Are Your Containers At Risk?

Containers have transformed the way organizations are deploying applications and services within their environments. While containers are lightweight and more efficient alternatives to virtual machines, they usually exist for a short period of time. Rapid changes in agile environments can create significant risks for security teams using traditional vulnerability management solutions. Tenable.io™ Container Security provides you with an in-depth vulnerability assessment of container images, enabling you to evaluate the security of your containers before they are deployed.
Containers and DevOps
Containers provide DevOps teams with an easy way to build and deploy applications into a production environment. Images are often pulled directly from public repositories that contain stripped down versions of base operating systems and web applications and services. Just like traditional applications and services, containers may be outdated and hold vulnerabilities that can leave your systems at risk.
Container and security teams
For security teams, attempting to assess the security of containers can present a host of challenges when the containers are deployed as needed or hidden behind the Docker virtual networks. Containers take advantage of the Linux OS kernel by sharing host OS resources, enabling for quick delivery of applications that can be easily deployed, used, or removed within a short amount of time. Active scanning using credentials is often ineffective, as containers typically don’t include the SSH daemon to log in and scan the container. Some containers may have isolated applications and services that are not exposed publicly, making it difficult for security teams to assess an organization's overall risk profile.
Tenable.io Container Security
Using Tenable.io Container Security provides you with the visibility needed to see what’s going on inside your containers. Having accurate information enables developers to pinpoint and remediate container risks in a timely manner.
Getting started with Tenable.io Container Security is so easy that we are offering a free 60-day test drive.
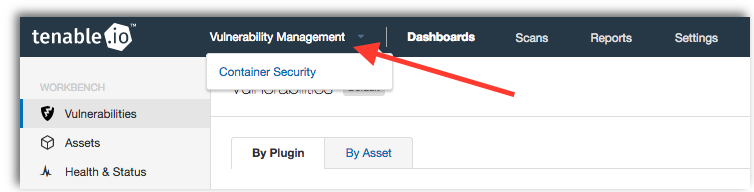
Existing Tenable.io customers can activate their trial by logging into Tenable.io, and selecting Container Security from the Vulnerability Management toolbar.
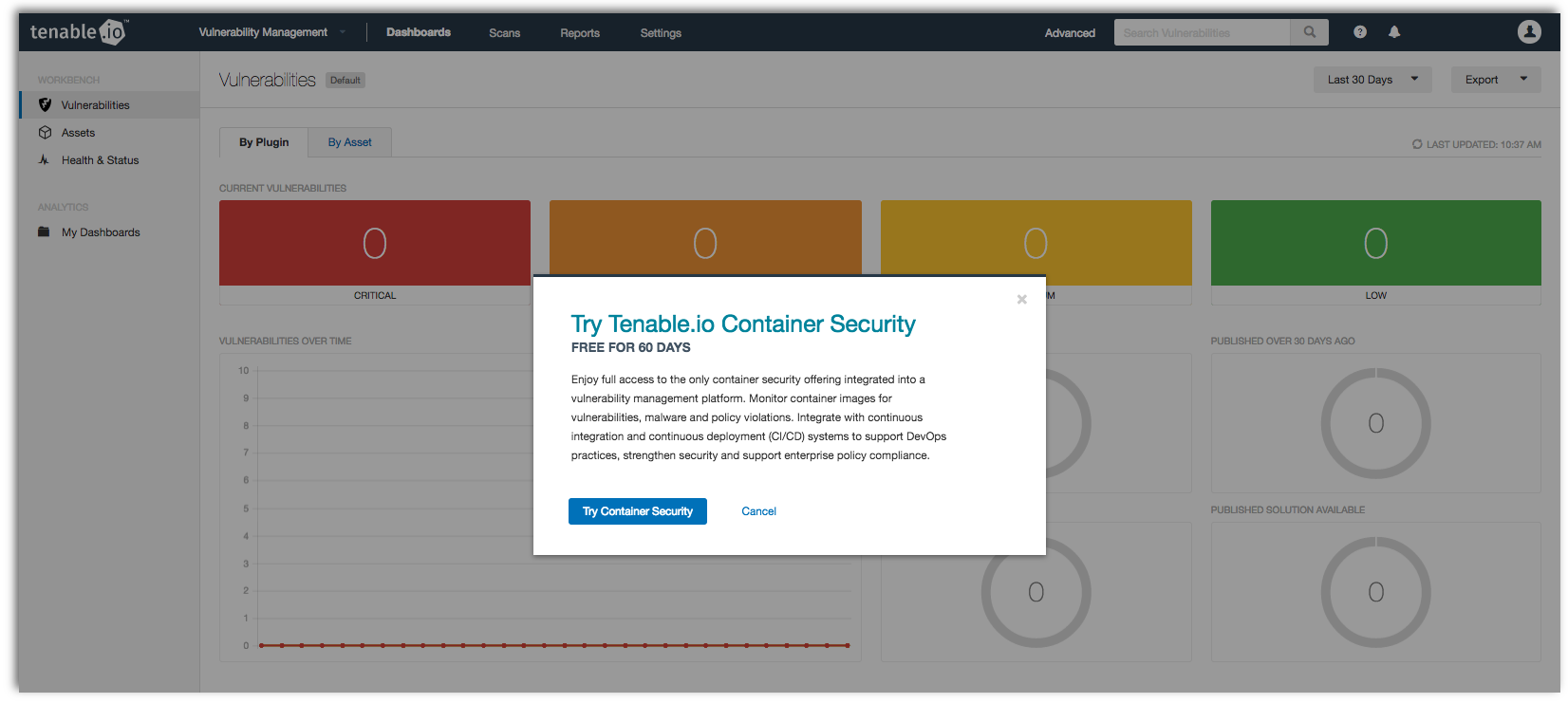
Within the splash screen, click on Try Container Security to enable your 60-day free trial.
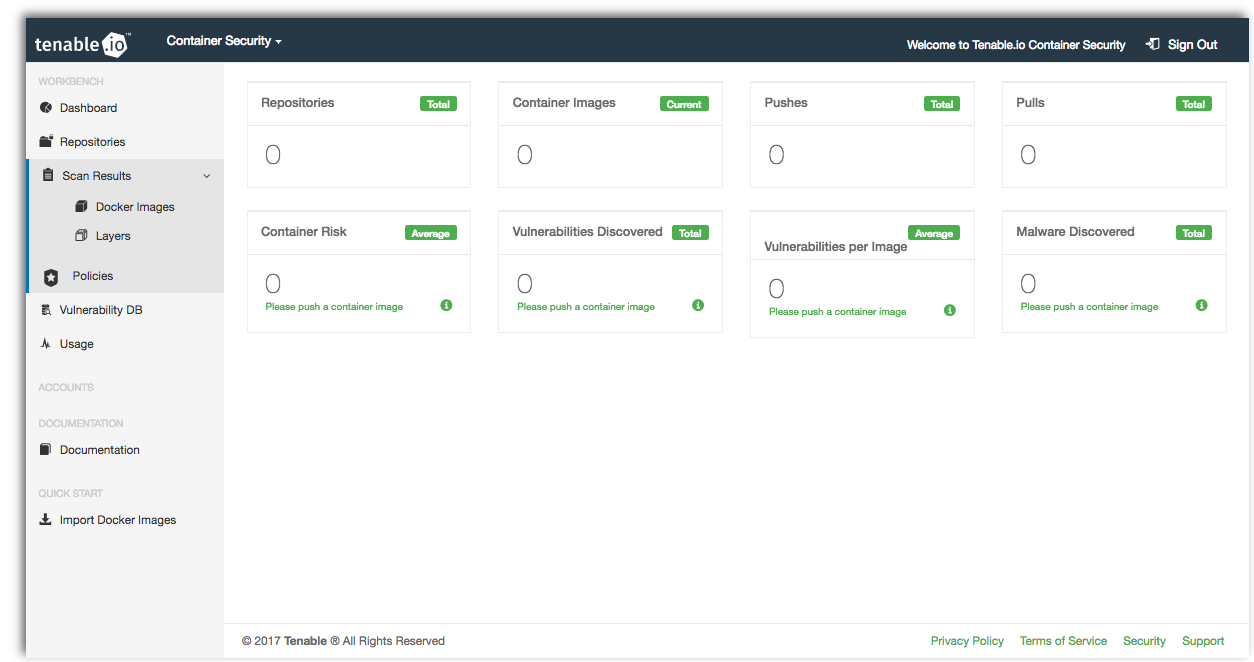
Once your trial has been activated, you will be redirected to the Tenable.io Container Security main page.
Pushing container images
You can easily push images to Tenable.io Container Security from any environment or platform within your network. To push images, start by logging in using your Tenable.io Container Security credentials from the host system.
$ docker login -u TENABLE_IO_CONTAINER_SECURITY_USERNAME -p TENABLE_IO_CONTAINER_SECURITY_PASSWORD registry.cloud.tenable.comTo get a complete list of your existing container images, enter the following:
$ docker imagesOnce you have identified the image you wish to upload, enter in the associated Docker Image ID, Repository name, Container image, and Tag. Note that using the tag switch is optional, and the system will use “latest” within the tag field by default.
$ docker tag <imageID>
registry.cloud.tenable.com/<repository>/<image>:<tag>Once tagged, you can push the container image up to registry.cloud.tenable.com.
$ docker push registry.cloud.tenable.com/<repository>/<image>:<tag>To close out of your session, use the docker logout command to remove login credentials from the host:
$ docker logout registry.cloud.tenable.comDashboards
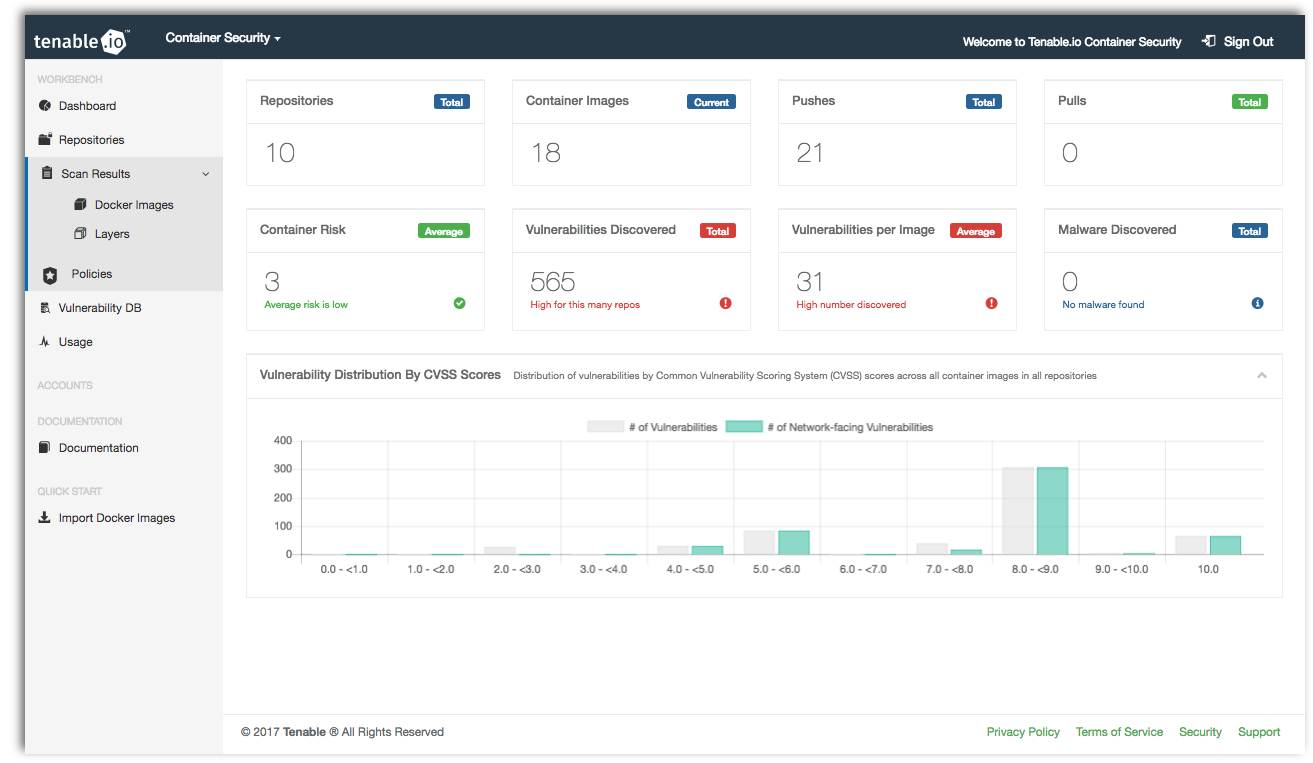
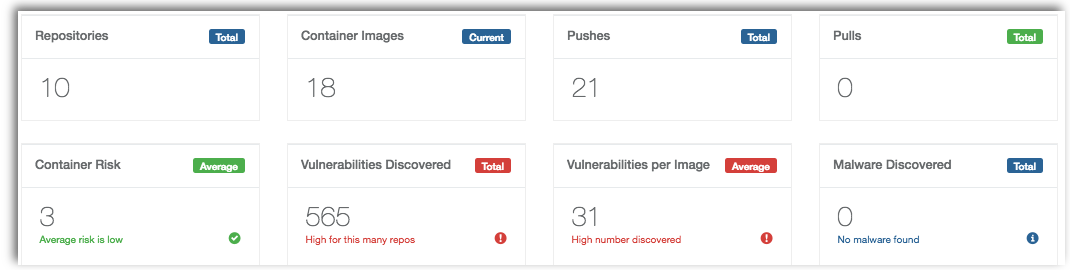
Dashboards provide management with complete visibility into your overall container security. Results include the number of images, vulnerabilities and malware discovered, enabling you to quickly determine which containers are at risk.
Repositories can be created manually or automatically pushed or pulled from an existing container registry. Tenable.io Container Security includes a repository index highlighting the number of images per repository, overall size, and the number of vulnerabilities or malware detected within that repository. You can easily drill down into any repository, image, or tag providing information on detected services, as well as vulnerabilities that may be present within the image.
Scan results for each container image include a list of when the image was last analyzed, overall risk score, and results in HTML, JSON and Nessus v2 file formats.
Layers
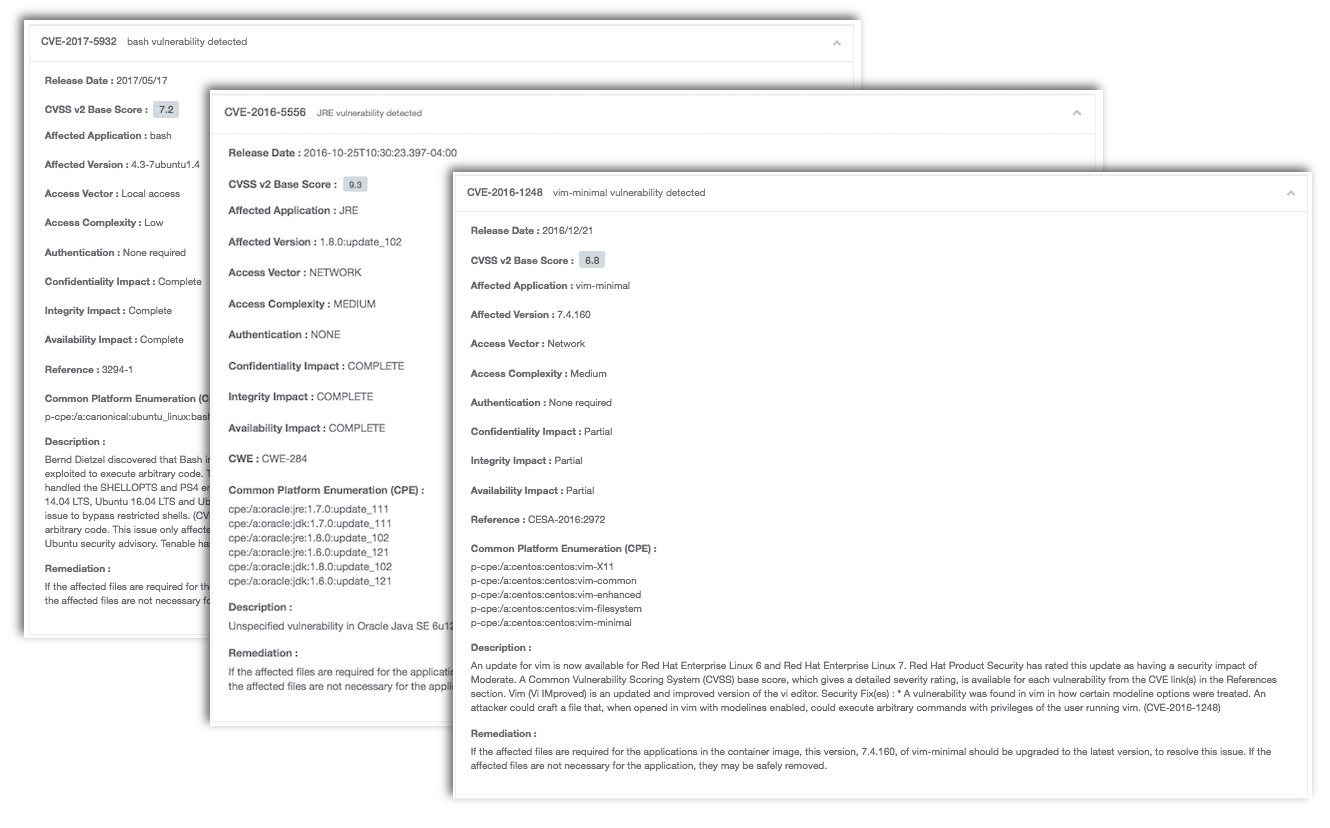
Tenable.io Container Security inventories and analyzes each layer within the container registry for vulnerabilities and malware. Scan results include information on the overall risk score, distribution of vulnerabilities by CVSS score, and a list of vulnerabilities by CVE. Use this information to help narrow down and remediate vulnerabilities before systems are deployed to production.
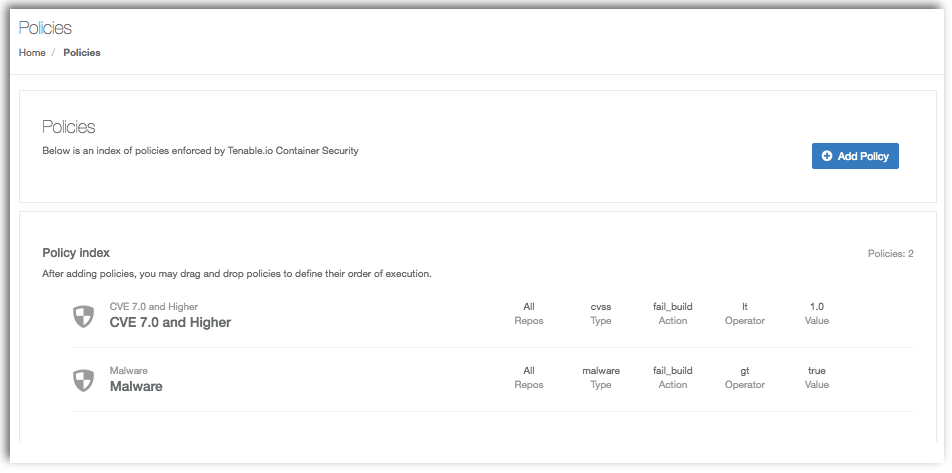
Policies
Tenable.io Container Security supports rules-based policy enforcement that helps you filter scan results and highlight specific vulnerability data relevant to your organization. Policies can be applied globally or to specific repositories that can highlight specific CVEs, CVSS values, or whether malware has been detected.
After adding rules that meet your organization's application security policies, you can organize the way rules are evaluated via drag and drop.
Scan results
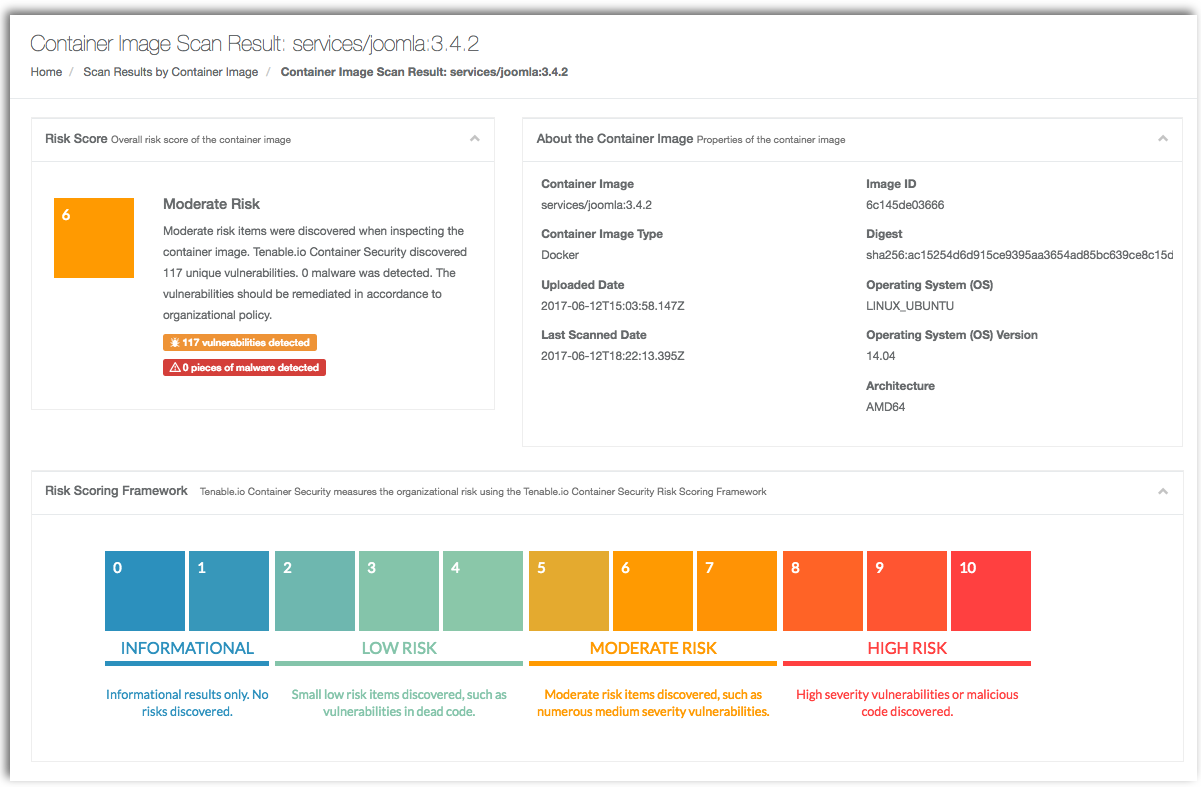
Results include an overall risk score and information about the container image, including the base operating system (OS) and version. For teams that want to scan for changes between development and production environments, results also include a unique SHA256 checksum for each individual image pushed to Tenable.io Container Security. Using the Tenable.io Container Security Risk Scoring Framework, vulnerabilities are measured to help you determine the risk to your environment.
Each container layer and associated checksum is included within the scan results, along with an inventory of packages within the container image. Results include detected CVE, CVSS base score, description of the vulnerability, and remediation details.
As container images are uploaded into Tenable.io Container Security, they are automatically scanned for vulnerabilities and malware. Once a vulnerability is identified, the product automatically rescans all stored container images against the new vulnerability, thus ensuring continuous protection.
For DevOps teams, Tenable.io Container Security provides integrations with common build systems such as Jenkins, Bamboo, Shippable, Travis CI and others, as well as with other continuous integration/continuous deployment tools used by software developers. This enables you to push images from your private registry into Tenable.io Container Security.
Learn more
Tenable is the only vulnerability management provider to offer integrated container security with Tenable.io Container Security.
Tenable.io Container Security integrates continuous integration and continuous deployment (CI/CD) systems to support and strength DevOps practices, as well as enterprise policy compliance.
Want to know more about Tenable.io Container Security?
- Read more about Tenable.io Container Security
- Try Tenable.io Container Security free for 60 days
Related Articles
- Container security
- Tenable.io
- Tenable.io Container Security