by Cesar Navas
October 10, 2016
Many organizations struggle to implement and maintain an effective asset management program. Relying on manual processes to track assets can be ineffective and place the organization at risk for data theft, non-compliance penalties, and additional threats. Unauthorized software on the network can open up vulnerabilities that allow attackers to gain full control over critical systems. Accounts with too many privileges can lead to unauthorized accesses and network pivoting activities. These issues can expose critical systems and data to compromise, potentially leading to devastating consequences and even jeopardizing an organization's competitiveness and long-term survival.
The French Network and Information Security Agency (Agence nationale de sécurité des systèmes d’information or ANSSI) developed the "40 Essential Measures for a Healthy Network" to assist organizations in safeguarding the security of information systems within a network. Following these measures, or rules, for a healthy network will provide basic protection for an organization's critical data. ANSSI states that the majority of IT attacks that have involved ANSSI stepping in could have been prevented had the IT measures set out in the guide been applied.
This dashboard aligns with Section I of the ANSSI 40 Essential Measures for a Healthy Network: Know the Information System and Its Users. This section contains three rules:
- Rule 1 focuses on keeping an accurate and up-to-date inventory of network assets. Large organizations today may have hundreds of thousands of devices, software, and users deployed across multiple locations. Without comprehensive asset management in place, administrators can easily lose track of devices and software in use. Monitoring portable devices such as mobile phones, tablets, and laptops can also be challenging as these devices can be easily lost or stolen.
- Rule 2 addresses identifying and monitoring privileged accounts. Administrative users have unrestricted access to internal systems. Tracking these administrative users and detecting any users who may have too many privileges is essential for ensuring the security of network assets and data.
- Rule 3 emphasizes the importance of managing new and existing user rights appropriately as employees arrive at, move within, or leave an organization. As employees change roles within an organization, some employees may retain former privileges that are excessive. Employees may also retain excessive rights after being granted temporary access to sensitive or confidential data.
This dashboard will enable organizations to more effectively manage assets, software, and accounts. Using this dashboard, an organization will be able to obtain comprehensive information about assets, software installations, privileged user groups, and changes on the network. This information will assist the organization in better knowing and managing network inventory, identifying and monitoring privileged accounts, managing user rights, and ultimately safeguarding critical assets and data.
Components on this dashboard provide counts of systems (including mobile devices), and lists of installed software, operating systems, and unsupported products. Information on currently installed software and operating systems can assist analysts in managing software assets and licenses throughout the organization. Information on new systems and software changes can be useful in maintaining inventory and detecting unauthorized changes. Data on user changes can highlight new users, permission changes, and first time user logins, which can aid in managing users and enforcing least privilege. Tracking members of administrative groups can help ensure authorized access and security of critical systems and data. Analysts can easily drill down into the data presented on this dashboard to gain more detailed information.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.3.2
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.1
Tenable's Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring solution, and can assist an organization in knowing and managing the network. Active scanning periodically examines devices to determine vulnerabilities and compliance concerns. Agent scanning enables detection and scanning of transient devices. Passive listening collects data to continuously detect devices and monitor network activity. Host data and data from other security investments is analyzed to monitor activity and identify new devices, software, and users. Tenable.sc CV provides an organization with the most comprehensive view of the network, and the intelligence needed to manage devices and users in order to safeguard critical assets and information.
This dashboard contains the following components:
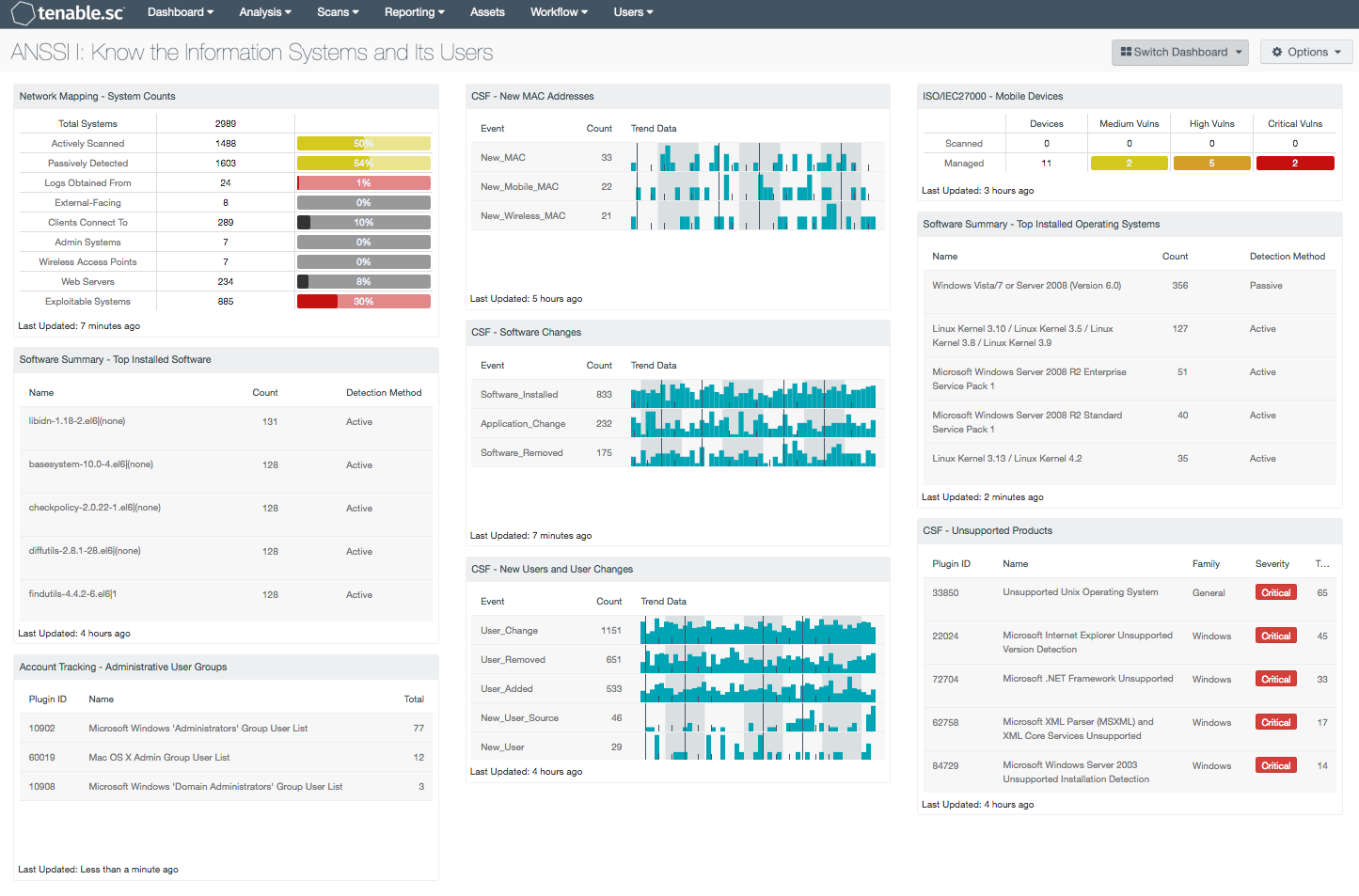
- Network Mapping - System Counts: This component presents the counts of systems detected on the network in various categories. The total number of systems is displayed, along with the counts of actively scanned systems detected by Nessus, passively detected systems discovered by NNM, and systems from which LCE obtained logs. For these, percentages of the total system count are displayed. The percentage bar color reflects coverage and will be red for a low percentage of total systems, yellow for a medium percentage, and green for a high percentage. In addition, counts of external-facing systems, systems that clients connect to (servers), admin systems, wireless access points, and web servers are also displayed. For each of these, percentages of the total system count are displayed with black bars. Finally, the count of exploitable systems on the network is displayed, along with a percentage bar displayed in red. Using this matrix, organizations will be able to gain a more complete picture of existing assets and high-valued systems on the network.
- Software Summary - Top Installed Software: This table displays a list of the software currently discovered on the network. The table is sorted so the most commonly detected software is at the top. Any unexpected software should be investigated to make sure it is authorized. Clicking on the Browse Component Data icon will bring up the vulnerability analysis screen to display details and allow further investigation. It may also be useful to reverse the sort order to investigate software that appears least often, as this may better indicate deviations from a baseline.
- Account Tracking - Administrative User Groups: Administrative users typically have unrestricted access to internal systems; tracking administrative users and groups is essential for ensuring the security of network assets and data. This component presents administrative groups that have been detected on the network. This information is obtained through Nessus credentialed scans. These detections will contain lists of administrative accounts in their output. Security teams can use this detailed information to both track administrative users and detect any users who may have excessive privileges.
- CSF - New MAC Addresses: This table detects new MAC addresses from workstations, servers, mobile, and wireless devices that were first observed in the last 72 hours. LCE utilizes the ‘New_MAC’, ‘New_Wireless_MAC’, and ‘New_Mobile_MAC’ normalized events when a new, never-before-seen MAC address is observed on the network. Each event displays the time observed, IP address, MAC address, and the raw syslog text. Discovering new hosts on the network can assist an organization in maintaining an accurate inventory and detecting rogue devices.
- CSF - Software Changes: This table presents event trend data on Software Installations and Changes over the past 72 hours. The “Software_Installed” normalized event displays event activity on software installations. The “Software_Removed” event detects software that has been removed or uninstalled across multiple operating systems. The “Application_Change” event presents details on changes such as anti-virus signature updates, firewall changes, and Tenable.sc CV events detected by the Log Correlation Engine (LCE). The analyst can drill down into the syslog events to obtain additional information about each normalized event.
- CSF - New Users and User Changes: This component presents data on new and existing user events on the network over the past 72 hours. The LCE normalized events of ‘User_Added’, ‘User_Change’, ‘User_Removed’ and ‘New_User’ are displayed within this table. These detected event changes will display information on new user accounts, user account password changes, rights access, and new user logins seen for the first time. The data within this component will be highly valuable to any analyst in determining the presence of unauthorized accounts on the network.
- ISO/IEC27000 - Mobile Devices: This component presents both scanned and managed mobile devices on a network. Scanned mobile devices are detected using NNM, and include mobile devices that are not managed by an MDM Server. The data displays the number of detected scanned and managed mobile devices, along with associated vulnerabilities by severity level. If no indication is present for the specified severity or count, zero is shown. The analyst may click on the indicator to retrieve further details on specific mobile devices.
- Software Summary - Top Installed Operating Systems: This component presents a list of the operating systems present on the network, as identified through active scans and passive detections. Analyst can use this information to track operating systems in use, for licensing requirements as well as checking for any outdated or unauthorized operating systems.
- CSF - Unsupported Products: This table displays all unsupported products by name, sorted by severity. Displayed is the plugin ID, product name, plugin family, severity, and the total found. This component identifies unsupported products by filtering on the text "unsupported" in the vulnerability plugin name. Products and applications that are no longer supported can be serious security risks, as any vulnerabilities will no longer be patched by the vendor.