by Cesar Navas
May 6, 2016
Traditional anti-virus clients solutions are a fundamental part of protecting the enterprise against malware and other malicious threats. As attacks against organizations continue to increase, attackers are creating malware that can evade anti-virus scanners and remain undetected for long periods of time. This dashboard can assist organizations in monitoring the status of anti-virus clients, which can help to ensure that all clients remain connected and up-to-date.
Many organizations frequently use managed anti-virus solutions to assist with remotely administering scans and pushing updates out to clients. However, issues with anti-virus clients can be the result of misconfigured policies or loss of communication between the client and anti-virus server. Although managed anti-virus solutions can provide greater visibility and control over clients, many organizations do not apply additional controls needed to protect systems from potential attacks.
Information presented within this dashboard will allow organizations to quickly identify and remediate issues from AV solutions. Nessus utilizes several WMI-based checks to determine if anti-virus, anti-spyware, and desktop firewalls are installed and have been updated to the latest release on Windows systems. The Log Correlation Engine (LCE) monitors activity from anti-virus clients, which can alert analysts to potential malware infections or other malicious activity. Several components include event activity from many leading anti-virus vendors including Symantec, McAfee, Sophos, and Trend Micro. Nessus also uses a variety of audit files to check systems for malware protection controls. This information can indicate potential misconfigurations or other security controls that need to be modified. Controls referenced within this dashboard include the following:
Compliance Regulations
- Cybersecurity Framework DE.CM-4 (Malicious code is detected)
- NIST 800-53 control SI-3 (Malicious Code Protection)
- SANS/Council on CyberSecurity Critical Security Control 5 (Malware Defenses)
- PCI DSS requirement 5 (Protect all systems against malware and regularly update anti-virus software or programs)
- ISO/IEC 27002 12.2 (Controls against malware)
- COBIT5 DSS05.01 (Protect against malware)
- HIPAA 164.308(a)(5)(ii)(B) (Protection from malicious software)
Analysts should review current security policies and compliance requirements that are relevant to the organization. By continuously monitoring anti-virus solutions, organizations will be able to reduce their attack surface, and strengthen their defenses against advanced malware.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Discovery & Detection. The dashboard requirements are:
- Tenable.sc 5.3.1
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.0
- complianceData
- localChecks
Tenable.sc Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. Tenable.sc is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. Nessus Network Monitor (NNM) provides deep packet inspection to continuously discover DNS vulnerabilities traveling the wire. LCE correlates real-time events, and has the capability to discover users, operating systems, network devices, hypervisors, databases, tablets, phones, web servers, and other critical infrastructure. Tenable.sc CV allows for the most comprehensive and integrated view of network health.
The following components are included in this dashboard:
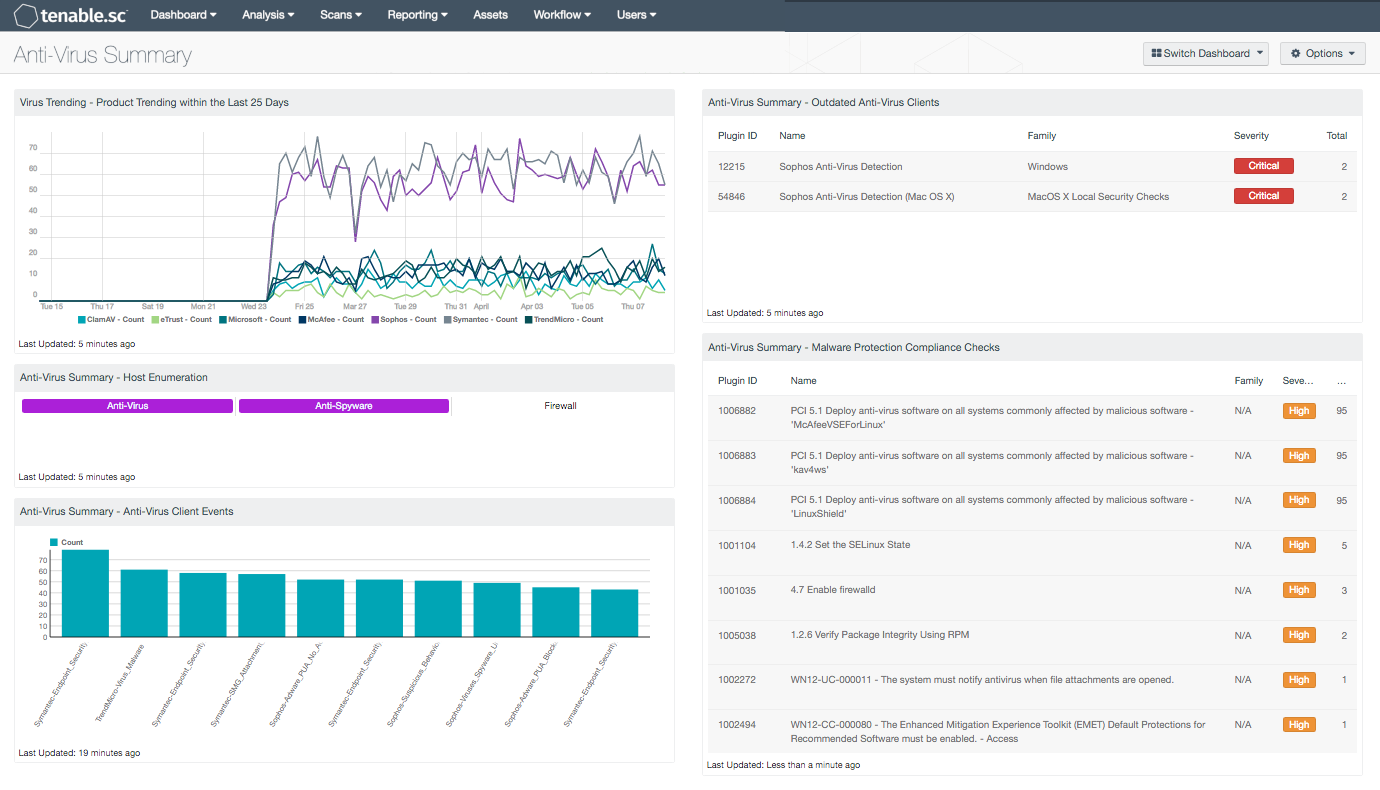
- Virus Trending – Product Trending within the Last 25 Days: This component displays trending of virus detections for various antivirus products within the last 25 days. Displayed are 7 of the most popular antivirus products in use by organizations today. This component can be modified to track any antivirus product that is used by an organization in their environment.
- Anti-Virus Summary – Host Enumeration: The Host Enumeration component uses the plugin IDs 16193 (Anti-Virus Enumeration), 45050 (Anti-Malware Enumeration), and 45052 (Firewall Enumeration) to report on the status of anti-virus, anti-malware, and desktop firewalls. Plugin ID 16193 will detect Windows and Mac OS X hosts with anti-virus installed, and virus definitions are up-to-date. Plugin IDs 45050 and 45052 utilize the Windows Management Instrumentation (WMI) to check for anti-spyware and desktop firewall software installed on Windows-based systems. Clicking on a highlighted indicator will bring up the analysis screen and display details on the detections and events.
- Anti-Virus Summary – Anti-Virus Client Events: The Anti-Virus Client Events component presents a chart of the top anti-virus client events within the last 72 hours. This chart displays the top 10 events from many leading anti-virus vendors such as Symantec, McAfee, Sophos, Trend Micro, and ClamAV. Events are normalized by LCE and filtered on the event type “virus,” which monitors anti-virus client events from the respective vendor. These events can alert organizations to potentially suspicious behavior, malware infections, spyware removal, quarantined events, and more. Organizations can use this component to quickly identify and remediate malware from anti-virus clients.
- Anti-Virus Summary – Outdated Anti-Virus Clients: The Outdated Anti-Virus Clients component can assist organizations in monitoring the network for outdated anti-virus clients. Information provided within this component may indicate systems with anti-virus clients that are offline, disconnected, or out-of-date. Analysts can use the information provided to ensure that all anti-virus clients remain connected and up-to-date.
- Anti-Virus Summary – Malware Protection Compliance Checks: The Malware Protection Compliance Checks component provides a summary of malware protection compliance checks. Nessus uses a variety of audit files to check systems for malware protection controls. High severity denotes checks that have failed to meet the compliance threshold. Medium severity shows checks that need to be manually reviewed to assess their compliance state. Informational severity status is used for checks that have passed the compliance requirement. Organizations should review current security policies and compliance requirements that are relevant to the organization. Each compliance check includes detailed information on the respective vulnerability that the analyst can immediately drill down into. This table can be modified to include additional or specific compliance checks based on organizational requirements.