by Cody Dumont
June 30, 2015
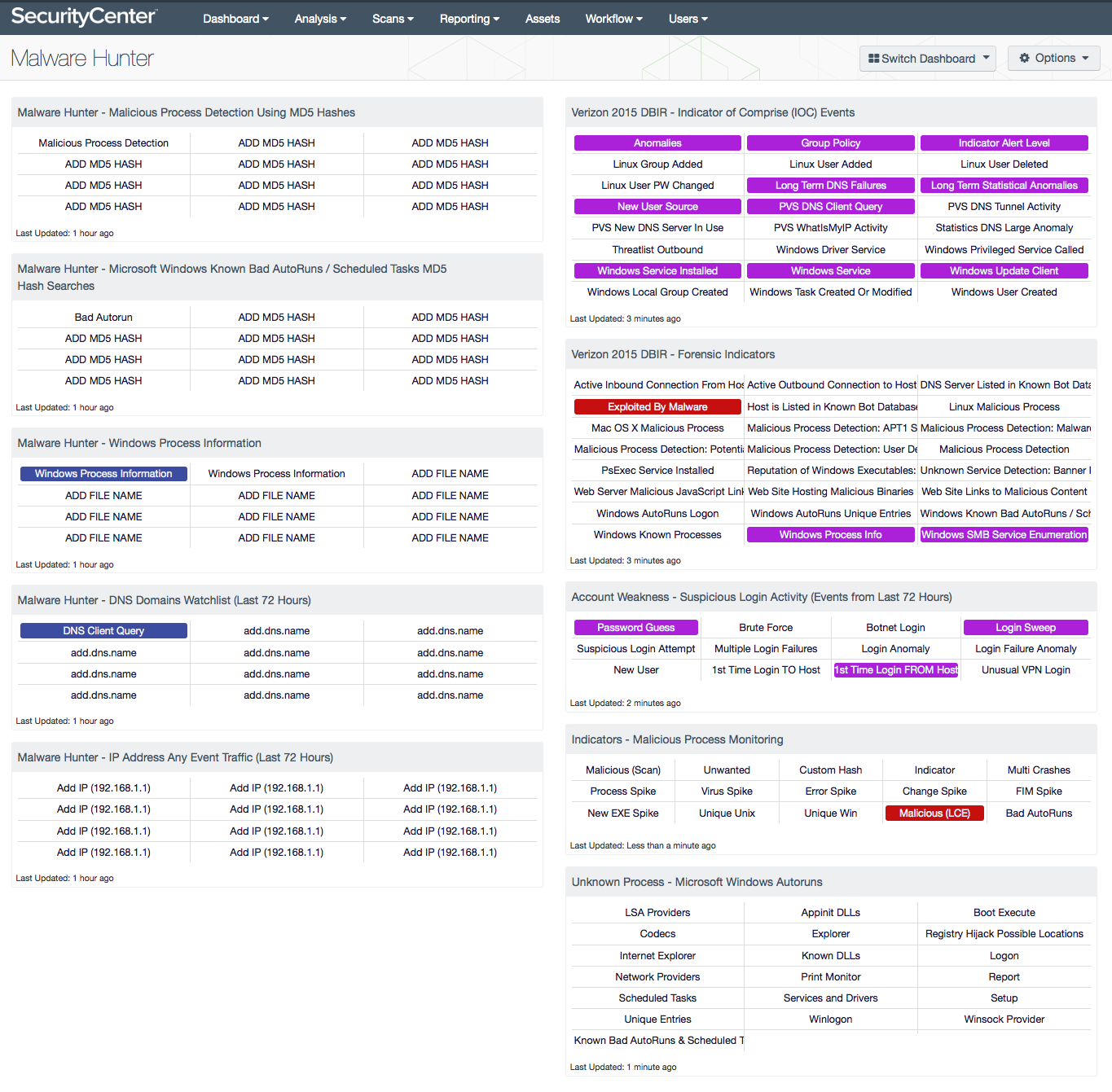
New versions of malware are identified daily and creating a custom dashboard for each malware can become difficult. This dashboard provides two sets of components. One set of template components, and another set with several Indicators of Compromise (IOC).
Continuous Network Monitoring provides several methods of detecting Indicators of Compromise (IOC). Defined by NIST, Continuous Network Monitoring is “maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational risk management decisions”. Ron Gula published this paper on Continuous Monitoring. Using SecurityCenter Continuous View (CV), analysts can use Active and Passive scanning along with deep log analysis to hunt for malware.
The dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Threat Detection & Vulnerability Assessments.
The dashboard requirements are:
- SecurityCenter 4.8.2
- Nessus 6.3.6
- LCE 4.4.1
- PVS 4.2.1
To get started with Continuous Monitoring, first start by passively scanning the network using Tenable’s Passive Vulnerability Scanner (PVS). PVS Sensors should be placed in strategic locations across the network. Next, setup the Log Correlation Engine (LCE) to collect logs from servers, network equipment, firewalls, and workstations. Also, ensure that PVS is sending log data to the LCE. Next, setup LCE to collect Netflow and/or use the Network Monitor Agent, which allows the LCE to analyze network traffic in real time. Finally, as the organization starts to identify assets on the network, active scanning can begin using Nessus. Active scanning should use network credentials, and administrators should make sure that the scanning policies check for Windows AutoRuns, Banner Detection, Process Enumeration, and Service Enumeration.
For this blog post we will use the recently identified POSeidon malware. Kenneth Bechtel, a Malware Research Analyst for Tenable, regularly posts information in the forums Indicators of Compromise and Malware. Recently, Ken discussed the POSeidon malware. For a more detailed “How To” guide, look in the SecurityCenter Forums. POSeidon is one of the newly discovered POS-targeting malware. POSeidon is rather unique, as it includes a memory scraper and key logger.
Now that the organization is monitoring the network, the analyst can start looking for files created by POSeidon. POSeidon is known to create several executables on affected systems: pes13.exe, pes13l.exe, pes13n.exe, and several others. Also (random).exe – A random string of characters. This will have to be searched for manually. Using plugin 70329 Microsoft Windows Process Information, the details on the running processes on the Windows computer are reported. This plugin is used for forensic investigation, malware detection, and to confirm that system processes conform to system policies.
Analysts should also be monitoring network traffic. When looking for IP addresses of network traffic, DNS queries monitored by PVS and logs collected by the LCE can provide a detailed list of all DNS queries on the network. Network devices that use NetFlow can send traffic analysis to the LCE NetFlow collector, and the Network Monitor Client can also collect NetFlow information. Network traffic can also be identified from other logs such as web and mail servers. Monitoring all of these possible sources will provide analysts with the best chance at collecting network traffic flows.
Another place to look is in known bad files using the File Hash Search plugins. Using these plugins, the analyst can search using specific plugin ID’s and Vulnerability Text field by simply adding the file hash of interest to vulnerability text field.
As mentioned earlier, this collection provides two sets of components, the templates and IOC components. The template components are on the left, while the IOC components are on the right. Each of the components on the left has placeholders for the field that needs to be modified. The term in the indicator “ADD MD5 HASH”, “ADD FILE NAME”, “add.dns.name”, or “Add IP (192.168.1.1)” provide information of filter that needs to be updated by the user. All the components on the right hand side are ready to use as configured. For more information about how to edit the dashboard see the How-To guide.
SecurityCenter Continuous View (CV) provides Continuous Threat Intelligence, which is more than vulnerability management. SecurityCenter CV allows organizations to identify IOC’s, malware, malicious activity, trust relationships, suspicious events, and so much more. SecurityCenter CV supports more technologies than any other vendor including operating systems, network devices, hypervisors, databases, tablets, phones, web servers, and critical infrastructure. Tenable covers all types of users and services, regardless of location, 100% of the time.
Components
Malware Hunter - Malicious Process Detection Using MD5 Hashes: This component uses the Malicious Process Detection plugins to monitor for the associated MD5 hashes identified by the FBI. Additionally, an indicator is used to help identify all the Malicious Process Detection plugins currently in SecurityCenter. There are several plugins to identify malicious processes, of which some focus on operating systems such as Windows, Linux, or Mac OS X. Others allow for security administrators input their own MD5 hashes and check for MD5 hashes identified by Mandiant.
Malware Hunter - Microsoft Windows Known Bad AutoRuns / Scheduled Tasks MD5 Hash Searches: This component provides indicators of possible malware using the reputation Microsoft Windows Known Bad AutoRuns / Scheduled Tasks plugin. Plugin 74442 (Microsoft Windows Known Bad AutoRuns / Scheduled Tasks) shows that the Windows system has one or more registry entries that are known to be associated to malware.
Malware Hunter - Windows Process Information: This component monitors Microsoft Windows process information. While the plugin is mostly informative, this information is often used for forensic investigation and malware detection purposes.
Malware Hunter - DNS Domains Watchlist (Last 72 Hours): This component provides a series of indicators that report on DNS query events detected by PVS and logged to LCE. The indicators need to be modified to contain a FQDN of the domain name the organization is looking for. Each malware version often uses some sort of a call-home or command-and-control method to contact the malware source. This matrix allows the analyst to monitor specific DNS patterns. Search for DNS queries captured by PVS using the “PVS-DNS_Client_Query” Normalized Event. The raw message will contain a statement similar to this: The most recent DNS query performed was for: www.google.com to the server at 10.31.15.1. The FQDN can be searched for using keyword searches and Boolean logic. However, there is one important detail to remember: when searching the syslog text all punctuation is removed, and replaced with an AND, resulting in www.google.com being translated to www AND google AND com.
Malware Hunter - IP Address Any Event Traffic (Last 72 Hours): This component indicates if specific IP addresses have been seen in LCE events over the last 72 hours. These events were collected using PVS, LCE Client, Netflow, or by other LCE collection methods. Each of these cells must be modified to reflect the targeted malware. Each malware version often uses some sort of a call-home or command-and-control method to contact the malware source. This component allows the analyst to track any communication with the malicious addresses.
Verizon 2015 DBIR - Indicator of Comprise (IOC) Events: This component provides a quick indicator for logs commonly triggered by malware. While the presence of these events is not proof of malware, malware can often trigger these events. For example the “Windows Service” indicator will report on all events related to services running on Microsoft Windows operating systems. These events should be monitored on a normal basis and should not change very often. Analysts should monitor these events to look for anomalies within their environment.
Verizon 2015 DBIR - Forensic Indicators: This component provides a quick indicator for vulnerabilities that commonly provide evidence of malware. While the presence of these vulnerabilities is not necessarily proof of malware, malware can often modify system services or registry settings leaving evidence of the presence of malware. For example the “Microsoft Windows AutoRuns Logon” indicator will report on all tasks and services to be run when a user logins to a system. Malware will often attempt to hide itself as an authorized service and use AutoRun as method of long-term access. These plugins should be monitored on a normal basis and should not change very often. Analysts should monitor these events to look for anomalies within their environment.
Account Weakness - Suspicious Login Activity (Events from Last 72 Hours): This matrix shows potentially suspicious login activity. This activity can bring attention to accounts that are more threatened and require greater protection.
Indicators - Malicious Process Monitoring: This component takes many of the various detection technologies for botnets, malicious file hashes, anomalous network traffic, spikes in system logs and continuous scanning activity and places them into one spot.
Unknown Process - Microsoft Windows AutoRuns: This indicator component triggers on each one of the 18 autorun active Nessus plugins.