by Cesar Navas
July 14, 2020
The National Banking and Securities Commission (CNBV) Annex 72 is a collection of Key Risk Indicators (KRI) that establish compliance standards for financial institutions operating in Mexico. Financial institutions in Mexico should be prepared to divulge cyber risk KRIs to CNBV when requested. This dashboard relates to KRI0005 but continues to build on assisting a security operations teams in monitoring user privilege, access and user related compliance checks.
Financial institutions are naturally at a higher risk of being targeted and attacked. In an effort to minimize organizational risk tracking assets, (including vulnerabilities, misconfigurations, and other security health indicators) is vital to a successful risk management program. KRI0005 describes knowing about amount users and their assigned roles and permissions. Tenable.sc provides many mechanisms for understanding credential hygiene. The Local Check Plugins provide group membership, local user access, and user account information including information about inactivity and password change status. Local checks can also identify inactive and duplicate accounts on Linux and UNIX systems. Tenable.sc uses audit files to determine the state of logging on hosts and the associated risks. Separation of duties can be inferred by understanding the group memberships and other checks.
Administrative privileges should be controlled and limited specifically to those with a need, to limit the risk from account compromise. Each user of a system should have a unique account assigned to them. Sharing of user accounts limits accountability for actions. Administrator credentials should only be used to log on to workstations specifically designated for administrative work and all actions by the administrator should be logged. This limits the risk of account compromise via non-hardened workstations and ensures an appropriate audit trail exists in case of credential use by a bad actor. Following the principle of least privilege, users should only have the access specifically needed and no more. Similarly, user privileges should be separated by functional groups preventing fraud by ensuring that no individual has unnecessary authority to perform critical functions.
This Dashboard is available in the Tenable.sc feed, which is a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The Dashboard can be easily located in the Tenable.sc feed under the Executive category. The dashboard requirements are as follows:
- Tenable.sc 5.14.1
- Nessus 8.10.1
- Compliance Data
This dashboard provides the organization with a clear and simplified method to identify and establish compliance according to Annex 72 by CNBV. The data can be Analyzed to provide more detail in non-compliant areas, which facilitates the Fix and Measuring steps to the Cyber Exposure Lifecycle. Tenable.sc is the On-prem solution for understanding the picture of the network, while keeping the data under the organization’s control. Built on leading Nessus technology, Tenable.sc discovers unknown assets and vulnerabilities, and monitors unexpected network changes before they turn into breaches.
Components
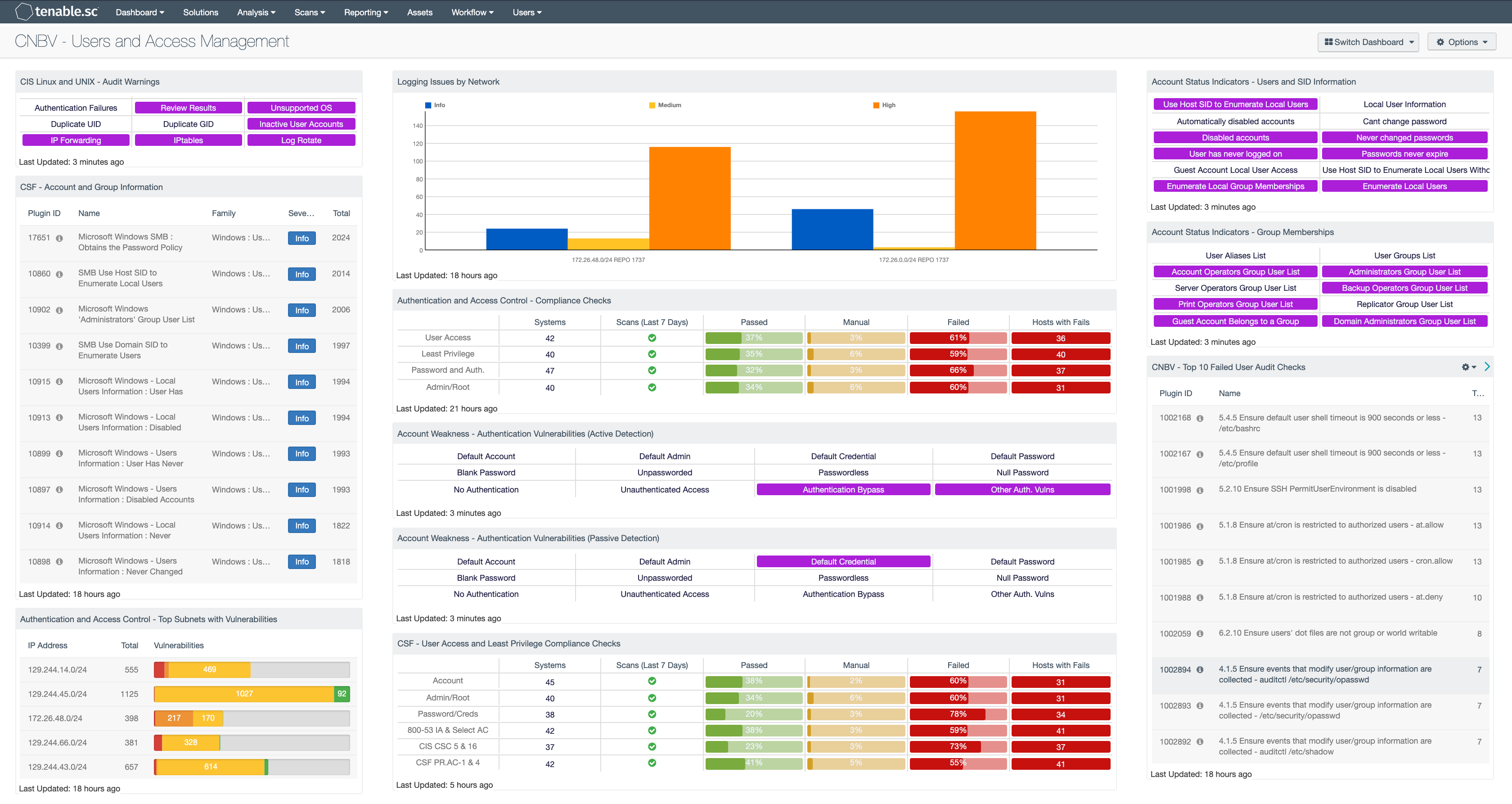
CIS Linux and UNIX - Audit Warnings: The Audit Warnings indicators trigger if one or more vulnerabilities are found to exist. Common checks included are: Duplicate UID/GID, Inactive User Account, and Unsupported OS. Indications can be customized to highlight specific CIS Linux and Unix vulnerabilities as the organization sees fit.
CSF - Account and Group Information: This table displays detections of account and group information, such as accounts that have never been logged into, disabled accounts, and group user lists. This information is obtained through Nessus credentialed scans. Most of these detections will contain lists of accounts in their output. The Obtains the Password Policy detection will contain the retrieved password policy in its output. Clicking on the Browse Component Data icon on the component will bring up the vulnerability analysis screen to display the detections and allow further investigation. In the analysis screen, setting the tool to Vulnerability Detail List will display the full details for each detection, including its description and output.
Authentication and Access Control - Top Subnets with Vulnerabilities: This component displays the top Class C subnets with actively and passively detected vulnerabilities related to authentication and access control. These vulnerabilities may include password vulnerabilities, default account and credential vulnerabilities, and other authentication-related vulnerabilities. Presenting these interactions by subnet allows easy understanding of which areas of the network are more vulnerable. Clicking on the Browse Component Data icon will bring up the vulnerability analysis screen to allow further investigation. If desired, the analysis tool can be changed to present the authentication and access control vulnerabilities by vulnerability, IP address, or asset list.
Logging Issues by Network: Logging Issues by Network shows a breakdown of logging issues by CIDR range. The Class C tool is used to group audit checks related to logging.
Authentication and Access Control - Compliance Checks: This component displays compliance information in the areas of user access, least privilege, password and authentication requirements, and administrative/root account control. The displayed compliance information is either based on keywords, or is related to relevant areas in security standards such as NIST SP 800-53, the CIS Critical Security Controls, the Cybersecurity Framework, and ISO/IEC 27001. For each row, the columns provide the number of hosts audited, whether an audit scan was run in the last seven days, the ratios of passed audit checks (in green), checks that require manual verification (in orange), and failed audit checks (in red), and the count of hosts with failed checks. Clicking on a highlighted indicator in the Hosts with Fails column will bring up the vulnerability analysis screen to display the systems with failed audit checks and allow further investigation. Note that in order for data to appear in this component, appropriate audit/compliance scans must first be run on the network.
Account Weakness - Authentication Vulnerabilities (Active Detection): This matrix shows active detections of authentication vulnerabilities. Each indicator highlights those vulnerabilities with the given keyword(s) in their name.
Account Weakness - Authentication Vulnerabilities (Passive Detection): This matrix shows passive detections of authentication vulnerabilities. Each indicator highlights those vulnerabilities with the given keyword(s) in their name.
CSF - User Access and Least Privilege Compliance Checks: This component displays user access and least privilege compliance information in areas such as password requirements, lockout policy after failed logins, and controlled use of administrative privileges. The first rows display compliance information by keyword. The last rows display user access and least privilege compliance information related to several standards: NIST 800-53 (IA family and selected AC controls), CIS Critical Security Controls (v6.0, CSC 5 and 16), and the Cybersecurity Framework (PR.AC-1 and PR.AC-4). For each row, the columns provide the number of hosts audited, whether an audit scan was run in the last seven days, the ratios of passed audit checks (in green), checks that require manual verification (in orange), and failed audit checks (in red), and the count of hosts with failed checks. Clicking on a highlighted indicator in the Hosts with Fails column will bring up the vulnerability analysis screen to display the systems with failed audit checks and allow further investigation. Note that in order for data to appear in this component, appropriate audit/compliance scans must first be run on the network.
Account Status Indicators - Users and SID Information: This component provides easy access to several plugins used to collect information about user accounts and security identifiers (SID). Listed below are the details for plugins identified in this matrix:
Account Status Indicators - Group Memberships: There are several default groups such as the administrators, server operators, account operators, backup operators, print operators, and replicator; this matrix provides an easy method to monitor these memberships.
CNBV - Top 10 Failed User Audit Checks: Logging Top 10 shows the Top 10 logging issues. Audit checks are filtered for those related to logging issues and displayed.