by Cesar Navas
October 10, 2016
Protecting and retaining records, monitoring systems security alerts, and identifying system flaws in a timely manner are essential to protecting information systems. Monitoring inbound and outbound communications is essential to detect attacks, and potential indicators of attacks. Improperly maintained systems, accounts, or audits will hinder investigations concerning inappropriate system activity, and may potentially allow attackers opportunities to exploit them.
The federal government relies heavily on external service providers and contractors to assist in carrying out a wide range of federal missions. Sensitive but unclassified federal information is routinely processed by, stored on, or transmitted through nonfederal information systems. Failing to properly protect this Controlled Unclassified Information (CUI) could impact the ability of the federal government to successfully carry out required missions and functions.
The National Institute of Standards and Technology (NIST) created Special Publication 800-171 "Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations" to provide recommended requirements for protecting the confidentiality of CUI. Federal agencies should use these requirements when establishing contracts and agreements with nonfederal entities that process, store, or transmit CUI.
This dashboard aligns with the Audit and Accountability (section 3.3) and System and Information Integrity (section 3.14) families of security requirements in NIST SP 800-171. These families are closely related and requirements focus on the monitoring, analysis, investigation, and reporting of unlawful, unauthorized, or inappropriate information system activity, including inbound and outbound communications traffic, to detect attacks and indicators of potential attacks. Using this dashboard, an organization will be better able to correlate audit review, analysis, and reporting processes for investigation and response to indications of inappropriate, suspicious, or unusual activity. Organizations will also be able to monitor information system security alerts and advisories and take appropriate actions in response.
Components in this dashboard assist in the review, analysis, and reporting processes for investigation and response to indications of inappropriate, suspicious, or unusual activity. This information will assist the organization in managing and properly restricting access to information systems that process, store, or transmit CUI. Analysts can use this dashboard to easily drill down into the data presented and gain more detailed information. If necessary, assets or subnet filters can be used to narrow the focus of this dashboard to only those systems that process, store, or transmit CUI.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.4.0
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.1
- Compliance data
Tenable Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring solution, and can assist an organization in monitoring inappropriate information system activity. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new regulatory compliance data. Active scanning periodically examines systems to find vulnerabilities, and can also make use of audit files to assess compliance. Passive listening provides real-time monitoring to collect information about systems and vulnerabilities. Host data and data from other security devices is analyzed to monitor inbound and outbound communications traffic, to detect attacks and indicators of potential attacks.. Tenable.sc CV provides an organization with the most comprehensive view of the network and the intelligence needed to secure systems and safeguard sensitive information.
The following components are included in this dashboard:
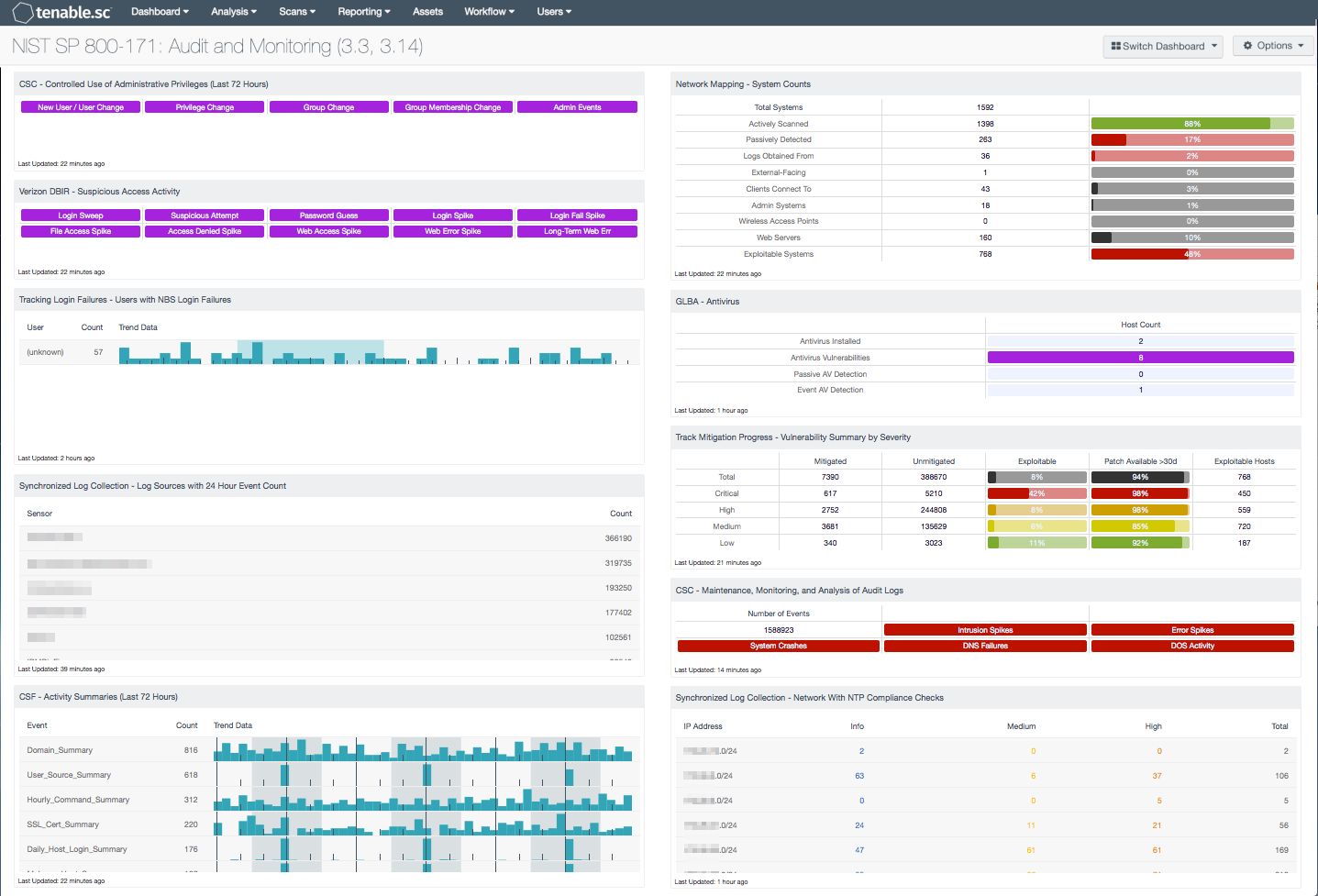
- CSC - Controlled Use of Administrative Privileges (Last 72 Hours): This component presents indicators of events related to user accounts and administrative privilege use. Indicators are included for new user and user account change events, privilege change events, and group and group membership change events. An indicator is also included for events that report performed or attempted administrative actions. Clicking on a highlighted indicator will bring up the event analysis screen to display details on the events and allow further investigation. In the analysis screen, setting the tool to Raw Syslog will display the raw syslog of the events, which can give more details. Any unexpected events should be further investigated.
- Verizon DBIR - Suspicious Access Activity: This matrix assists the organization in monitoring for suspicious access activity such as suspicious login activity and spikes in file and web accesses. Each indicator is based on one or more LCE events; the indicator is highlighted purple if the event occurred in the last 72 hours. Login spikes can occur when an account is compromised and shared and used by many hackers. Login failure spikes may indicate brute-force password guessing. File access and access denied spikes may indicate suspicious access to files. Web access spikes may indicate a busier-than-normal web server or more Internet browsing. Web error spikes and long-term Web errors can identify web application scanning and web probes. Clicking on a highlighted indicator will bring up the analysis screen to display details on the events and allow further investigation.
- Tracking Login Failures - Users with NBS Login Failures: This component displays the last 7 days of users with never before seen login failure events, along with their associated counts and trend data. The top 200 users with the highest number of never before seen login failures are presented. Spikes in login failure events may indicate unauthorized access attempts, and should be investigated further.
- Synchronized Log Collection - Log Sources with 24 Hour Event Count: This component identifies log sources and helps the organization ensure that all systems that can send logs are sending them to LCE and/or allowing NNM to scan them. Identifying patterns of suspicious behavior using NNM, and sending these logs to the LCE, will show correlated events across multiple workstations and servers. This practice enables investigation and auditing functions to be easier and more effective should an intrusion occur.
- CSF - Activity Summaries (Last 72 Hours): This table displays all summary events generated by the LCE in the last 72 hours. The LCE maintains summaries of the various event information it receives and periodically creates summary logs, such as summaries of visited Internet domains, hourly summaries of commands issued on hosts, and daily summaries of users active on hosts. This table can be used by an analyst to investigate recent network activity of interest. Clicking on the Browse Component Data icon will bring up the event analysis screen to display the summary events and allow further investigation. In the analysis screen, clicking on a particular event will display all occurrences of that event. Setting the tool to Raw Syslog will display the raw syslog of the events, which can give more details.
- Network Mapping - System Counts: This component presents the counts of systems detected on the network in various categories. The total number of systems is displayed, along with the counts of actively scanned systems detected by Nessus, passively detected systems discovered by NNM, and systems from which LCE obtained logs. For these, percentages of the total system count are displayed. The percentage bar color reflects coverage and will be red for a low percentage of total systems, yellow for a medium percentage, and green for a high percentage. In addition, counts of external-facing systems, systems that clients connect to (servers), admin systems, wireless access points, and web servers are also displayed. For each of these, percentages of the total system count are displayed with black bars. Finally, the count of exploitable systems on the network is displayed, along with a percentage bar displayed in red. Using this matrix, organizations will be able to gain a more complete picture of existing assets and high-valued systems on the network. Clicking on a highlighted indicator will bring up the analysis screen to display the specific systems and allow further investigation.
- GLBA - Antivirus: The Antivirus dashboard component leverages the Nessus antivirus auditing plugins to report known antivirus installations and identified vulnerabilities.
- Track Mitigation Progress - Vulnerability Summary by Severity: Tenable.sc records when vulnerabilities are discovered, when patches are issued, and when vulnerabilities are mitigated. This component assists in tracking vulnerability mitigations. In the matrix, the row with red is critical severity vulnerability information, the row with orange is high severity, the row with yellow is medium severity, and the row with green is low severity. The Mitigated column displays the number of vulnerabilities that have been moved to the mitigated database. A vulnerability is moved to the mitigated database when the vulnerability is no longer detected by a rescan; the vulnerability is assumed to be remediated. The Unmitigated column displays the number of current vulnerabilities that are not yet remediated and have not been moved to the mitigated database. The Exploitable column displays the percentage of those unmitigated vulnerabilities that are known to be exploitable. The Patch Available column displays the percentage of the unmitigated, exploitable vulnerabilities that have had a patch available for more than 30 days. Ideally, both of these percentages should be 0%, because all exploitable vulnerabilities and all vulnerabilities with patches available should have been mitigated already. The Exploitable Hosts column displays the number of hosts on the network that have unmitigated, exploitable vulnerabilities.
- CSC - Maintenance, Monitoring, and Analysis of Audit Logs: This component displays a total for the number of Normalized Events seen over the past 48 hours. Also displayed are indicators of log items that may be of importance, such as DOS events, DNS failures, error, system crashes, and firewall spikes.
- Synchronized Log Collection - Network With NTP Compliance Checks: This component reports on audit checks that verify the NTP settings on subnets. Centralized and time-synchronized logging, and timely log analysis will increase an organization's ability to rapidly identify patterns of suspicious behavior and correlate logged events across multiple workstations and servers. This practice enables investigation and auditing functions to be easier and more effective should an intrusion occur.