by Cesar Navas
July 7, 2020
The National Banking and Securities Commission (CNBV) Annex 72 is a collection of Key Risk Indicators (KRI) that establish compliance standards for financial institutions operating in Mexico. Financial institutions in Mexico should be prepared to divulge cyber risk KRIs to CNBV when requested. The KRIs relating to vulnerability management and anti-malware systems are grouped by asset function, for example the servers, workstation, network devices, and other asset types. This dashboard relates to the following KRIs: KRI0011, KRI0018- KRI0022
Financial institutions are naturally at a higher risk of being targeted and attacked. In an effort to minimize organizational risk it is vital to track vulnerabilities in the network. KRI0011 talks about knowing the count of critical vulnerabilities. Tenable.sc provides institutions with the ability to track the status of installed anti-virus solutions, and track discovery and mitigation of vulnerabilities. Annex 72 requires risk managers to provide evidence of vulnerability mitigation efforts.
By tracking when scans are completed and comparing the new scan to the previously collected data, the risk manager is able to identify when a risk is mitigated.
Many organizations frequently use managed anti-virus solutions to assist with remotely administering scans and pushing updates out to clients. However, issues with anti-virus clients can be the result of misconfigured policies or loss of communication between the client and anti-virus server. Although managed anti-virus solutions can provide greater visibility and control over clients, many organizations do not apply additional controls needed to protect systems from potential attacks. KRI0018-22 relates to knowing the number of servers and workstations without anti-virus or with outdated anti-virus.
This Dashboard is available in the Tenable.sc feed, which is a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The Dashboard can be easily located in the Tenable.sc feed under the Executive category. The dashboard requirements are as follows:
- Tenable.sc 5.14.1
- Nessus 8.10.1
- Compliance Data
This dashboard provides the organization with a clear and simplified method to identify and establish compliance according to Annex 72 by CNBV. The data can be Analyzed to provide more detail in non-compliant areas, which facilitates the Fix and Measuring steps to the Cyber Exposure Lifecycle. Tenable.sc is the On-prem solution for understanding the picture of the network, while keeping the data under the organization’s control. Built on leading Nessus technology, Tenable.sc discovers unknown assets and vulnerabilities, and monitors unexpected network changes before they turn into breaches.
Components
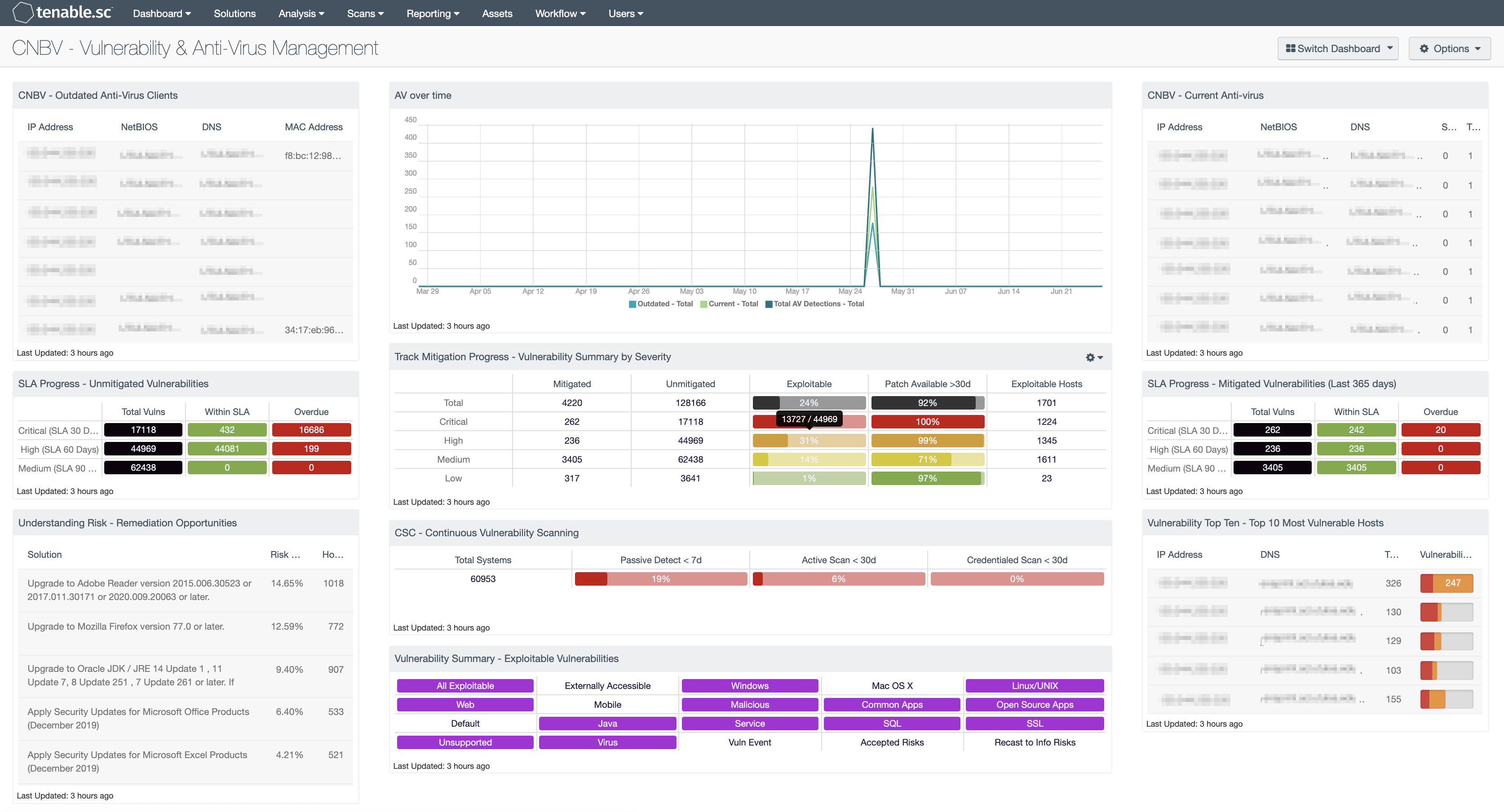
CNBV - Outdated Anti-Virus Clients: The Outdated Anti-Virus Clients table shows 10 hosts which have Outdated anti-virus detected. This component uses plugin ID 16193 filter and vulnerability text in order to parse through the plugin output.
CNBV - AV Over Time: The AV Over Time trend line shows the number of current, outdated, and total anti-virus that has been detected in the network. The numbers of outdated plus current anti-virus counts should add up to the total.
CNBV - Current Anti-Virus: The Current Anti-Virus table shows hosts which have had current anti-virus detected. This component uses plugin ID 16193 filter and vulnerability text in order to parse through the plugin output.
SLA Progress - Unmitigated Vulnerabilities: The matrix provides a summary of vulnerabilities based on the CVSS score and the SLA of 30, 60, 90 days. Each of the three rows are based on the CVSS severity from Medium to Critical. The three columns illustrate the count of vulnerabilities across all systems. To provide more focus to an asset group, the component can be installed with focus option set accordingly. The black cells are the count of vulnerabilities, with green meaning newly discovered and are within the prescribed SLA, while the red count are vulnerabilities that have been detected on the network for more than the allotted mitigation time.
Track Mitigation Progress - Vulnerability Summary by Severity: Tenable.sc records when vulnerabilities are discovered, when patches are issued, and when vulnerabilities are mitigated. This component assists in tracking vulnerability mitigations. In the matrix, the row with red is critical severity vulnerability information, the row with orange is high severity, the row with yellow is medium severity, and the row with green is low severity. The Mitigated column displays the number of vulnerabilities that have been moved to the mitigated database. A vulnerability is moved to the mitigated database when the vulnerability is no longer detected by a rescan; the vulnerability is assumed to be remediated.
SLA Progress - Mitigated Vulnerabilities (Last 365 days): The matrix provides a summary of the mitigated vulnerabilities discovered over the past 365 days. The rows depict the time required to mitigate (30, 60, 90 days) and the CVSS severity level. The three columns illustrate the count of vulnerabilities across all systems. To provide more focus to an asset group, the component can be installed with focus option set accordingly. The black cells are the count of vulnerabilities, with green meaning newly discovered and are within the prescribed SLA, while the red count are vulnerabilities that have been detected on the network for more than the allotted mitigation time.
Understanding Risk - Remediation Opportunities: This table displays the top remediations for the network. For each remediation, the risk reduction for the network if the remediation is implemented is shown, along with the number of hosts affected. The table is sorted so that the highest risk reduction is at the top. Implementing the remediations will decrease the overall vulnerability of the network. Adding filters to the component, such as filtering on only critical severity vulnerabilities or filtering on a specific asset group, can narrow the focus of the component, giving remediation opportunities in specific areas.
CSC - Continuous Vulnerability Scanning: This matrix assists in monitoring the vulnerability detection and scanning performed by the Tenable Nessus Network Monitor (NNM) and Tenable Nessus. Presented are the percentages of total systems that have had recent passive vulnerability detections, active vulnerability scans, and credentialed scans. This information highlights detection coverage and whether vulnerability scans are being regularly executed. The timeframes may be altered to fit organizational requirements.
Vulnerability Top Ten - Top 10 Most Vulnerable Hosts: This component shows the top ten hosts with exploitable vulnerabilities of high or critical severity. Editing the filters in the component and changing the tool from IP Summary to Class C Summary or Port Summary can give information on exploitable vulnerabilities per subnet or per port, respectively.
Vulnerability Summary - Exploitable Vulnerabilities: This matrix displays warning indicators for exploitable vulnerabilities actively and passively detected on the network, including vulnerabilities by OS, web vulnerabilities, application vulnerabilities, and vulnerabilities by keywords such as "Java" and "unsupported". Exploitable vulnerabilities that are externally accessible (i.e., accessible from hosts outside of the configured network address range) are very dangerous and must be remediated as soon as possible.