by Stephanie Dunn
December 2, 2016
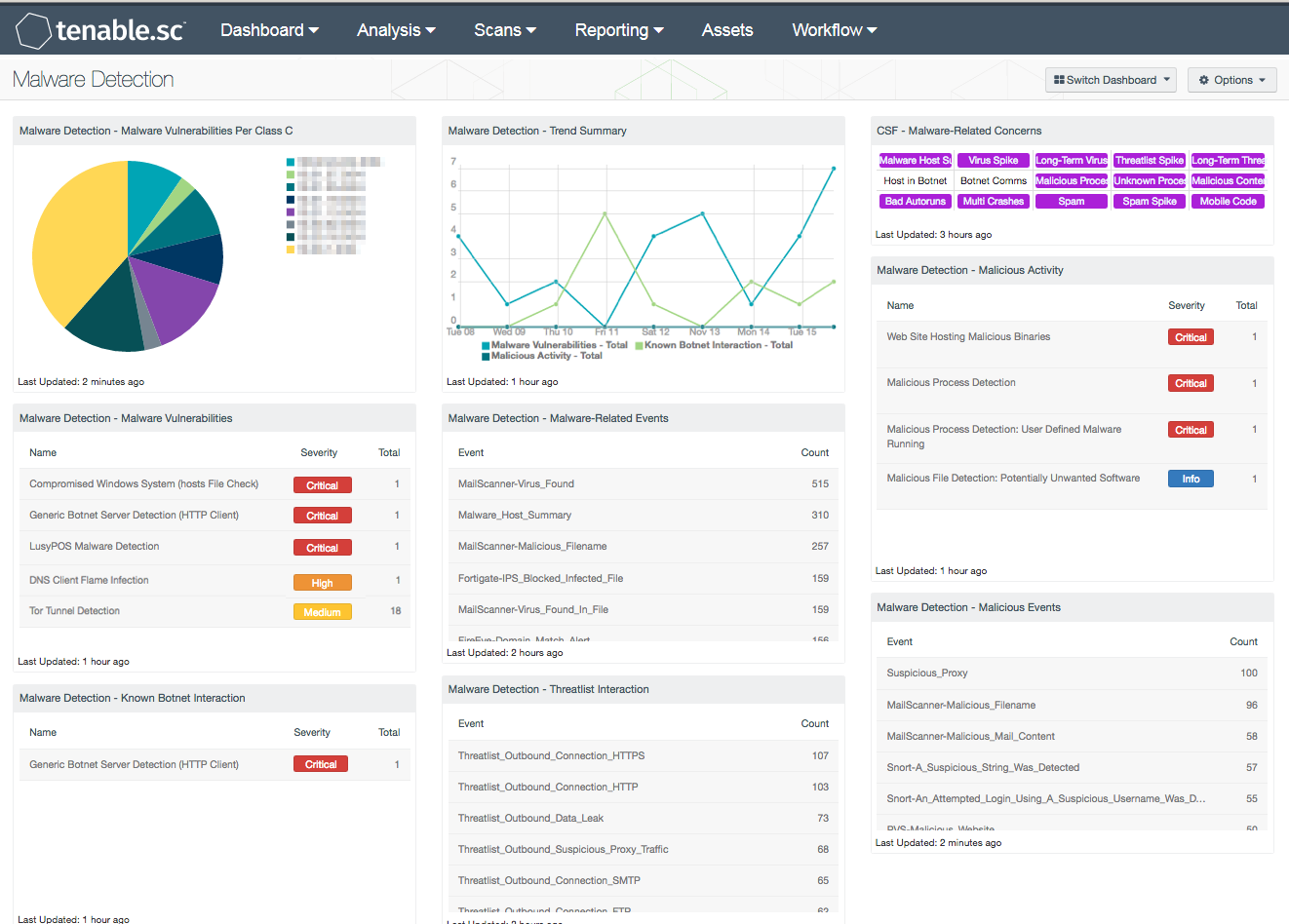
Malware remains a constant and ever-growing threat among organizations. Even with anti-virus systems in place, advanced malware can still bypass these solutions and propagate throughout a network. Systems can become infected from users accessing a compromised website, which can install malware and other malicious software. Malware variants can allow for long-term persistence, provide a backdoor to internal systems, or exfiltrate confidential data on demand. The Malware Detection dashboard can assist the organization in monitoring the enterprise for potential malware infections, botnet interactions, malicious processes, and malware event activity.
Even with the best security solutions in place, organizations must accept that at some point their network will be breached. One critical part of keeping the network secure is enabling a continuous monitoring strategy and monitoring of all possible network endpoints. Information gathered from Tenable Nessus, Tenable Nessus Network Monitor (NNM), and Tenable Log Correlation Engine (LCE) will provide organizations with a complete picture of malicious activity, malware infections, and compromised hosts. In order to gain additional information from logs, analysts should setup LCE to collect logs from all network devices, and ensure that NNM is sending log data to LCE.
This dashboard provides a detailed view of potential malware, suspicious processes, and malicious activity. Analysts will be able to easily identify malware activity on hosts. Event data will provide valuable information from devices and services on suspicious files, unauthorized logins, malicious websites and requests, and more. Systems are scanned for malicious backdoors, botnet activity, potential malware being hosted on web servers, and unknown processes. A summary of both outbound threatlist interactions and malware events will draw attention to systems communicating with botnets or other malicious hosts. Spikes in trend activity can indicate changes from anti-virus clients, detection of newly discovered malware, and malicious file detection. Information provided within this dashboard will provide organizations with the ability to detect, respond, and recover more effectively, thus allowing organizations to stay on top of the challenging threat landscape.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Threat Detection & Vulnerability Assessments. The dashboard requirements are:
- Tenable.sc 5.4.0
- Nessus 8.6.0
- NNM 5.9.0
- LCE 6.0.0
Tenable Network Security transforms security technology for the business needs of tomorrow through comprehensive solutions that provide continuous visibility and critical context, enabling decisive actions to protect the organization. Tenable's Tenable.sc is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audit files. Active scanning examines running systems and services, detects vulnerable software applications, and analyzes configuration settings. Passive listening collects data to continuously monitor traffic, collect information about user privilege changes, and administrative activity, along with the discovery of additional vulnerabilities. Host data and data from other security products is analyzed to monitor for malware and malicious activity on the network. Monitoring the network to ensure that all systems are secured against vulnerabilities is essential to ongoing security efforts. Tenable enables powerful, yet non-disruptive, continuous monitoring that will enable organizations with the information needed to proactively respond to threats within the enterprise.
The following components are included within this dashboard:
- Malware Detection - Malware Vulnerabilities Per Class C: This component presents a Class C summary of malware activity detected over the last seven days. Data is filtered by the 'Backdoors' family of plugins for both Nessus and NNM. These detections indicate hosts with known Trojans, viruses, and other forms of malware on them. Analysts can use this information to quickly identify and remediate malware on network hosts. By clicking on the Browse Component Data icon, and setting the tool to Vulnerability Detail List, analysts can obtain additional information on the vulnerability, hosts involved, and potential solutions to remediate the vulnerability.
- Malware Detection - Malware Vulnerabilities: This component displays a summary of vulnerabilities detected in the last seven days by the 'Backdoors' family of plugins for both Nessus and NNM. These detections indicate hosts with known Trojans, viruses, and other forms of malware on them. For each finding, the severity and total number of detections are shown. Analysts can drill down and obtain additional information on the find, hosts involved, and potential solutions to remediate the issue.
- Malware Detection – Known Botnet Interaction: This component displays a summary of client/server botnet detections across the enterprise over the last seven days. These detections indicate hosts interacting with known botnets, which might indicate that the hosts are infected with malware. For each vulnerability, the severity and total number of detections are shown.
- Malware Detection – Trend Summary: This component displays trends for various malware-related activity over the last seven days. Information presented within this component will highlight changes of software altered potentially by malware, malware events, and related activity. Any spikes should be further investigated, as they may indicate botnet activity, hosts that have been infected, or interaction with malicious hosts. Using this information, analysts can quickly identify and remediate malware infections on hosts throughout the network.
- Malware Detection – Malware-Related Events: This component displays a summary of events of type 'virus' that have occurred in the last seven days. Information presented within this component can assist analysts in detecting malware activity on hosts within the network. These events were reported by various applications and collected by LCE. For each event, the count of occurrences is shown. Event data can be filtered to include specific activity per organizational requirements.
- Malware Detection - Threatlist Interaction: This component displays a summary of outbound events of type 'threatlist' that have occurred in the last seven days. Outbound events are IP addresses considered internal to your network, going to addresses that are external to your network. These events may indicate hosts on the network that are infected with malware, and analysts can make use of this information to discover the infected hosts. LCE maintains a list of hostile IP addresses that are known to be involved in botnets.
- CSF - Malware-Related Concerns: This matrix displays warning indicators for potential malware-related events and vulnerabilities detected on the network, such as virus and threatlist event spikes, botnet interactions, malicious processes and web content, bad Windows autoruns, multiple system crashes, and detections of spam and mobile code. Clicking on a highlighted indicator will bring up the analysis screen to display more details and allow further investigation. In the analysis screen, setting the tool to IP Summary will display the systems on which the detections and events occurred. For vulnerability detections, setting the tool to Vulnerability Details will display the full details for each vulnerability, including a description, the solution to fix the vulnerability, and in some cases, links to more information. For events, setting the tool to Raw Syslog will display the raw syslog of the events, which can give more details. The LCE maintains 24-hour summaries of malware or virus events detected on hosts; these summaries can be viewed by clicking on the Malware Host Summary indicator.
- Malware Detection - Malicious Activity: This component displays a summary of malicious activity detected over the last seven days. For each finding, the severity and total number of detections are shown. Information presented within this component will alert analysts to hosts running potentially malicious processes, malicious files, and websites hosting malicious content. Tenable Nessus enumerates the list of running processes on the system and compares the MD5 hash of the process. A vulnerability is detected when the MD5 hash of the process matches a known malware hash. Analysts can obtain additional information by drilling down and setting the tool to Vulnerability Detail List. This tool provides information on IP addresses, malicious processes running, and potential remediation solutions for the malicious content.
- Malware Detection - Malicious Events: The Malicious Events component presents a list of the top malicious events detected on the network over the last seven days. The chart includes the top 10 normalized events, and is filtered on both malicious and suspicious events. Event data will highlight malicious requests, malicious binaries, suspicious behavior, suspicious login connections, compromised websites, and other related activity.