by Megan Daudelin
August 12, 2016
Many organizations do not have adequate incident response plans to deal with compromised machines and network devices. Once a host has been compromised, malware can remain on the system for weeks or more, harvesting credentials, stealing data, and causing significant and widespread damage. Without adequate detection and reporting capabilities, organizations will not have a clear picture of the extent of an infection or compromise. Analysts could miss critical information on attack vectors that were used and the points of entry into the network. Inadequate data backups can also hamper recovery efforts as business critical information may be corrupted or lost completely. Organizations need to have a comprehensive business continuity or disaster recovery plan in place to recover and restore business operations in the event of a natural disaster or network incident. Without these plans, an incident or compromise may jeopardize an organization's competitiveness and long-term survival.
In order to perform effective incident response procedures, extensive information about the network and about specific hosts impacted by the incident must be readily available. Attempting to gather detailed information from affected systems after an incident has occurred wastes precious time and resources that should be spent responding to and recovering from the effects of the incident. Integrating incident response preparation measures into regular scanning and monitoring procedures is the most effective way to prepare for and detect an incident. Many types of incidents require a swift response in order to minimize their impact, including intrusions and malware infections. If allowed to proliferate, malicious activities can spread through a network and impact critical systems and data. Tenable SecurityCenter Continuous View (CV) leverages multiple data sources in order to provide comprehensive incident response support. Active scanning by Tenable Nessus gathers detailed information about hosts and network devices, while passive listening by the Tenable Passive Vulnerability Scanner (PVS) sniffs network traffic to detect activity and connections that could be a cause for concern. The Tenable Log Correlation Engine (LCE) synthesizes data from other security devices to provide event correlation in support of early detection and incident response efforts.
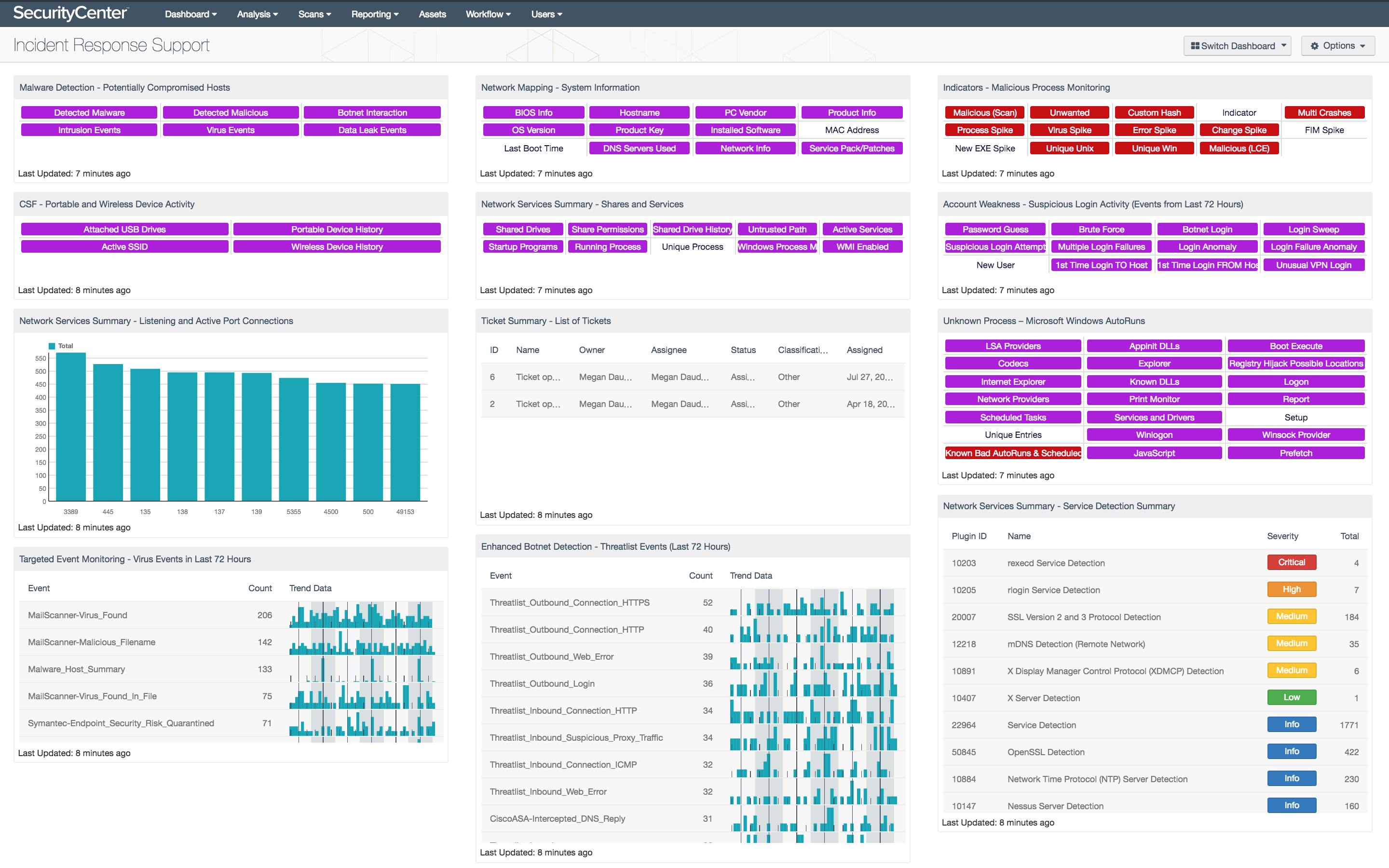
The Incident Response Support dashboard provides access to extensive details about hosts on the network in order to effectively prepare security teams in case of an incident. System information about listening port connections is presented to help support incident response planning and identify post-exploitation activity. Security teams can use the data presented to monitor the network for wireless and portable devices that have been connected to the network. Service detection on internal hosts will provide valuable information on any unauthorized or insecure services in use that could be exploited by attackers. Indicators provide a comprehensive look at system information, configurations, shared drives, startup programs, and active processes on internal hosts. This information can be useful in determining an initial point of entry used by an attacker, malicious processes that may be running, data that an attacker could have access to, and other systems that may have been compromised. The components in this dashboard provide security teams with exhaustive details about hosts on the network in order to most effectively respond to incidents.
Virus events from the past three days are also presented, providing insight into potential malware infections. Additional indicators are displayed that will alert analysts to potentially compromised hosts based on detected malware, malicious processes, or suspicious behavior. Events related to hosts communicating with known botnet IP addresses are listed for the past 72 hours to alert security teams to potentially infected, misused, or misconfigured machines. A ticket activity summary is included that leverages SecurityCenter CV’s integrated ticketing system, which can be used to track incident response activities. Indicators about AutoRun and startup services will alert security teams to processes, registry keys, startup programs, and scheduled tasks that could potentially execute malicious programs on hosts. Information about unusual, suspicious, or never-before-seen login activity highlights potential sources of unauthorized access attempts. This information can be useful for security teams to understand current weaknesses and how to fix them, detect compromised hosts, and track incident response activity. Organizations will be able to use the extensive information presented by components in this dashboard to strengthen security controls, reduce the attack surface, and improve overall incident response procedures.
Without any additional filters, this dashboard provides an overview of the incident response support information available for the entire network. When an incident occurs, the dashboard can be easily modified to focus on specific hosts, assets, or repositories. When the dashboard is added from the SecurityCenter Feed, analysts can set the Targets filter in the Focus section so that specific targets will be added automatically as filters to all of the included components. Setting this filter will allow security teams to more efficiently gather information about specific targets when responding to incidents on the network.
This dashboard is available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Monitoring. The dashboard requirements are:
- SecurityCenter 5.3.2
- Nessus 6.7.0
- LCE 4.8.0
- PVS 5.1.0
Tenable SecurityCenter Continuous View (CV) is the market-defining continuous network monitoring solution, and can assist in securing an organization’s internal network and effectively responding to incidents. SecurityCenter CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new regulatory compliance data. Active scanning periodically examines systems to determine vulnerabilities and compliance concerns. Agent scanning enables scanning and detection of vulnerabilities on transient and isolated devices. Passive listening provides real-time discovery of vulnerabilities on operating systems, protocols, network services, wireless devices, web applications, and critical infrastructure. Host data and data from other security products is analyzed to monitor the network for malware, intrusions, and other forms of malicious activity. SecurityCenter CV provides an organization with the most comprehensive view of the network and the intelligence needed to support proactive incident response efforts.
The following components are included in this dashboard:
- Malware Detection - Potentially Compromised Hosts: This component presents indicators that highlight potentially compromised hosts. The top row of indicators highlight those hosts that have a high probability of being compromised, including hosts with detected malware infections, hosts with detected malicious activity, and hosts interacting with known bad IP addresses. The second row of indicators highlight hosts with suspicious activity that may indicate a compromise, including those hosts with intrusion events, virus events, and data leakage events. If an event or activity has been detected on a host, the indicator will turn purple. Analysts can drill down and obtain information on the hosts involved, event activity, and potential remediation solutions.
- CSF - Portable and Wireless Device Activity: This component presents indicators that will report on Active SSIDs, attached USB drives, and history of previously detected portable and wireless devices. This information can not only alert to attached USB or portable drives, but other devices that use USB connections such as printers may also be presented. Hosts with active SSIDs include information reported by wireless network card on a host, and associated SSID that the host connected to. Both wireless and port device history will provide insight on wireless networks that a host has connected to, and any previously connected USB-based devices. Security teams can use the information detect and prevent any unauthorized USB or rogue wireless access devices that may be present on the network.
- Network Services Summary - Listening and Active Port Connections: This bar chart presents the top 10 ports detected on hosts that are listening or have active port connections. Nessus provides several plugins that leverage the “Netstat” command to determine all listening and enabled connections on hosts. This component can be modified to include specific port connections per organizational requirements. Analysts can browse the component data to obtain additional information on hosts, services, and port activity.
- Targeted Event Monitoring - Virus Events in Last 72 Hours: The Virus Events in Last 72 Hours table lists the virus events by count detected in the last three days. Events are normalized by LCE and filtered on the event type “virus,” which can include logs that indicate the presence of a virus in email, a virus found on a system by antivirus software, or virus logs found by network IDS events and firewalls. This component alerts analysts to possible malware infections seen in the past three days to enable quick remediation. Directing focus toward the most recent and prolific infections helps reduce the time between discovery and containment.
- Network Mapping - System Information: This component presents indicators that will report on system details, network configurations, and installed software detected on network hosts. This data can provide analysts will valuable information to support asset management, incident response, and forensic investigation efforts. Data provided within this component can be used to correlate malicious events and other suspicious activity. The indicator turns purple when active scans successfully gather data from internal hosts. This component can help to ensure that analysts have accurate and up-to-date information about hosts on the network.
- Network Services Summary - Shares and Services: This component presents indicators that highlight the types of services and shared storage in use on the network. This information provides an overview of system information, configurations, shared drives, startup programs, and active processes on internal hosts. Clicking on a highlighted indicator will provide comprehensive information about the presence of each specific service on the network.
- Ticket Summary - List of Tickets: This table presents a status summary of tickets issued within the SecurityCenter Ticketing and Alert System. Tickets are a means by which tasks are assigned to users to perform important actions such as vulnerability remediation or incident response. Tickets can be created manually or automatically by a predefined set of conditions through the alerting functionality. Integration with any existing third-party ticketing systems is also supported, typically via email notification. This component displays the number of tickets in each ticket status.
- Enhanced Botnet Detection - Threatlist Events (Last 72 Hours): The Threatlist Events (Last 72 Hours) table provides a normalized event summary of the threatlist events detected in the past 72 hours by count. The component is filtered by the LCE event type “threatlist” and lists the count and trend of each normalized event. Security analysts can use this table to monitor threatlist events detected in the network.
- Indicators - Malicious Process Monitoring: This component takes many of the various detection technologies for botnets, malicious file hashes, anomalous network traffic, spikes in system logs and continuous scanning activity and places them into one spot. This component is included in dashboards related to the 2015 Verizon Data Breach Investigation Report (DBIR).
- Account Weakness - Suspicious Login Activity (Events from Last 72 Hours): This matrix shows potentially suspicious login activity. This activity can bring attention to accounts that are more threatened and require greater protection.
- Unknown Process – Microsoft Windows AutoRuns: This component presents 21 indicators that will alert on a variety of Windows AutoRun and startup service issues detected on the network. Corrupted or unauthorized startup services can be an indication of compromise. Windows Prefetch data can be useful information during a forensics investigation to allow an analysis of software usage on a host. AutoRun is a feature is found on Windows systems that will allow mounted portable devices such as USBs, CDs, and DVDs to launch programs automatically without user intervention. Disabling AutoRun is best practice as leaving this feature enabled can allow for malware and other malicious programs to infiltrate the network. Indicators will turn purple when a system has detected activity on a host.
- Network Services Summary - Service Detection Summary: This component presents a list of services detected on internal network hosts. Services presented within this table can include network protocols, databases, servers, remote desktop services, and more. Some of this information can also include insecure protocols such as FTP, Telnet, and SSL protocols. The table is sorted by severity which will allow for quick detection and remediation of insecure protocols by analysts. Analysts can modify the table to report on specific information per organizational requirements.