by Cody Dumont
May 2, 2016
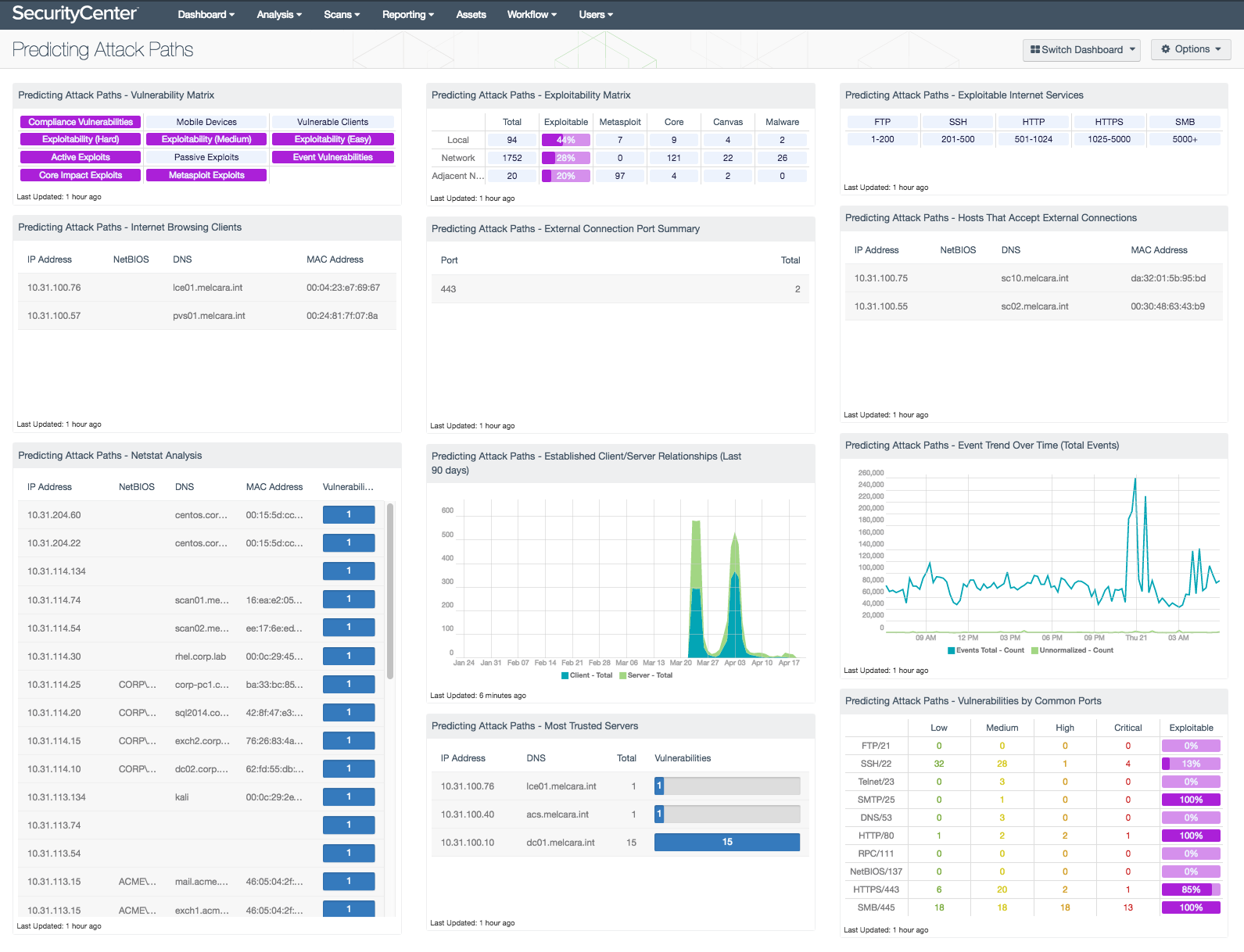
Adversaries are always looking for new methods to attack an organization’s network. These new attack methods can be identified when looking at all the possible attack paths. This dashboard provides a look into many of the attack methods SecurityCenter Continuous View (CV) can be used to identify new attack paths.
Many of the components in this dashboard are provided to assist the analyst in identifying systems on the network that can be exploited in a variety of different ways. The methods of detecting vulnerabilities include active, passive, and events. This data can be leveraged to rapidly identify vulnerabilities that are subject to attack and exploitation. This dashboard was created in support of the Tenable whitepaper titled “Predicting Attack Paths”.
SecurityCenter CV provides an organization with a proactive method to validate third-party tools such as Windows Server Update Services (WSUS) for installed software updates or other settings. SecurityCenter CV can also help with discovering cyber intrusions, allowing the organization to correlate vulnerabilities, configuration audits, and event logs in a single solution. As organizations gain more familiarity with continuous network monitoring, they will be better able to analyze detailed information about predicting attack paths.
When searching for attack paths in the network, the analyst should begin by using Passive Vulnerability Scanner (PVS) to detect the trusted connections between hosts and servers, and also identify systems that are accessible from External sources. By first identifying the communication paths, the analyst can then begin to identify the possible attack vectors. When PVS encounters traffic originating from outside the network, a string “External Access” is added in the vulnerability output. Using the “Systems Accessible from External IP Addresses” asset, the analysts can look for other vulnerabilities or events, and then gain a better understanding of the attack paths.
The dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Threat Detection & Vulnerability Assessments. The dashboard requirements are:
- SecurityCenter 5.2.0
- Nessus 6.5.6
- LCE 4.8.0
- PVS 5.0.0
SecurityCenter CV’s ability to continuously monitor the network to identify vulnerabilities, reduce risk, and ensure compliance differentiates Tenable from the competition and provides organizations with the ability to be proactive while implementing the Strategies to Mitigate Targeted Cyber Intrusions. The ability of Nessus, Log Correlation Engine (LCE), and PVS to detect vulnerabilities on the network is unmatched in the industry. Nessus actively scans the network for vulnerabilities and compliance issues, while PVS passively monitors network traffic. LCE monitors logs and PVS events to detect vulnerabilities, while also using NetFlow and syslog events to correlate threats and provide alerts to security professionals.
Components
Predicting Attack Paths - Vulnerability Matrix: This matrix provides indicators that identify exploitable or questionably secure client software, including passive exploitable clients, exploitable mobile devices, passive vulnerable clients, unsupported software, and exploitable client software with an AC:H and AC:M. The access complexity (AC) metric describes how easy or difficult it is to exploit the discovered vulnerability. H is for High, and M for Medium exploits. This is independent of severity of the plugin. For example, a medium severity may be listed in with AC:H (High), because it is easier to exploit. This component also has indications for known active and passively detected exploits, event and compliance vulnerabilities, and vulnerabilities that are exploitable by Metasploit and Core Impact.
Predicting Attack Paths - Internet Browsing Clients: PVS plugin #16 specifically tracks which systems connects to the Internet and on which ports. The concept of “outbound browsing” may be unusual as Analysts typically think about ports as opened for listening by the server for a specific application, but not something that is tracked as a specific client-side property. However, when tracked as a unique system property, it becomes very easy to classify hosts based on their client-side port usage. To produce lists of internal systems that connect to the Internet, a dynamic or static asset list can be created by listing all of the IP addresses that matched PVS plugin #16. To produce a more detailed list of internal systems that connected to the Internet on specific ports, consider adding port filters for common ports such as 21, 22, 25, 80, 443, 465, and so on.
Predicting Attack Paths - Exploitability Matrix: This component filters on using the CVSS Exploitability Metric Vectors. The matrix uses the Attack Vector (AV) matrix, and provides a cell for each exploitability framework. The CVSS metric will help illustrate if the vulnerability is a local or remote vulnerability.
Predicting Attack Paths - External Connection Port Summary: This component uses information from plugin ID 14, “Accepts external connections”, and the Port Summary tool to present a table that is sorted by the most commonly observed active ports.
Predicting Attack Paths - Established Client/Server Relationships (Last 90 days): This trend component graphs data on internal client trusted client and server connections over a 90-day period. These connections are considered "trusted" as they have occurred between hosts within the monitored network range. Plugin ID 3, “Internal client trusted connection”, is used by PVS to identify internal servers that workstations have connected to on a particular port. Plugin ID 15, “Internal server trusted connection”, is used by PVS to identify internal clients that have connected to servers on a particular server port. Plugin IDs 3 and 15 are the opposite of each other when reporting on trusted connections.
Predicting Attack Paths - Most Trusted Servers: This component leverages plugin ID 15, “Internet server trusted connection”, to present data on clients who have connected to a given server, and what port the connection has taken place on.
Predicting Attack Paths - Exploitable Internet Services: This component takes many of the various detection technologies for botnets, malicious file hashes, anomalous network traffic, spikes in system logs and continuous scanning activity and places them into one spot.
Predicting Attack Paths - Hosts That Accept External Connections: When PVS is deployed in a manner to monitor external network traffic, PVS has the ability to readily identify any system and service that is in use. This component utilizes data from plugin ID 14, “Accepts external connections”. UDP and TCP services are both detected and the table presents data via the IP Summary tool with columns for the host IP address, NetBIOS, MAC address, and DNS Name.
Predicting Attack Paths - Event Trend Over Time (Total Events): This line chart component displays information on event trends over time. Displayed is a line chart comparison over the last 24 hours of total normalized events versus unnormalized events. This provides the analyst with a quick overview of any current event spike activity.
Predicting Attack Paths - Vulnerabilities by Common Ports: This component contains six columns that enumerate the number of hosts with vulnerabilities on a specific port. The columns provide a count of vulnerable hosts based on a specific ports and severity level. The last column provides a percentage of hosts with an exploitable vulnerability on that port. The colors used in this matrix have a transparent background and change the color based on the severity level. The color green represents low severities, yellow is for medium severity, high severity vulnerabilities are orange, and critical severities are red. The last column in purple shows exploitability but makes no reference to severity level.