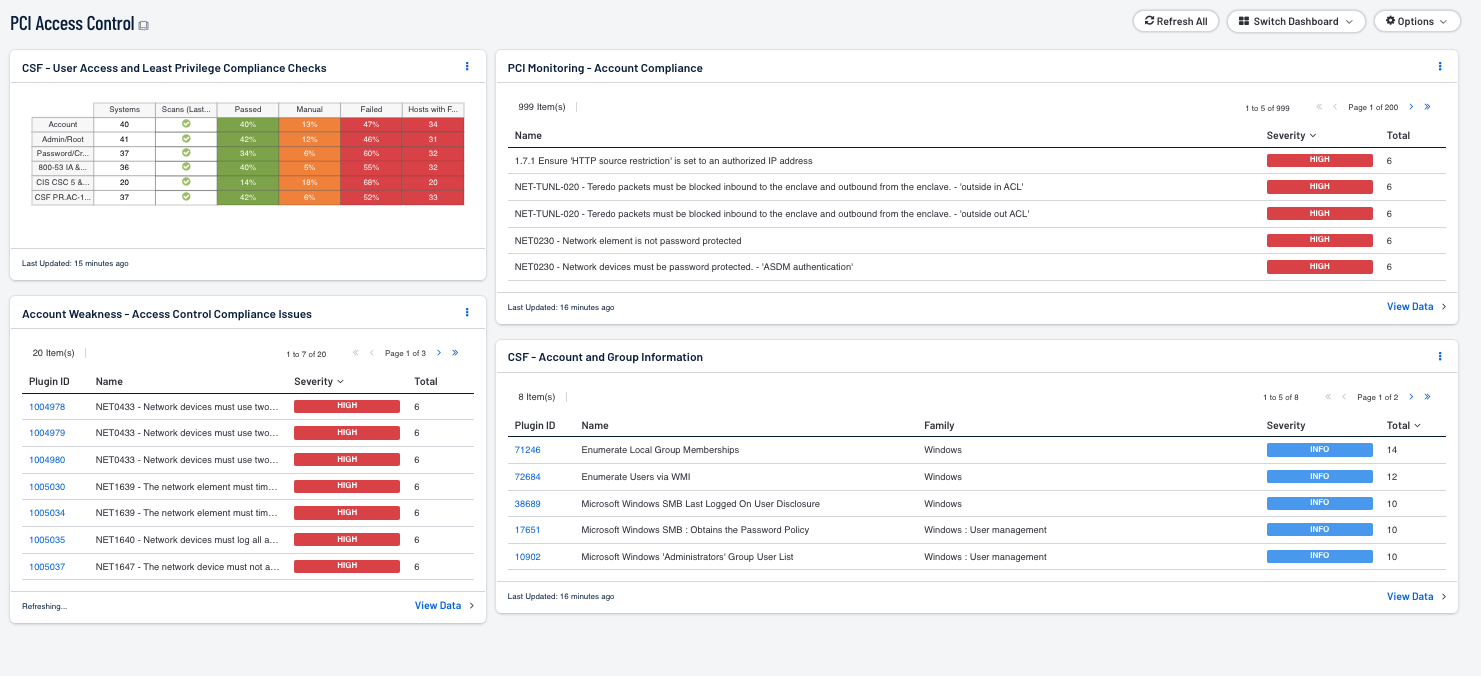
- CSF - User Access and Least Privilege Compliance Checks: This component displays user access and least privilege compliance information in areas such as password requirements, lockout policy after failed logins, and controlled use of administrative privileges.
- Account Weakness - Access Control and Compliance Issues: This component displays a table of compliance checks related to an organization's access control.
- PCI Monitoring - Account Compliance: The “PCI Monitoring - Account Compliance” table component lists account compliance plugin detections that match various security standards.
- CSF - Account and Group Information: This table displays detections of account and group information, such as accounts that have never been logged into, disabled accounts, and group user lists.